Directive Blogs
Computer viruses and malware have been around for a long time, and cybercriminals have always tried to package their malevolent doings under a veil of deception. One method that has been in place for a while now is called scareware. Often disguised as something that appears to want to help your computer, scareware will scam users into paying for a service that isn't beneficial.
Ever since the mid-1990s employees have been taking advantage of personal gadgets to help them get work done faster. Remember the PDAs and Palm Pilots from a decade and a half ago? Even though many companies weren't quick to establish policies to protect corporate data, tech savvy users were able to sync contacts, schedules, email, and company files to their mobile device. These days, mobile devices are in the hands of many more users, but there are ways to provide security without sacrificing your employees rights to their personal device.
Last time, we blogged about whether or not social media and personal Internet use was a bottleneck for employee productivity. Let's not look at the Internet as a fundamental time-waster or a necessary evil. After all, the Internet has changed the way companies do business. This time we're going to investigate if your Internet is keeping up with your company.
Internet privacy is no new issue. Between malicious hackers trying to breach private information, governments trying to regulate it, and organizations trying to track as many metrics as they can, the Internet continues to chug along for the most part just fine. Are YOU concerned about Internet privacy?
We can never stress enough to our clients how important their data is. There are plenty of ways data can become lost, but the one scenario that nobody ever likes to talk about is internal data theft. That's right; businesses can suffer from their own employees stealing data. Now, this doesn't mean that all or any part of your staff is plotting to expose company secrets or distribute your leads to competitors, but a few precautions can be taken to just ensure that it never happens.
As you may know, Sony's online gaming service, the Playstation Network, has been getting a lot of media coverage lately due to a major attack by hackers last month. Sony is a massive global company with billions of dollars and stockholders and spans multiple industries, but even a giant can teach us all a lesson that relates to our comparably small-fry organizations.
 Having strong passwords for your online accounts is very important, but sometimes you may want a little more protection in the event your password gets stolen or someone forces their way through it. If you use Google's Gmail service, you can set up your account, then you will need two forms of authentication to get into your email.
Having strong passwords for your online accounts is very important, but sometimes you may want a little more protection in the event your password gets stolen or someone forces their way through it. If you use Google's Gmail service, you can set up your account, then you will need two forms of authentication to get into your email.
Directive has had the pleasure of working with David Mann for over 10 years. David owns Alta Log Homes in Upstate NY. Alta is a leading manufacturer of Log Homes. David is an expert in building Green, Energy Star dream homes and a great guy. His website is http://www.altaloghomes.com. We set him up with the Ultimate Social Media Rig a few months ago along with some coaching services to get him started. He's been pretty religious about posting and using it. He sent me an email asking what recommendations I'd have to get more out of it now that he's "warmed up" and has a little more experience with Social Media.
Is your organization using the latest technology solutions? If so, that’s great--you’ve taken the first step toward achieving maximum productivity and efficiency. However, you need to realize that no technology solution comes without its quirks that need to be addressed. Here are two ways that your new technology solutions could potentially be putting your business’s infrastructure at risk.
Security has never been easy for any business that deals with sensitive information. Nowadays, even a small business that uses an Internet connection has to worry about hackers and malware of all types. This is especially problematic for small healthcare offices that need to keep sensitive information secure and safe from online threats.
Has your business dealt with a phishing attack? If not, consider yourself lucky. There has been a massive spike in phishing attacks as hackers are aggressively going after organizations and the personal identifiable information they hold. These attacks are just not focused on typical businesses either, they are going after organizations that provide public goods. One place that has become a major target for hackers (and phishing attacks) are schools.
When a hacker tries to infiltrate your network, they are doing so with a purpose in mind. Usually they are looking for specific information, like account credentials, personal information, or files that can be used to blackmail victims. Regardless, we’ll go over what a hacker can do with the information that they collect from you, and how you can best protect it from them.
Whether you’re just a small business looking to get operations moving in your chosen location, or you’re an enterprise with multiple offices across the country, one thing is universally the same: you need IT support in some capacity. As more technology is added to networks of all sizes and complexities, the need to manage this technology improves. Thankfully, you don’t necessarily have to go at it alone--you have third-party outsourcing at your disposal, which can save you both time and money in the long run.
!--
How to Anonymously Browse the Internet
--> Some places on the Internet are only suitable for secret browsing. Maybe you're shopping for a present and don't want your links to show in your browsing history, or maybe you don't want the customized ads to reflect a private interest. Whatever your reason is for wanting to anonymously browse the web, here's how you do it.
Some places on the Internet are only suitable for secret browsing. Maybe you're shopping for a present and don't want your links to show in your browsing history, or maybe you don't want the customized ads to reflect a private interest. Whatever your reason is for wanting to anonymously browse the web, here's how you do it.
Despite the increasingly vast trust we put into the Internet to keep our personal and business information safe and secure, many users take their passwords very lightly. In an analysis studying over 32 million passwords from RockYou, a company that develops software for social networks, it's been discovered just how little effort is put in to keep things secure. The results are shocking.
 Hackers have always gone after industries that are profitable, or hold sensitive information that can be lucrative when sold under the table. As such, retailers that accumulate financial credentials are often hit by hacks. The entertainment industry is no different, and hackers continue to grow craftier in their pursuit of wealth and power. Not even Steam, the PC gamer’s most valuable software solution, is safe from the dangers of hacking attacks.
Hackers have always gone after industries that are profitable, or hold sensitive information that can be lucrative when sold under the table. As such, retailers that accumulate financial credentials are often hit by hacks. The entertainment industry is no different, and hackers continue to grow craftier in their pursuit of wealth and power. Not even Steam, the PC gamer’s most valuable software solution, is safe from the dangers of hacking attacks.
 There’s a reason why IT professionals think that the Internet of things is a major security discrepancy. Around 5.5 million new devices are being connected to the Internet every day, and are giving security experts a run for their money. The Internet of Things and its devices could potentially become a security hazard for businesses that aren’t prepared to protect their assets from hacks.
There’s a reason why IT professionals think that the Internet of things is a major security discrepancy. Around 5.5 million new devices are being connected to the Internet every day, and are giving security experts a run for their money. The Internet of Things and its devices could potentially become a security hazard for businesses that aren’t prepared to protect their assets from hacks.
 Apple has been a major contributor to advancements in computing over the past few decades. Their iPhone was the first commercially available smartphone, and they continue to innovate with new and exciting consumer technology. However, one of Apple’s most recent decisions might be one of the most important for today’s cyber security world.
Apple has been a major contributor to advancements in computing over the past few decades. Their iPhone was the first commercially available smartphone, and they continue to innovate with new and exciting consumer technology. However, one of Apple’s most recent decisions might be one of the most important for today’s cyber security world.
 While they might seem like glorified toys for adults, drones are fantastic tools that can help people take some breathtaking photos and videos of their local scenery. Unfortunately, as is the case with most good technology, there are people out there who want to use them for nefarious purposes. This leads authorities to a tough question: how do you knock an illegal or dangerous drone out of the sky without harming those down below? The answer is simple: eagles.
While they might seem like glorified toys for adults, drones are fantastic tools that can help people take some breathtaking photos and videos of their local scenery. Unfortunately, as is the case with most good technology, there are people out there who want to use them for nefarious purposes. This leads authorities to a tough question: how do you knock an illegal or dangerous drone out of the sky without harming those down below? The answer is simple: eagles.
 Firewalls are one of the most common IT security measures on the market today, and for good reason. They act as the first line of defense against any incoming threats, and without them, your organization would have to deal with one data breach after another. Of course, that’s only if you’re taking advantage of a proper firewall; if not, you should seriously consider doing so as soon as possible.
Firewalls are one of the most common IT security measures on the market today, and for good reason. They act as the first line of defense against any incoming threats, and without them, your organization would have to deal with one data breach after another. Of course, that’s only if you’re taking advantage of a proper firewall; if not, you should seriously consider doing so as soon as possible.
 Whenever hackers show themselves, they always spell trouble. Whether it’s stealing credentials or completely taking over someone’s computer, a hacker has a plethora of targets and methods that can be irritating for the average PC user, or business executive. In fact, hackers are so crafty that they can even hack into hospital equipment.
Whenever hackers show themselves, they always spell trouble. Whether it’s stealing credentials or completely taking over someone’s computer, a hacker has a plethora of targets and methods that can be irritating for the average PC user, or business executive. In fact, hackers are so crafty that they can even hack into hospital equipment.
 Password security is a common problem that businesses that take their cybersecurity seriously have to deal with on a regular basis. Passwords need to be complex and difficult to guess, but easy to remember at the same time. Unfortunately, these two goals don’t go hand-in-hand, and as such, users often have to sacrifice one for the other. The “passpoem” is a concept born to resolve this issue, though it takes a pretty roundabout path of doing so.
Password security is a common problem that businesses that take their cybersecurity seriously have to deal with on a regular basis. Passwords need to be complex and difficult to guess, but easy to remember at the same time. Unfortunately, these two goals don’t go hand-in-hand, and as such, users often have to sacrifice one for the other. The “passpoem” is a concept born to resolve this issue, though it takes a pretty roundabout path of doing so.
 Have you ever wondered what hackers do with all of the data they steal on a regular basis? Sure, they could go public with it like they did with the Ashley Madison and Sony hacks, or they could sell it and make some quick cash. Credentials like passwords, usernames, Social Security numbers, and more, can be sold for top dollar in illegal markets, but how much can your identity go for?
Have you ever wondered what hackers do with all of the data they steal on a regular basis? Sure, they could go public with it like they did with the Ashley Madison and Sony hacks, or they could sell it and make some quick cash. Credentials like passwords, usernames, Social Security numbers, and more, can be sold for top dollar in illegal markets, but how much can your identity go for?
 We all know that Windows 10 is the hot new operating system released by Microsoft this past July, with slick new features and (gasp!) the Start menu. We’ve been writing a lot of articles about how great and functional the new operating system is. Keep in mind that Windows 10 is a great operating system, but you should also take note of these four shortcomings when considering whether you should immediately upgrade or not.
We all know that Windows 10 is the hot new operating system released by Microsoft this past July, with slick new features and (gasp!) the Start menu. We’ve been writing a lot of articles about how great and functional the new operating system is. Keep in mind that Windows 10 is a great operating system, but you should also take note of these four shortcomings when considering whether you should immediately upgrade or not.
 Agent Chrome is a pretty well-known guy in Google City. In fact, you could say he was the top of his class at Browser University, and everybody who is anybody knows who he is. When on the job, Agent Chrome sometimes needs to lay low and avoid the prying eyes of the masses around him. And this particular operation, rightfully dubbed “Incognito,” is one such occasion.
Agent Chrome is a pretty well-known guy in Google City. In fact, you could say he was the top of his class at Browser University, and everybody who is anybody knows who he is. When on the job, Agent Chrome sometimes needs to lay low and avoid the prying eyes of the masses around him. And this particular operation, rightfully dubbed “Incognito,” is one such occasion.
 With so much nasty content just begging to get viewed on the Internet, it’s understandable why a content filter needs to be integrated into your company’s web viewing protocol. Still, it should be understood that your content filter isn’t going to keep all questionable content away from prying eyes. Therefore, the only way you can really know with certainty that your Internet users aren’t doing anything sketchy is to actively monitor their activity, and check for any suspicious websites.
With so much nasty content just begging to get viewed on the Internet, it’s understandable why a content filter needs to be integrated into your company’s web viewing protocol. Still, it should be understood that your content filter isn’t going to keep all questionable content away from prying eyes. Therefore, the only way you can really know with certainty that your Internet users aren’t doing anything sketchy is to actively monitor their activity, and check for any suspicious websites.
 You know the saying “you can never be too careful”? It’s always said by the person who understands the value of proceeding with caution, and understands that all it takes is a moment to lose everything. In some cases, it could be your workplace dignity, but in others, you need to cover your tracks to prevent hackers and other miscreants from performing the unspeakable: messing with your computer while you’re away from it momentarily.
You know the saying “you can never be too careful”? It’s always said by the person who understands the value of proceeding with caution, and understands that all it takes is a moment to lose everything. In some cases, it could be your workplace dignity, but in others, you need to cover your tracks to prevent hackers and other miscreants from performing the unspeakable: messing with your computer while you’re away from it momentarily.
 With revelations coming to light on how governments are monitoring citizen's Internet usage, many people are concerned about their online privacy. Most of us are so dependent upon technology that it's almost impossible to totally disconnect off the grid, yet there are a few tricks you can use to browse the Web with anonymity.
With revelations coming to light on how governments are monitoring citizen's Internet usage, many people are concerned about their online privacy. Most of us are so dependent upon technology that it's almost impossible to totally disconnect off the grid, yet there are a few tricks you can use to browse the Web with anonymity.
 Since the dawn of the computing age, hackers have taken advantage of all sorts of tactics in order to crack systems and ruin lives. With the Internet of Things bringing connected devices from all over the place into the mix, there are more opportunities than ever to take advantage of unsuspecting users. In fact, even car computers are capable of being hacked.
Since the dawn of the computing age, hackers have taken advantage of all sorts of tactics in order to crack systems and ruin lives. With the Internet of Things bringing connected devices from all over the place into the mix, there are more opportunities than ever to take advantage of unsuspecting users. In fact, even car computers are capable of being hacked.
 In this day and age, a password isn’t enough to keep your accounts secure from attempted hacks. Passwords can be cracked as easily as anything. A lot of businesses have moved to two-factor authentication in order to preserve their data. There are several ways of using this for your business, but a new startup called BioCatch is developing an authentication procedure which looks at your mouse activity.
In this day and age, a password isn’t enough to keep your accounts secure from attempted hacks. Passwords can be cracked as easily as anything. A lot of businesses have moved to two-factor authentication in order to preserve their data. There are several ways of using this for your business, but a new startup called BioCatch is developing an authentication procedure which looks at your mouse activity.
 It seems like we can’t go on the Internet without reading about some sort of data breach. Sometimes they’re caused by poor security measures, like lack of data encryption or two-factor authentication; other times, it’s because of lackluster password security. Despite the antiquity of the username and password, they’re staples in the modern office. Thus, it’s important that they’re as secure as possible at all times.
It seems like we can’t go on the Internet without reading about some sort of data breach. Sometimes they’re caused by poor security measures, like lack of data encryption or two-factor authentication; other times, it’s because of lackluster password security. Despite the antiquity of the username and password, they’re staples in the modern office. Thus, it’s important that they’re as secure as possible at all times.
 Normally in cybersecurity, we hear about hacking attacks and immediately sympathize with the victim. It’s usually an individual or a business that suffers the most; yet, a recent trend is showing that hackers are lashing out at one another in response to certain threats. In response to a hack from the cyberespionage group Naikon, another group, Hellsing, retaliated with their own attack.
Normally in cybersecurity, we hear about hacking attacks and immediately sympathize with the victim. It’s usually an individual or a business that suffers the most; yet, a recent trend is showing that hackers are lashing out at one another in response to certain threats. In response to a hack from the cyberespionage group Naikon, another group, Hellsing, retaliated with their own attack.
 How much thought have you put into selecting your debit card PIN? If you’ve not put any thought into your PIN, then it’s likely the case that you’ve picked a number that’s easy to remember or even one that’s associated with something personal. Fact: Taking time to pick random and hard-to-remember numbers greatly improves PIN security.
How much thought have you put into selecting your debit card PIN? If you’ve not put any thought into your PIN, then it’s likely the case that you’ve picked a number that’s easy to remember or even one that’s associated with something personal. Fact: Taking time to pick random and hard-to-remember numbers greatly improves PIN security.
 We always talk about protecting your computers and servers from outside threats, but what about protecting your smartphones? There isn’t much difference between a smartphone and a computer. They both function in very similar ways with access to a variety of apps, social media, and browsers. Your smartphone could hold much more valuable data than just contacts or text messages.
We always talk about protecting your computers and servers from outside threats, but what about protecting your smartphones? There isn’t much difference between a smartphone and a computer. They both function in very similar ways with access to a variety of apps, social media, and browsers. Your smartphone could hold much more valuable data than just contacts or text messages.
 Changing your password is a pain. After you’ve gone several months with the same one, it can be difficult to remember your new password. Despite this, it’s always recommended that you change your passwords often. Unfortunately, when you change all of your passwords often, it’s even easier to forget them. Instead of using a post-it note on your monitor, you should instead try using a password manager.
Changing your password is a pain. After you’ve gone several months with the same one, it can be difficult to remember your new password. Despite this, it’s always recommended that you change your passwords often. Unfortunately, when you change all of your passwords often, it’s even easier to forget them. Instead of using a post-it note on your monitor, you should instead try using a password manager.
 Today’s headlines are dominated by stories of major companies getting hacked, making the average computer user feel uneasy about their security. If you’re solely dependent on a measly password to protect you from hackers, then you’ve got good reason to worry. Adding a second layer of verification is an easy way to protect your information. Here’s how to set up 2-Step Verification for your Google account.
Today’s headlines are dominated by stories of major companies getting hacked, making the average computer user feel uneasy about their security. If you’re solely dependent on a measly password to protect you from hackers, then you’ve got good reason to worry. Adding a second layer of verification is an easy way to protect your information. Here’s how to set up 2-Step Verification for your Google account.
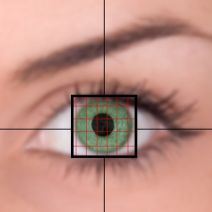 Humans are always trying to improve security protocols that can protect against increasingly advanced online threats. Unfortunately, the threats only grow stronger in response, and the war against malicious online activity rages on. Biometrics are security measures that are growing in popularity, but are expensive and difficult to integrate. Now, the US military is funding a campaign to make it more readily available to end users.
Humans are always trying to improve security protocols that can protect against increasingly advanced online threats. Unfortunately, the threats only grow stronger in response, and the war against malicious online activity rages on. Biometrics are security measures that are growing in popularity, but are expensive and difficult to integrate. Now, the US military is funding a campaign to make it more readily available to end users.
 We see a lot of password-bashing these days, and some people have lost faith in them as a security measure. But, unfortunately, a lot of the blame for this lies in human memory. We just don’t pick passwords that are strong enough. In fact, a mind-numbing one in 20 people still use “password” to keep their information safe.
We see a lot of password-bashing these days, and some people have lost faith in them as a security measure. But, unfortunately, a lot of the blame for this lies in human memory. We just don’t pick passwords that are strong enough. In fact, a mind-numbing one in 20 people still use “password” to keep their information safe.
 The busy business owner keeps sensitive work-related information stored on their mobile device. If he lost the device, it could have disastrous results, especially if the device were to fall into the hands of an experienced hacker or competitor. Just in case, it’s a best practice to always lock your mobile devices. How do you choose the Android lock feature which is right for your unique needs?
The busy business owner keeps sensitive work-related information stored on their mobile device. If he lost the device, it could have disastrous results, especially if the device were to fall into the hands of an experienced hacker or competitor. Just in case, it’s a best practice to always lock your mobile devices. How do you choose the Android lock feature which is right for your unique needs?
 People dial 911 when they’re in some sort of trouble or in the event of an emergency. If not for the hotline, who knows how many lives could be lost daily. Sometimes, however, help doesn’t come, even when dispatchers have received the call and responded. This generally isn’t the fault of the dispatchers, but rather the criminals who have undermined the rescue efforts thanks to some unorthodox hacking.
People dial 911 when they’re in some sort of trouble or in the event of an emergency. If not for the hotline, who knows how many lives could be lost daily. Sometimes, however, help doesn’t come, even when dispatchers have received the call and responded. This generally isn’t the fault of the dispatchers, but rather the criminals who have undermined the rescue efforts thanks to some unorthodox hacking.
 When a virus infects your computer, you may not know about it until it’s too late. Like a biological virus, the damage it does to your system can be minimized if it’s caught early on. Stopping a computer virus early is possible if you know what symptoms to look for. Is your PC infected? Here are four signs you’ve been hacked.
When a virus infects your computer, you may not know about it until it’s too late. Like a biological virus, the damage it does to your system can be minimized if it’s caught early on. Stopping a computer virus early is possible if you know what symptoms to look for. Is your PC infected? Here are four signs you’ve been hacked.
 In the past, we’ve been known to go into detail about threats, vulnerabilities, and how to protect your business while online. Distributed denial of service (DDoS) attacks aren’t new in the technology world, but notorious hacking group Lizard Squad has somehow managed to take out Internet service for much of Sweden with a faulty DDoS attack; an unprecedented feat, especially for a ragtag group of irate gamers.
In the past, we’ve been known to go into detail about threats, vulnerabilities, and how to protect your business while online. Distributed denial of service (DDoS) attacks aren’t new in the technology world, but notorious hacking group Lizard Squad has somehow managed to take out Internet service for much of Sweden with a faulty DDoS attack; an unprecedented feat, especially for a ragtag group of irate gamers.
 The holiday shopping season is upon us and more people are choosing to shop from the comforts of their home PC or mobile device rather than fight the crowds. Shopping online is super convenient, but it’s not without the risk of identity theft. The best way to protect your digital shopping cart from hackers is to know how to safely shop online. We’ll show you how.
The holiday shopping season is upon us and more people are choosing to shop from the comforts of their home PC or mobile device rather than fight the crowds. Shopping online is super convenient, but it’s not without the risk of identity theft. The best way to protect your digital shopping cart from hackers is to know how to safely shop online. We’ll show you how.
 This subject isn’t very interesting outside of hospital administrators… or for hospital administrators, but there’s no denying that healthcare is one of the most important industries in our society today; and one that is having a technology overhaul at present. The influx of cheaper and more powerful technology is surely going to be a driving force for healthcare in the 21st century. Under the Health Information Technology for Economic and Clinical Health Act (HITECH), the United States government has followed the lead of other Western nations in forcing entities to upgrade their healthcare practice’s information technology for the betterment of patients, insurers, and health care providers.
This subject isn’t very interesting outside of hospital administrators… or for hospital administrators, but there’s no denying that healthcare is one of the most important industries in our society today; and one that is having a technology overhaul at present. The influx of cheaper and more powerful technology is surely going to be a driving force for healthcare in the 21st century. Under the Health Information Technology for Economic and Clinical Health Act (HITECH), the United States government has followed the lead of other Western nations in forcing entities to upgrade their healthcare practice’s information technology for the betterment of patients, insurers, and health care providers.
 With all the attention given today to scams over the Internet, it’s easy to neglect classic scams like con artists using the phone to exploit people. You may think that you’re safe because you have a smartphone with caller ID, but thanks to new spoofing tactics, reliable defenses like caller ID can no longer be depended upon to safeguard you from telemarketer scum.
With all the attention given today to scams over the Internet, it’s easy to neglect classic scams like con artists using the phone to exploit people. You may think that you’re safe because you have a smartphone with caller ID, but thanks to new spoofing tactics, reliable defenses like caller ID can no longer be depended upon to safeguard you from telemarketer scum.
 The world of online currency is a strange, bizarre realm. While it’s designed for online transactions, it has gone from the somewhat useful (Bitcoin) to just plain silly (Dogecoin). However, there’s now an anonymous cryptocurrency available for use called Darkcoin, which attempts to make online transactions more difficult to trace.
The world of online currency is a strange, bizarre realm. While it’s designed for online transactions, it has gone from the somewhat useful (Bitcoin) to just plain silly (Dogecoin). However, there’s now an anonymous cryptocurrency available for use called Darkcoin, which attempts to make online transactions more difficult to trace.
 When you were a kid, did you ever ask your parents for a cool new toy only to have your request denied because you were in the habit of breaking everything? Your parents would point out your destructive habit and tell you, "This is why we can't have nice things." As an adult, the coolest toy is the Internet and hackers want to break it.
When you were a kid, did you ever ask your parents for a cool new toy only to have your request denied because you were in the habit of breaking everything? Your parents would point out your destructive habit and tell you, "This is why we can't have nice things." As an adult, the coolest toy is the Internet and hackers want to break it.
 There's nothing quite like the feeling of getting scammed, and the scammers of today love using technology to rip you off and leave you with that sinking scammy feeling. The best way to avoid scams is to be proactive and know what to look for. New to your list of scams to be on the look out for are fake apps.
There's nothing quite like the feeling of getting scammed, and the scammers of today love using technology to rip you off and leave you with that sinking scammy feeling. The best way to avoid scams is to be proactive and know what to look for. New to your list of scams to be on the look out for are fake apps.
 2014 has been a year of technological advancement, but with any kind of advances such as these, there will always be those who want to steal the work of others. According to the Identity Theft Resource Center and , as of March this year, there have been 204 instances of data breaches this year alone. These affected companies are perfect examples of why web protection is important. Directive can provide you with this protection and peace of mind. Here are a few of the more unbelievable breaches, most of which could have been easily avoided.
2014 has been a year of technological advancement, but with any kind of advances such as these, there will always be those who want to steal the work of others. According to the Identity Theft Resource Center and , as of March this year, there have been 204 instances of data breaches this year alone. These affected companies are perfect examples of why web protection is important. Directive can provide you with this protection and peace of mind. Here are a few of the more unbelievable breaches, most of which could have been easily avoided.
 On April 7th, a new bug on the Internet was discovered that's putting millions of users' personal data at risk. Given the name "Heartbleed bug," it's capable of allowing infiltrators to collect information while you are securely browsing a SSL/TLS website. Since SSL/TLS is so widely used, it's very probably that your personal data is at risk.
On April 7th, a new bug on the Internet was discovered that's putting millions of users' personal data at risk. Given the name "Heartbleed bug," it's capable of allowing infiltrators to collect information while you are securely browsing a SSL/TLS website. Since SSL/TLS is so widely used, it's very probably that your personal data is at risk.
 You're likely familiar with the various ways that hackers can steal your identity, but you may not be familiar with how hackers anonymously buy and sell people's personal information to interested parties. This is done through online ID theft services and a December hearing before the U.S. Senate highlights how one service was selling personal records on more than 200 million Americans!
You're likely familiar with the various ways that hackers can steal your identity, but you may not be familiar with how hackers anonymously buy and sell people's personal information to interested parties. This is done through online ID theft services and a December hearing before the U.S. Senate highlights how one service was selling personal records on more than 200 million Americans!
 We live in a time where information technology has touched every facet of life. It would be a fair bet to assume that, at this point, it is more commonplace than a trend. We are inundated with Internet-connected computer systems in every aspect of life. We use automated tellers to do our banking, most major retailers have automated checkouts to supplement the work staff they have in place, and even your Grandma uses Gmail. With this technology saturated into the culture, there are many pragmatic uses that are just now being discovered and implemented. Nowhere is this more true than in the health care industry.
We live in a time where information technology has touched every facet of life. It would be a fair bet to assume that, at this point, it is more commonplace than a trend. We are inundated with Internet-connected computer systems in every aspect of life. We use automated tellers to do our banking, most major retailers have automated checkouts to supplement the work staff they have in place, and even your Grandma uses Gmail. With this technology saturated into the culture, there are many pragmatic uses that are just now being discovered and implemented. Nowhere is this more true than in the health care industry.
 Tech savvy individuals and businesses alike have moved away from traditional Internet browsers such as Microsoft's Internet Explorer and Apple's Safari to Google's Chrome browser. After all, many people enjoy having a simplistic, yet powerful web browser that easily integrates it's Google Docs tools and Gmail email service. However, users may want to think twice about using the browser now that a new YouTube video has surfaced entitled "Chrome Bug Lets Sites Listen to Your Conversations." In the video, user Tal Ater walks through a very dangerous exploit that allows anyone to access your microphone through Google's voice recognition software embedded in Chrome.
Tech savvy individuals and businesses alike have moved away from traditional Internet browsers such as Microsoft's Internet Explorer and Apple's Safari to Google's Chrome browser. After all, many people enjoy having a simplistic, yet powerful web browser that easily integrates it's Google Docs tools and Gmail email service. However, users may want to think twice about using the browser now that a new YouTube video has surfaced entitled "Chrome Bug Lets Sites Listen to Your Conversations." In the video, user Tal Ater walks through a very dangerous exploit that allows anyone to access your microphone through Google's voice recognition software embedded in Chrome.
 With the NSA and Edward Snowden making headlines around the world, it's enough to make any user of the Internet think twice about online security and wonder if they are being monitored or not. Google Search has been a popular hub for third party monitoring, which makes Internet users ask, "Is there a more secure search engine available?" There is with DuckDuckGo.
With the NSA and Edward Snowden making headlines around the world, it's enough to make any user of the Internet think twice about online security and wonder if they are being monitored or not. Google Search has been a popular hub for third party monitoring, which makes Internet users ask, "Is there a more secure search engine available?" There is with DuckDuckGo.
 You may think that the standard security policies that come with your email account can protect you from hackers. It's an easy mistake to make, but the truth of the matter is that, if a hacker really wants access to an account, then they will employ every tactic possible to get it, which can make standard password security measures woefully inadequate.
You may think that the standard security policies that come with your email account can protect you from hackers. It's an easy mistake to make, but the truth of the matter is that, if a hacker really wants access to an account, then they will employ every tactic possible to get it, which can make standard password security measures woefully inadequate.
 The value of your email account cannot be understated. You may think less of your email inbox because there are so many other ways to digitally communicate, but to a hacker, your email is a goldmine of valuable information. You may use your email less than ever before, but that doesn't mean you can neglect email security.
The value of your email account cannot be understated. You may think less of your email inbox because there are so many other ways to digitally communicate, but to a hacker, your email is a goldmine of valuable information. You may use your email less than ever before, but that doesn't mean you can neglect email security.
 On December 3, 2013, security company Trustwave discovered over two million stolen user passwords for popular online services like Facebook, LinkedIn, Google, Twitter, Yahoo, and 93,000 other websites. There's a high probability that you use one of the services affected by the hack. Is your personal information compromised?
On December 3, 2013, security company Trustwave discovered over two million stolen user passwords for popular online services like Facebook, LinkedIn, Google, Twitter, Yahoo, and 93,000 other websites. There's a high probability that you use one of the services affected by the hack. Is your personal information compromised?
 The world you do business in is a pretty dangerous and messed up place, and things always seem to be getting worse. Thankfully, security technology is improving, which helps offset the risks of living in a perilous world. You can take advantage of these security improvements by installing intelligent surveillance cameras for your business.
The world you do business in is a pretty dangerous and messed up place, and things always seem to be getting worse. Thankfully, security technology is improving, which helps offset the risks of living in a perilous world. You can take advantage of these security improvements by installing intelligent surveillance cameras for your business.
 Recently, Adobe sent out e-mails and letters to users notifying everyone of a security breach. "The attackers may have obtained access to your Adobe ID and encrypted password." The obvious question here is, "How do I protect myself and my business from such attacks?" The unfortunate answer is you can't, but you can marginalize the impact by taking some common sense measures.
Recently, Adobe sent out e-mails and letters to users notifying everyone of a security breach. "The attackers may have obtained access to your Adobe ID and encrypted password." The obvious question here is, "How do I protect myself and my business from such attacks?" The unfortunate answer is you can't, but you can marginalize the impact by taking some common sense measures.
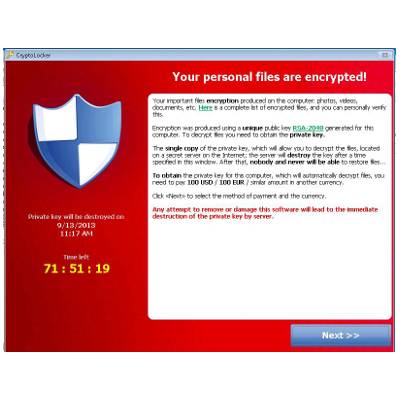 On September 10th, 2013, a new ransomware known as Trojan:Win32/Crilock.A began attacking computers all over the Internet, locking users out of their PCs and putting sensitive information at risk. If your computer gets it, then you're in for a world of hurt. Here are the details on what this virus does and what you can do to prevent it.
On September 10th, 2013, a new ransomware known as Trojan:Win32/Crilock.A began attacking computers all over the Internet, locking users out of their PCs and putting sensitive information at risk. If your computer gets it, then you're in for a world of hurt. Here are the details on what this virus does and what you can do to prevent it.
 If you use a smartphone to take personal pictures and post them to the Internet, then you may unknowingly be posting more about yourself than you want to, like where and when the picture was taken. This information in the hands of the wrong person can lead to dangerous consequences, like theft of your property, your identity, or even kidnapping.
If you use a smartphone to take personal pictures and post them to the Internet, then you may unknowingly be posting more about yourself than you want to, like where and when the picture was taken. This information in the hands of the wrong person can lead to dangerous consequences, like theft of your property, your identity, or even kidnapping.
 With an increase in Distributed Denial of Service (DDOS) attacks and packet flooding volume, its evident that hackers are using compromised web servers for their malicious activities. By infecting servers, these dastardly infiltrators create a Zombie command-and-control center to direct their malicious activities from.
With an increase in Distributed Denial of Service (DDOS) attacks and packet flooding volume, its evident that hackers are using compromised web servers for their malicious activities. By infecting servers, these dastardly infiltrators create a Zombie command-and-control center to direct their malicious activities from.
 If you have been following international news headlines with stories like WikiLeaks spreading confidential documents, and recent revelations about a US surveillance scandal, it kind of feels like we are in the middle of Spy vs. Spy. As nations look for stronger security solutions to protect themselves, Russia is looking to older technology to keep their communications safe.
If you have been following international news headlines with stories like WikiLeaks spreading confidential documents, and recent revelations about a US surveillance scandal, it kind of feels like we are in the middle of Spy vs. Spy. As nations look for stronger security solutions to protect themselves, Russia is looking to older technology to keep their communications safe.
 Many businesses are discovering how great it is for employees to use their personal devices to accomplish work. BYOD has been proven to improve productivity and worker satisfaction; but like so many great things, these BYOD benefits are in danger of being shut down as employers are becoming concerned about being sued. How can you still benefit from BYOD while being protected from lawsuits?
Many businesses are discovering how great it is for employees to use their personal devices to accomplish work. BYOD has been proven to improve productivity and worker satisfaction; but like so many great things, these BYOD benefits are in danger of being shut down as employers are becoming concerned about being sued. How can you still benefit from BYOD while being protected from lawsuits?
 We often view hackers as creeps who are bent on spreading viruses to disrupt everyone's lives, perhaps for the sake of anarchy or some extreme ideology. But when it comes down to it, most hackers are in it for the money and are just trying to make a quick buck. In fact, hacking groups may even be more organized than your business!
We often view hackers as creeps who are bent on spreading viruses to disrupt everyone's lives, perhaps for the sake of anarchy or some extreme ideology. But when it comes down to it, most hackers are in it for the money and are just trying to make a quick buck. In fact, hacking groups may even be more organized than your business!
 Driving a powerful car can be an exhilarating experience, but if you have no idea what you're doing, it can be dangerous. This is why governments require drivers to pass a safety class before they can speed down the road encased in steel and glass. The Internet is also a powerful tool that can be exciting, beneficial, and dangerous.
Driving a powerful car can be an exhilarating experience, but if you have no idea what you're doing, it can be dangerous. This is why governments require drivers to pass a safety class before they can speed down the road encased in steel and glass. The Internet is also a powerful tool that can be exciting, beneficial, and dangerous.
 You can't log onto your online account if you're dead, and unless you have your password clearly marked on a sticky note, then nobody else will be able to either. While the Internet is a great distraction to keep us from pondering our mortality, the issue of post-mortem social media forces us to face death by preparing a digital will.
You can't log onto your online account if you're dead, and unless you have your password clearly marked on a sticky note, then nobody else will be able to either. While the Internet is a great distraction to keep us from pondering our mortality, the issue of post-mortem social media forces us to face death by preparing a digital will.
 As smartphone ownership continues to rise (175 million cellphones sold last year in the US), so too does smartphone theft. Take San Francisco, CA as an example, half of all robberies reported last year were phone-related. To help curb this trend, crime fighting agencies are seeking help from phone manufacturers in developing a smartphone kill switch.
As smartphone ownership continues to rise (175 million cellphones sold last year in the US), so too does smartphone theft. Take San Francisco, CA as an example, half of all robberies reported last year were phone-related. To help curb this trend, crime fighting agencies are seeking help from phone manufacturers in developing a smartphone kill switch.
 You know that having a strong firewall is a key component to having strong network security, but do you how firewalls work? Firewalls take their name from the protective barriers that keep buildings and engines safe from fire. While it’s unlikely that your computer is in danger of incineration, a firewall does protect it from cyber-threats; here’s how!
You know that having a strong firewall is a key component to having strong network security, but do you how firewalls work? Firewalls take their name from the protective barriers that keep buildings and engines safe from fire. While it’s unlikely that your computer is in danger of incineration, a firewall does protect it from cyber-threats; here’s how!
 With all the attention that hackers receive, you would think that they are solely responsible for every network security breach, but the truth of the matter is that most damages to company networks are due to negligence. Here are the four most common IT security oversights that can lead to major damages to your network.
With all the attention that hackers receive, you would think that they are solely responsible for every network security breach, but the truth of the matter is that most damages to company networks are due to negligence. Here are the four most common IT security oversights that can lead to major damages to your network.
 Using strong passwords is a critical part of keeping your network protected. For years we have been preaching the need to use complex passwords, along with the need to use different passwords for different accounts. As the technology of crackers (not the salted kind) improves, the need to be diligent about password security intensifies.
Using strong passwords is a critical part of keeping your network protected. For years we have been preaching the need to use complex passwords, along with the need to use different passwords for different accounts. As the technology of crackers (not the salted kind) improves, the need to be diligent about password security intensifies.
 Facebook makes it easy to connect with everyone; unfortunately, this includes people that you may not want to connect with. Whether it is the person you once had an awkward date with, or a hacker looking to hijack your profile, you can make sure that only the people who you want to see your post will be able to by adjusting your security settings.
Facebook makes it easy to connect with everyone; unfortunately, this includes people that you may not want to connect with. Whether it is the person you once had an awkward date with, or a hacker looking to hijack your profile, you can make sure that only the people who you want to see your post will be able to by adjusting your security settings.
 Your company's information on your network is labeled as "sensitive" for a reason. The files on your servers contain the secrets to your success, along with financial records about you, your employees, and your customers. When trusting sensitive data to a third party, make sure that it is someone you trust.
Your company's information on your network is labeled as "sensitive" for a reason. The files on your servers contain the secrets to your success, along with financial records about you, your employees, and your customers. When trusting sensitive data to a third party, make sure that it is someone you trust.
 Even if you are using the best antivirus software available, sensitive company data can still be compromised by users falling victim to phishing scams. Phishing is a tactic where scammers trick users into giving out their personal information, usually through deceptive spam e-mails. Looking to fry bigger fish, scammers are trying their luck at whaling.
Even if you are using the best antivirus software available, sensitive company data can still be compromised by users falling victim to phishing scams. Phishing is a tactic where scammers trick users into giving out their personal information, usually through deceptive spam e-mails. Looking to fry bigger fish, scammers are trying their luck at whaling.
 In 2011, Ponemon Research surveyed 583 U.S. businesses and found that 90% of respondents reported that their company's computers had been breached at least once by hackers within the past year; 77% of these companies felt like they were attacked multiple times within the same year. If your SMB does not have any protection from hackers, then your sensitive data is at serious risk.
In 2011, Ponemon Research surveyed 583 U.S. businesses and found that 90% of respondents reported that their company's computers had been breached at least once by hackers within the past year; 77% of these companies felt like they were attacked multiple times within the same year. If your SMB does not have any protection from hackers, then your sensitive data is at serious risk.
 Facebook has recently achieved one billion active users. Being on top of the social media world comes with a price. Facebook has become one of the top 10 most hated companies in America, this according to a January 2013 study from news site 24/7 Wall St. This survey takes into account customer and employee satisfaction and, most of all, stock prices.
Facebook has recently achieved one billion active users. Being on top of the social media world comes with a price. Facebook has become one of the top 10 most hated companies in America, this according to a January 2013 study from news site 24/7 Wall St. This survey takes into account customer and employee satisfaction and, most of all, stock prices.
 Technology can change in an instant. The popularity of mobile devises and tablets has grown exponentially in a very short amount of time. In fact, having a tablet, smartphone, laptop and desktop is not an unusual occurrence, especially for small and medium business owners who are, essentially, always on the clock. And so, it stands to reason that threats and security are also evolving along with technology.
Technology can change in an instant. The popularity of mobile devises and tablets has grown exponentially in a very short amount of time. In fact, having a tablet, smartphone, laptop and desktop is not an unusual occurrence, especially for small and medium business owners who are, essentially, always on the clock. And so, it stands to reason that threats and security are also evolving along with technology.
 Have you ever stopped and wondered where the internet is housed? Maybe all the websites are on a skyscraper-sized router? Maybe the internet all fits inside your computer? Most of the information is actually stored in data center facilities all over the world, and the sheer size and complexity of these centers will boggle your mind.
Have you ever stopped and wondered where the internet is housed? Maybe all the websites are on a skyscraper-sized router? Maybe the internet all fits inside your computer? Most of the information is actually stored in data center facilities all over the world, and the sheer size and complexity of these centers will boggle your mind.
 The smartphone ownership rate for American adults increased to 46% in 2012, this according to a study by Pew Research. This study does not include other mobile devices like tablets, laptops, and notebooks, but the use of these devices is also growing, with worldwide sales for just smartphones and tablets projected to hit 1.2 billion in 2013.
The smartphone ownership rate for American adults increased to 46% in 2012, this according to a study by Pew Research. This study does not include other mobile devices like tablets, laptops, and notebooks, but the use of these devices is also growing, with worldwide sales for just smartphones and tablets projected to hit 1.2 billion in 2013.
 The 2012 holiday online shopping season is shaping up to be the biggest yet. Harris Interactive conducted a survey regarding this holiday season, and found that 51% of Americans plan on shopping online this year. Everybody has different reasons to shop online, 71% of respondents thought they could find better deals, and 31% want to simply avoid the crowds.
The 2012 holiday online shopping season is shaping up to be the biggest yet. Harris Interactive conducted a survey regarding this holiday season, and found that 51% of Americans plan on shopping online this year. Everybody has different reasons to shop online, 71% of respondents thought they could find better deals, and 31% want to simply avoid the crowds.
 Using a strong password with complex combinations of letters and numbers will go a long way in protecting your account, but passwords provide only one level of protection against hackers. Additional levels of security can be added with multi-factor authentication. This is the best protection available for your internet accounts, and major technology companies have recently made this a reality for the public.
Using a strong password with complex combinations of letters and numbers will go a long way in protecting your account, but passwords provide only one level of protection against hackers. Additional levels of security can be added with multi-factor authentication. This is the best protection available for your internet accounts, and major technology companies have recently made this a reality for the public.
 A weak password makes identity theft easy for hackers. You would never paint your social security number on the side of a truck and drive around town, but if your password is shared, left out in the open, and used on multiple sites, then you might as well ride shotgun with the Lifelock CEO (his SSN has been stolen 13 times).
A weak password makes identity theft easy for hackers. You would never paint your social security number on the side of a truck and drive around town, but if your password is shared, left out in the open, and used on multiple sites, then you might as well ride shotgun with the Lifelock CEO (his SSN has been stolen 13 times).

























