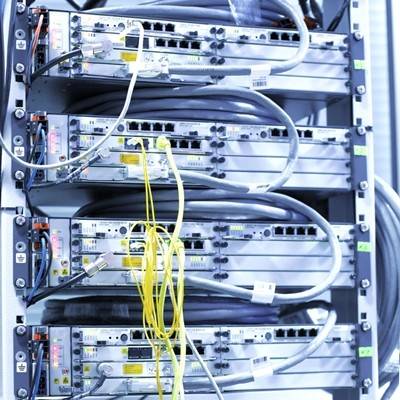
You know that having a strong firewall is a key component to having strong network security, but do you how firewalls work? Firewalls take their name from the protective barriers that keep buildings and engines safe from fire. While it’s unlikely that your computer is in danger of incineration, a firewall does protect it from cyber-threats; here’s how!
You know that having a strong firewall is a key component to having strong network security, but do you how firewalls work? Firewalls take their name from the protective barriers that keep buildings and engines safe from fire. While it’s unlikely that your computer is in danger of incineration, a firewall does protect it from cyber-threats; here’s how!
Directive Blogs
 What do hackers look for when choosing a victim? While there are hackers out there that specialize in targeting high-profile companies and executives (a hacking method call whaling), most hackers do a broad sweep of the Internet and choose the easiest targets. If your company has weak network security, then you have a target on your back.
What do hackers look for when choosing a victim? While there are hackers out there that specialize in targeting high-profile companies and executives (a hacking method call whaling), most hackers do a broad sweep of the Internet and choose the easiest targets. If your company has weak network security, then you have a target on your back.
 With all the attention that hackers receive, you would think that they are solely responsible for every network security breach, but the truth of the matter is that most damages to company networks are due to negligence. Here are the four most common IT security oversights that can lead to major damages to your network.
With all the attention that hackers receive, you would think that they are solely responsible for every network security breach, but the truth of the matter is that most damages to company networks are due to negligence. Here are the four most common IT security oversights that can lead to major damages to your network.
 The Internet has given us many new and exciting ways to transact business. The newest frontier is in regards to a virtual currency called Bitcoins that is unregulated and accepted by Internet users worldwide. Bitcoins may be too much of a novelty for your business to take seriously, but that does not discredit it as an interesting investment opportunity.
The Internet has given us many new and exciting ways to transact business. The newest frontier is in regards to a virtual currency called Bitcoins that is unregulated and accepted by Internet users worldwide. Bitcoins may be too much of a novelty for your business to take seriously, but that does not discredit it as an interesting investment opportunity.
 Using strong passwords is a critical part of keeping your network protected. For years we have been preaching the need to use complex passwords, along with the need to use different passwords for different accounts. As the technology of crackers (not the salted kind) improves, the need to be diligent about password security intensifies.
Using strong passwords is a critical part of keeping your network protected. For years we have been preaching the need to use complex passwords, along with the need to use different passwords for different accounts. As the technology of crackers (not the salted kind) improves, the need to be diligent about password security intensifies.
 As an IT company, we get excited about the newest computer hardware and software. We try to convince everybody that upgrades are great, but some people cannot be shaken from their devotion to what is familiar and refuse to upgrade their tech. In our experience, here are the three biggest reasons why upgrades are avoided.
As an IT company, we get excited about the newest computer hardware and software. We try to convince everybody that upgrades are great, but some people cannot be shaken from their devotion to what is familiar and refuse to upgrade their tech. In our experience, here are the three biggest reasons why upgrades are avoided.
 Your company's information on your network is labeled as "sensitive" for a reason. The files on your servers contain the secrets to your success, along with financial records about you, your employees, and your customers. When trusting sensitive data to a third party, make sure that it is someone you trust.
Your company's information on your network is labeled as "sensitive" for a reason. The files on your servers contain the secrets to your success, along with financial records about you, your employees, and your customers. When trusting sensitive data to a third party, make sure that it is someone you trust.
 Everybody has a weakness; Superman has Kryptonite, the Wicked Witch of the West had water, and the Death Star had a womprat-sized exhaust port. Character weaknesses make for solid storylines because they drive conflict. Your company has its own set of vulnerabilities that you may not know about, and unlike stories, conflict in business is not a good thing. Here are a few of the lesser known IT weaknesses, and what you can do to resolve them.
Everybody has a weakness; Superman has Kryptonite, the Wicked Witch of the West had water, and the Death Star had a womprat-sized exhaust port. Character weaknesses make for solid storylines because they drive conflict. Your company has its own set of vulnerabilities that you may not know about, and unlike stories, conflict in business is not a good thing. Here are a few of the lesser known IT weaknesses, and what you can do to resolve them.
 Even if you are using the best antivirus software available, sensitive company data can still be compromised by users falling victim to phishing scams. Phishing is a tactic where scammers trick users into giving out their personal information, usually through deceptive spam e-mails. Looking to fry bigger fish, scammers are trying their luck at whaling.
Even if you are using the best antivirus software available, sensitive company data can still be compromised by users falling victim to phishing scams. Phishing is a tactic where scammers trick users into giving out their personal information, usually through deceptive spam e-mails. Looking to fry bigger fish, scammers are trying their luck at whaling.
 In 2011, Ponemon Research surveyed 583 U.S. businesses and found that 90% of respondents reported that their company's computers had been breached at least once by hackers within the past year; 77% of these companies felt like they were attacked multiple times within the same year. If your SMB does not have any protection from hackers, then your sensitive data is at serious risk.
In 2011, Ponemon Research surveyed 583 U.S. businesses and found that 90% of respondents reported that their company's computers had been breached at least once by hackers within the past year; 77% of these companies felt like they were attacked multiple times within the same year. If your SMB does not have any protection from hackers, then your sensitive data is at serious risk.
 In today's digital age there are actually two of you. There is the flesh and blood you, that you are all-too-familiar with, and then there is the digital you, which amounts to a profile of yourself, compiled of data that is collected and exchanged by companies all over the internet. The worst part is how little you may know about your digital self.
In today's digital age there are actually two of you. There is the flesh and blood you, that you are all-too-familiar with, and then there is the digital you, which amounts to a profile of yourself, compiled of data that is collected and exchanged by companies all over the internet. The worst part is how little you may know about your digital self.
 There are several practices that you can do in order to keep your PC safe from computer viruses. Not visiting shady websites and keeping your antivirus program up-to-date are proven best practices; although, sometimes these practices are not enough. Sometimes hackers will find vulnerabilities in a trusted application and take advantage of them, this happened recently to Java.
There are several practices that you can do in order to keep your PC safe from computer viruses. Not visiting shady websites and keeping your antivirus program up-to-date are proven best practices; although, sometimes these practices are not enough. Sometimes hackers will find vulnerabilities in a trusted application and take advantage of them, this happened recently to Java.
 Technology can change in an instant. The popularity of mobile devises and tablets has grown exponentially in a very short amount of time. In fact, having a tablet, smartphone, laptop and desktop is not an unusual occurrence, especially for small and medium business owners who are, essentially, always on the clock. And so, it stands to reason that threats and security are also evolving along with technology.
Technology can change in an instant. The popularity of mobile devises and tablets has grown exponentially in a very short amount of time. In fact, having a tablet, smartphone, laptop and desktop is not an unusual occurrence, especially for small and medium business owners who are, essentially, always on the clock. And so, it stands to reason that threats and security are also evolving along with technology.
 With 46% of American adults owning a smartphone, the Bring Your Own Device (BYOD) to work revolution is here to stay. BYOD may be convenient for employees, but it also presents challenges for IT network security. To complicate the matter further, we are now seeing a new revolution with Bring Your Own Application to work (BYOA).
With 46% of American adults owning a smartphone, the Bring Your Own Device (BYOD) to work revolution is here to stay. BYOD may be convenient for employees, but it also presents challenges for IT network security. To complicate the matter further, we are now seeing a new revolution with Bring Your Own Application to work (BYOA).
 Internet bandwidth is a precious resource, and the amount your office can use is limited to whatever internet service package your company is signed up for. If your office is running short on bandwidth, then you will need to upgrade to a bigger package, which will be expensive. Before you spend money on upgrading, you should consider internet monitoring.
Internet bandwidth is a precious resource, and the amount your office can use is limited to whatever internet service package your company is signed up for. If your office is running short on bandwidth, then you will need to upgrade to a bigger package, which will be expensive. Before you spend money on upgrading, you should consider internet monitoring.
 With computing becoming increasing mobile, software companies have begun to roll out all kinds of file sharing options. There have been many of these file sharing options made available to consumers and companies alike, with most adhering to the freemium business model. Google (Drive), Apple (iCloud), and Microsoft (SkyDrive), and countless others have released file sharing and collaboration software via the cloud and while these services are great if you want to share small files like documents or playlists, when you need to share large files or a large quantity of files, these solutions quickly become expensive.
With computing becoming increasing mobile, software companies have begun to roll out all kinds of file sharing options. There have been many of these file sharing options made available to consumers and companies alike, with most adhering to the freemium business model. Google (Drive), Apple (iCloud), and Microsoft (SkyDrive), and countless others have released file sharing and collaboration software via the cloud and while these services are great if you want to share small files like documents or playlists, when you need to share large files or a large quantity of files, these solutions quickly become expensive.
 The smartphone ownership rate for American adults increased to 46% in 2012, this according to a study by Pew Research. This study does not include other mobile devices like tablets, laptops, and notebooks, but the use of these devices is also growing, with worldwide sales for just smartphones and tablets projected to hit 1.2 billion in 2013.
The smartphone ownership rate for American adults increased to 46% in 2012, this according to a study by Pew Research. This study does not include other mobile devices like tablets, laptops, and notebooks, but the use of these devices is also growing, with worldwide sales for just smartphones and tablets projected to hit 1.2 billion in 2013.
 The 2012 holiday online shopping season is shaping up to be the biggest yet. Harris Interactive conducted a survey regarding this holiday season, and found that 51% of Americans plan on shopping online this year. Everybody has different reasons to shop online, 71% of respondents thought they could find better deals, and 31% want to simply avoid the crowds.
The 2012 holiday online shopping season is shaping up to be the biggest yet. Harris Interactive conducted a survey regarding this holiday season, and found that 51% of Americans plan on shopping online this year. Everybody has different reasons to shop online, 71% of respondents thought they could find better deals, and 31% want to simply avoid the crowds.
 Using a strong password with complex combinations of letters and numbers will go a long way in protecting your account, but passwords provide only one level of protection against hackers. Additional levels of security can be added with multi-factor authentication. This is the best protection available for your internet accounts, and major technology companies have recently made this a reality for the public.
Using a strong password with complex combinations of letters and numbers will go a long way in protecting your account, but passwords provide only one level of protection against hackers. Additional levels of security can be added with multi-factor authentication. This is the best protection available for your internet accounts, and major technology companies have recently made this a reality for the public.
 A weak password makes identity theft easy for hackers. You would never paint your social security number on the side of a truck and drive around town, but if your password is shared, left out in the open, and used on multiple sites, then you might as well ride shotgun with the Lifelock CEO (his SSN has been stolen 13 times).
A weak password makes identity theft easy for hackers. You would never paint your social security number on the side of a truck and drive around town, but if your password is shared, left out in the open, and used on multiple sites, then you might as well ride shotgun with the Lifelock CEO (his SSN has been stolen 13 times).
 Prominent companies falling victim to hacker has become all too common in the news. Some of the larger breaches in security involve the compromise of thousands of customers' information. Definitely not the kind of press you want, not to mention the irreparable damage to your business. This can be a little scary for a small business owner, especially if you consider that these large companies have the best cyber security money can buy.
Prominent companies falling victim to hacker has become all too common in the news. Some of the larger breaches in security involve the compromise of thousands of customers' information. Definitely not the kind of press you want, not to mention the irreparable damage to your business. This can be a little scary for a small business owner, especially if you consider that these large companies have the best cyber security money can buy. If only spam were true. You would have thousands in unclaimed money, cute singles would be lining up to meet you, and there would be a magic pill that would revolutionize your personal life. Some spam is so ridiculous they are instantly deleted, others are more subtle and dangerous. Here are some threats to watch out for before you open that unsolicited email.
If only spam were true. You would have thousands in unclaimed money, cute singles would be lining up to meet you, and there would be a magic pill that would revolutionize your personal life. Some spam is so ridiculous they are instantly deleted, others are more subtle and dangerous. Here are some threats to watch out for before you open that unsolicited email.
 Everybody likes the free goodies in a hotel room, tiny shampoo bottles, coupons to nearby restaurants, and HBO top the list. Wi-Fi however, our favorite goodie, sometimes fails to make the complimentary goodie list. It seems a little messed up to us, that hotels (the place you work and sleep) charge you for Wi-Fi while Burger King gives it away for free, but we have found a Wi-Fi loophole to help you out.
Everybody likes the free goodies in a hotel room, tiny shampoo bottles, coupons to nearby restaurants, and HBO top the list. Wi-Fi however, our favorite goodie, sometimes fails to make the complimentary goodie list. It seems a little messed up to us, that hotels (the place you work and sleep) charge you for Wi-Fi while Burger King gives it away for free, but we have found a Wi-Fi loophole to help you out.
 Today, your employees are more and more technologically empowered. With the consumer electronics market teaming with amazing gadgets and high-end devices, cool tech is no longer reserved for fancy geek toys. With employees bringing in their own smartphones and tablets, mobile security becomes a big concern for small businesses.
Today, your employees are more and more technologically empowered. With the consumer electronics market teaming with amazing gadgets and high-end devices, cool tech is no longer reserved for fancy geek toys. With employees bringing in their own smartphones and tablets, mobile security becomes a big concern for small businesses.
To most people, computer viruses are things that cause annoyance, downtime, and cost money to fix. That's pretty bad on it's own, but some viruses are much more complex than others and can be far more dangerous. Let's look at Stuxnet, coined as the first weapon made entirely out of code, and why it is so frightening.
Ever since the public has been logging on to the Internet, certain people have been using the Internet to take advantage of others. Whether it be through scams, viruses, malware, phishing, or a whole slew of other dangerous activity, cyber criminals have been very good at making Internet security an industry on its own. With the colossal popularity of social networks like Twitter and Facebook, miscreants are capable of targeting even more users than ever before. On top of that, their methods seem to be hitting people where it hurts. Learn how you can prevent falling into one of their traps.
The time to implement a social media policy is now. Your social media policy outlines for employees your companies guidelines or principles for communicating in the online world. Your company should have a communications policy in place that spell out your expectations for phone and email, it’s important that you add social media and online site usage to this policy.
A lot of businesses have been taking advantage of Wi-Fi wireless networking to increase mobility around the office for staff. Most businesses seem to understand that their Wi-Fi network needs to be password protected to keep outsiders from getting in, but most businesses often make the mistake in using WEP security on their wireless network instead of a more secure solution.
The WEP algorithm can be hacked in minutes by a savvy user with a notebook, not only giving them access to your internet access, but to your network and files. Read on to learn a better way to secure your wireless network.
The problem with carrying around an expensive, portable piece of equipment is that it's possible for someone to pick it up and run with it. According to LoJack, a security firm that focuses on stolen property, two million laptops are stolen each year. What should you do if you are a victim of laptop theft?
Email is (and has been) a prime method of communication for businesses of all sizes. With email comes a whole slew of issues that are essentially synonymous with the technology; spam, information overload, phishing, and information privacy. Even Upstate New York small businesses that only do business locally are at risk of these issues. Personal email accounts are equally at risk. Employing proper precautions and practices whenever communicating via email is very important to prevent the risk of security compromises, monetary loss, and even legality issues.
Security is an important aspect to a company's continuity, and while portions of business security involve things like anti-virus and firewalls, other aspects of security can't be handled by a piece of equipment. In these cases, your organization needs to create security policies, and keep them up to date as the company grows and changes. There are many policies and sub policies that are necessary for any organization that, if non-existent, can cause chaos down the road.
Sometimes studies like these are laughable, but nevertheless, worth discussing. Norton's latest Cybercrime report suggests that people who fall victim to malware are statistically more likely to be mugged in real life. If someone is careless when it comes to online security, could that really reflect how susceptible they are in everyday life?
Have you ever been browsing the internet when out of nowhere your computer starts telling you that you are at risk or that you've downloaded a virus, and before you know it your screen is inundated with warnings and virus scanners? In most cases, this over-dramatic display is caused by a fake antivirus program. Today we're going to discuss how to prevent getting tricked by a fake antivirus attack.
Patch Tuesday is typically the second Tuesday of each month, and is the day Microsoft releases security patches for Windows Update. This month's Patch Tuesday has some of the most significant updates compared to the past several months, fixing many dangerous flaws with imminent exploits. These are critical updates that, if not installed, will leave computers vulnerable to attack.
We're asked all time, both by existing clients and during dialog while on boarding new prospects to our NOCOLOGY IT Support Services. 'What exactly is the point of running Windows updates, especially when my workstation or server is running fine?'
We'll cover why updates are so important, discuss a couple ways you can make sure they are always done as well as how we test and prevent "bad updates".
Remember in "Mission Impossible," after an agent listens to his secret mission, the recording goes on to mention "This message will self destruct…" followed by the oversized tape-recorder puffing out billows of smoke. Businesses have gone a long way since then (we've replaced sending tape-recorders with the much more efficient email), and encrypting email messages is easy and cost effective for businesses that want to ensure that certain messages are only seen by certain recipients.
 Most of the time, when it comes to cybersecurity, businesses tend to focus primarily on external threats rather than those that might be lurking in the shadows of their internal operations. Believe it or not, the most dangerous entities out there could very well be working for you, right under your nose.
Most of the time, when it comes to cybersecurity, businesses tend to focus primarily on external threats rather than those that might be lurking in the shadows of their internal operations. Believe it or not, the most dangerous entities out there could very well be working for you, right under your nose.
 Since you run a business, you know that your business’s network requires a secure firewall in order to keep threats out. In fact, the firewall is the most basic of security protocol that you should be taking advantage of. Knowing what a firewall protects you from, and what it doesn’t protect you from, is an important first step toward improving your data infrastructure’s security, and in turn improving your business’s continuity.
Since you run a business, you know that your business’s network requires a secure firewall in order to keep threats out. In fact, the firewall is the most basic of security protocol that you should be taking advantage of. Knowing what a firewall protects you from, and what it doesn’t protect you from, is an important first step toward improving your data infrastructure’s security, and in turn improving your business’s continuity.
 The modern business is inundated with all types of threats, from people outside the organization phishing around for information, to employees that are aloof to their role in your network’s security. If your network’s security is like a levee, it is indisputably an IT department’s job to fill in the gaps to ensure a deluge of misfortune doesn’t swamp your company’s IT. So what happens when your company’s IT department is the biggest offender of perilous activity?
The modern business is inundated with all types of threats, from people outside the organization phishing around for information, to employees that are aloof to their role in your network’s security. If your network’s security is like a levee, it is indisputably an IT department’s job to fill in the gaps to ensure a deluge of misfortune doesn’t swamp your company’s IT. So what happens when your company’s IT department is the biggest offender of perilous activity?
 Technology is often exploited by hackers for their benefit, but one avenue of attack that’s consistently neglected is the mobile device. Smartphones and tablets are arguably at greater risk than desktops and workstations due to them being exposed to more wireless networks. One of the greatest threats to these devices is the botnet, a threat that usually targets desktop computers, enslaving them and turning the machine against its owner (and the rest of the Internet).
Technology is often exploited by hackers for their benefit, but one avenue of attack that’s consistently neglected is the mobile device. Smartphones and tablets are arguably at greater risk than desktops and workstations due to them being exposed to more wireless networks. One of the greatest threats to these devices is the botnet, a threat that usually targets desktop computers, enslaving them and turning the machine against its owner (and the rest of the Internet).
 There are many types of malware out there, but few are as scary as ransomware. Imagine being struck by a threat that instantaneously locks down your files and keeps you from accessing them until you pay a certain amount of money. If your business is targeted by ransomware, would you be able to protect it from dragging your operations into a bitter pit of despair?
There are many types of malware out there, but few are as scary as ransomware. Imagine being struck by a threat that instantaneously locks down your files and keeps you from accessing them until you pay a certain amount of money. If your business is targeted by ransomware, would you be able to protect it from dragging your operations into a bitter pit of despair?