Computers use quite a lot of different types of protocol to function. In particular, the Internet takes advantage of protocol to a great degree. You might recognize terms like Hypertext Transfer Protocol Secure, Transmission Control Protocol/Internet Protocol, File Transfer Protocol, Internet Message Protocol, and Post Office Protocol. But what exactly is protocol, and why is it important?
Directive Blogs
During your time in the business world, you may have heard about the Dark Web. It’s a place that’s filled with illegal activity, with some of the most notable being online marketplaces where credentials and personal records can be sold to the highest bidder. However, there’s much more to the Dark Web than meets the eye.
Sherlock Holmes is one of the most famous detectives in fiction, but without his dear Dr. Watson, he would have been stumped on occasion. There’s a good reason why IBM named its super-intelligent computer, Watson, after the famous character. True to its namesake, Watson is now being used to safeguard 40 organizations from cyber security threats.
The average office worker needs to access the Internet in order to do their job. What they don’t need to access is cat videos, memes, social media, online games, and malware-ridden websites. How can a business owner clamp down on Internet activity in their office? By equipping their network with a content filtering solution, of course.
December 14th is the last day that our government representatives can vote whether or not to continue the Internet’s protection under the net neutrality rules established in 2015. Without these rules in place, your data can be analyzed by your Internet service provider, and they are free to act on that knowledge and manipulate your Internet in support of their own interests.
Many of those in favor to end net neutrality focused not on the issues of technology, but on the principles of the 'invisible hand,' otherwise known as the free market. Their argument, as espoused by Ajit Pai, is that regulation - particularly that of net neutrality - stifled innovation, and it’s that lack of variation which is the cause of so many of us being stuck with crummy internet options. In fact, Mr. Pai has a valid point, states and countries with multiple ISP services, do seem to have better outcomes for their customers. The problem is most of us don’t live in those places and don’t have many, if any, choices but one or two.
If you’re trying to run your business without considering communication, you’re crippling your business unnecessarily. One of the ways that you can improve communications is by capitalizing on a modern phone system that uses the cloud. You might be surprised by how great a cloud-hosted VoIP solution works for your business--especially if you haven’t thrown out the traditional telephone handset yet.
When you are surfing the web, do you know if you are secure? Typically, your browser will tell you when a site is secure or not. This is especially important if you are putting in sensitive information, like passwords or credit card information. Google Chrome is stepping up it’s game to keep users safe.
It’s hard to believe that half of the world still doesn’t have access to the Internet. When so many people in the west take their near-ubiquitous Internet accessibility for granted, over three and half billion people don’t have access at all. Years ago, Google created what came to be known as X (or Google X) which was basically a research-and-development facility.
In the fairy tale of Hansel and Gretel, the titular characters decided to leave a trail of breadcrumbs behind them, so they could find their way back home. While this strategy didn’t work out very well for the siblings, the same concept is used in computing today. We even refer to it as breadcrumb navigation in honor of the German fairy tale.
 Everyone who uses e-mail has become accustomed to finding the occasional Spam e-mail. No matter how careful you are, it's only a matter of time before you receive a Viagra testing e-mail, the South African Inheritance Tied Up in Legal Battles, or the Winning of a Sweepstakes that you never signed up for. Where do those e-mails come from?
Everyone who uses e-mail has become accustomed to finding the occasional Spam e-mail. No matter how careful you are, it's only a matter of time before you receive a Viagra testing e-mail, the South African Inheritance Tied Up in Legal Battles, or the Winning of a Sweepstakes that you never signed up for. Where do those e-mails come from?
This has been a pretty common topic for us on the Directive blog. We've seen a lot of Upstate New York clients and customers suffer the consequences when online retailers and other account providers experience a security breach. It is equally vital for consumers to know what to do in the event of a security breach as it is the company that is actually breached.
Computer viruses and malware have been around for a long time, and cybercriminals have always tried to package their malevolent doings under a veil of deception. One method that has been in place for a while now is called scareware. Often disguised as something that appears to want to help your computer, scareware will scam users into paying for a service that isn't beneficial.
 For sites you need to log into often, having your browser remember your password can save you time logging in, especially if you are using secure passwords that you might need to look up otherwise. There are circumstances where you might want to manage what personal information gets stored in your web browser.
For sites you need to log into often, having your browser remember your password can save you time logging in, especially if you are using secure passwords that you might need to look up otherwise. There are circumstances where you might want to manage what personal information gets stored in your web browser.
 In order to best serve their clients, companies need to have a comprehensive program in place to help them defend their systems from malware attacks on their company's infrastructure. These attacks can have a devastating effect on a business's continuity, so having an appreciation for exactly what types of adversaries your company is up against is important. There are several types of potential intruders that you should be aware of.
In order to best serve their clients, companies need to have a comprehensive program in place to help them defend their systems from malware attacks on their company's infrastructure. These attacks can have a devastating effect on a business's continuity, so having an appreciation for exactly what types of adversaries your company is up against is important. There are several types of potential intruders that you should be aware of.
Internet privacy is no new issue. Between malicious hackers trying to breach private information, governments trying to regulate it, and organizations trying to track as many metrics as they can, the Internet continues to chug along for the most part just fine. Are YOU concerned about Internet privacy?
This month Google announced that their search results will now contain personal results from friends and connections made in Google+. Twitter, the real-time searchable social network, publicly announced that they thought this was not a good idea. Will personalizing search results make for a better Google experience or will it hurt? Let's take a look.
 Computer viruses are pretty serious threats, and can cause huge expensive issues for businesses. Many cases of malware and computer viruses actually use your computer to commit real crimes. The FBI states that hundreds of thousands of people will likely lose the ability to surf the web if they have a particular piece of malware.
Computer viruses are pretty serious threats, and can cause huge expensive issues for businesses. Many cases of malware and computer viruses actually use your computer to commit real crimes. The FBI states that hundreds of thousands of people will likely lose the ability to surf the web if they have a particular piece of malware.
 Having strong passwords for your online accounts is very important, but sometimes you may want a little more protection in the event your password gets stolen or someone forces their way through it. If you use Google's Gmail service, you can set up your account, then you will need two forms of authentication to get into your email.
Having strong passwords for your online accounts is very important, but sometimes you may want a little more protection in the event your password gets stolen or someone forces their way through it. If you use Google's Gmail service, you can set up your account, then you will need two forms of authentication to get into your email.
So you keep hearing about the need for a firewall, but maybe you’re not exactly sure what it is or even what it does. As a business owner, you don’t need to fully grasp the complexities of network security in order to effectively manage your company. Although, it is beneficial for every business owner to understand the basics of what a firewall is, along with a working knowledge of how it protects an organization’s IT infrastructure.
With the growing popularity of Cyber Monday sales and explosion of all types of eCommerce, employees are more than likely tempted to shop during work hours. There are a lot of promotions exclusively available to online shoppers that take place during a business’ hour of operations. Many companies allow occasional use of company time for personal use. However, some employees are going to take advantage of this generosity and abuse the privilege.
 Which is worst, fingernails scraping down a chalkboard or slow internet? A person who would answer the former has likely never experienced internet speeds in excess of 1 Mbps. It is a proven fact that faster is better. Before you decide to complain to your Internet Service Provider (ISP) or even switch providers, make sure that you are informed about what your internet speed is and should be.
Which is worst, fingernails scraping down a chalkboard or slow internet? A person who would answer the former has likely never experienced internet speeds in excess of 1 Mbps. It is a proven fact that faster is better. Before you decide to complain to your Internet Service Provider (ISP) or even switch providers, make sure that you are informed about what your internet speed is and should be.
!--
How to Anonymously Browse the Internet
--> Some places on the Internet are only suitable for secret browsing. Maybe you're shopping for a present and don't want your links to show in your browsing history, or maybe you don't want the customized ads to reflect a private interest. Whatever your reason is for wanting to anonymously browse the web, here's how you do it.
Some places on the Internet are only suitable for secret browsing. Maybe you're shopping for a present and don't want your links to show in your browsing history, or maybe you don't want the customized ads to reflect a private interest. Whatever your reason is for wanting to anonymously browse the web, here's how you do it.
 Every business owner understands that having a good reputation is paramount toward their success. Yet, some business owners may not fully grasp just how much the Internet influences their company’s reputation in today’s business environment. In order to find out what the people of the Internet are saying about your business, you have to manage your company’s online reputation.
Every business owner understands that having a good reputation is paramount toward their success. Yet, some business owners may not fully grasp just how much the Internet influences their company’s reputation in today’s business environment. In order to find out what the people of the Internet are saying about your business, you have to manage your company’s online reputation.
 The Internet is a fantastic tool that has ushered in an era of productivity and connectivity that we could only previously have dreamed of. Unfortunately, like every great tool, it can be used for darker, malicious purposes. In the Internet’s case, it’s used for anonymous illegal activity, like drug trafficking or selling data on the black market.
The Internet is a fantastic tool that has ushered in an era of productivity and connectivity that we could only previously have dreamed of. Unfortunately, like every great tool, it can be used for darker, malicious purposes. In the Internet’s case, it’s used for anonymous illegal activity, like drug trafficking or selling data on the black market.
 When one thinks about The Internet of Things, new and fantastic devices come to mind, like smart homes, smart cars, mobile devices, and more. While innovations like these are fueling the excitement behind the IoT, it’s actually the smaller, behind-the-scenes IoT devices which are poised to bring about the most significant change to our connected society.
When one thinks about The Internet of Things, new and fantastic devices come to mind, like smart homes, smart cars, mobile devices, and more. While innovations like these are fueling the excitement behind the IoT, it’s actually the smaller, behind-the-scenes IoT devices which are poised to bring about the most significant change to our connected society.
 You might remember Bitcoin, the cryptocurrency known for increasing the anonymity and privacy of transactions on the web. Bitcoin was gaining ground for a while, but a couple of key events left it in the dust, sinking to seeing use only as a currency used by hackers and criminals in online black markets. Now, however, it seems that Bitcoin is being used again, and with a few key innovations in how it’s spent, Bitcoin will continue to grow more popular as a payment option.
You might remember Bitcoin, the cryptocurrency known for increasing the anonymity and privacy of transactions on the web. Bitcoin was gaining ground for a while, but a couple of key events left it in the dust, sinking to seeing use only as a currency used by hackers and criminals in online black markets. Now, however, it seems that Bitcoin is being used again, and with a few key innovations in how it’s spent, Bitcoin will continue to grow more popular as a payment option.
 Wireless Internet access is a luxury that seems commonplace, but there are many who experience trouble with their connections on a daily basis. Sometimes the problem stems from familiar issues that could happen at any minute, but other times the issues might not be so obvious. Either way, you should be aware of the most common disruptions to your WiFi signal, even those that you might not consider problems.
Wireless Internet access is a luxury that seems commonplace, but there are many who experience trouble with their connections on a daily basis. Sometimes the problem stems from familiar issues that could happen at any minute, but other times the issues might not be so obvious. Either way, you should be aware of the most common disruptions to your WiFi signal, even those that you might not consider problems.
 A good business practices extreme caution when using the Internet, thanks to hackers using any means possible to unleash threats against organizations of all sizes. You teach your employees how to avoid threats and to avoid suspicious websites, but what if that’s not enough to keep hackers out of your network infrastructure?
A good business practices extreme caution when using the Internet, thanks to hackers using any means possible to unleash threats against organizations of all sizes. You teach your employees how to avoid threats and to avoid suspicious websites, but what if that’s not enough to keep hackers out of your network infrastructure?
 The Internet is an absolutely essential part of today’s workplace. It helps businesses get the upper hand on their competition by offering practically limitless access to tools, resources, and contacts that can be used for the betterment of their organizations. However, classrooms can reap the benefits of Internet too, and it’s surprising that it’s taken so long for all schools to hop on board with this concept.
The Internet is an absolutely essential part of today’s workplace. It helps businesses get the upper hand on their competition by offering practically limitless access to tools, resources, and contacts that can be used for the betterment of their organizations. However, classrooms can reap the benefits of Internet too, and it’s surprising that it’s taken so long for all schools to hop on board with this concept.
 We all know how important an Internet connection is to the success of any business. In fact, it takes an exceptionally powerful cabling protocol to ensure that your business’s Internet connection remains constant. While many businesses take advantage of big cable companies like Time Warner Cable and Comcast for their Internet needs, a select few have the option of Google Fiber.
We all know how important an Internet connection is to the success of any business. In fact, it takes an exceptionally powerful cabling protocol to ensure that your business’s Internet connection remains constant. While many businesses take advantage of big cable companies like Time Warner Cable and Comcast for their Internet needs, a select few have the option of Google Fiber.
 For all of you YouTubers out there, you probably already know that the video-playback website is offering a premium service that launched last month. Now you can watch cat videos and other nonsense in an entirely new way. But what do you get with a subscription to YouTube Red? Is it worth the money? Well, let’s find out.
For all of you YouTubers out there, you probably already know that the video-playback website is offering a premium service that launched last month. Now you can watch cat videos and other nonsense in an entirely new way. But what do you get with a subscription to YouTube Red? Is it worth the money? Well, let’s find out.
 Have you ever wondered how the Internet is capable of connecting countries on the other side of the world? You may already be aware of this, but the Internet’s cables run deep underneath the ocean’s surface, all around the world. In fact, you might wonder how we could even keep these cables safe when they’re submerged underneath such an immense amount of water.
Have you ever wondered how the Internet is capable of connecting countries on the other side of the world? You may already be aware of this, but the Internet’s cables run deep underneath the ocean’s surface, all around the world. In fact, you might wonder how we could even keep these cables safe when they’re submerged underneath such an immense amount of water.
 With the Internet of Things continuing to gain popularity, we’re seeing more devices that connect to the Internet than ever before. However, what the users of these devices might be failing to take into consideration is the fact that the Internet is a dangerous place full of threats and other miscreants. What happens if these criminals decide to attack any of your connected devices? This is a relevant question to ask since October is Cyber Security Month, and The Internet of Things represents the next frontier of cyberspace.
With the Internet of Things continuing to gain popularity, we’re seeing more devices that connect to the Internet than ever before. However, what the users of these devices might be failing to take into consideration is the fact that the Internet is a dangerous place full of threats and other miscreants. What happens if these criminals decide to attack any of your connected devices? This is a relevant question to ask since October is Cyber Security Month, and The Internet of Things represents the next frontier of cyberspace.
 October is Cyber Security month. We want to bring attention to this very important issue affecting every person and organization connected to the Internet. When discussing cyber security, we often talk about computer viruses and malware, but these threats are only part of the cyber security equation. It’s just as important that you, your staff, and even your family, are mindful to not overshare information online that can compromise your organization’s security and personal identities.
October is Cyber Security month. We want to bring attention to this very important issue affecting every person and organization connected to the Internet. When discussing cyber security, we often talk about computer viruses and malware, but these threats are only part of the cyber security equation. It’s just as important that you, your staff, and even your family, are mindful to not overshare information online that can compromise your organization’s security and personal identities.
 With revelations coming to light on how governments are monitoring citizen's Internet usage, many people are concerned about their online privacy. Most of us are so dependent upon technology that it's almost impossible to totally disconnect off the grid, yet there are a few tricks you can use to browse the Web with anonymity.
With revelations coming to light on how governments are monitoring citizen's Internet usage, many people are concerned about their online privacy. Most of us are so dependent upon technology that it's almost impossible to totally disconnect off the grid, yet there are a few tricks you can use to browse the Web with anonymity.
 As a business owner, you might have the sudden and inexplicable urge to creep on (track) your competitors to get a feel for their prices and services. With these six apps, you can make this job a little bit easier by seeing what others have to say about your competitors, including what they are saying about you.
As a business owner, you might have the sudden and inexplicable urge to creep on (track) your competitors to get a feel for their prices and services. With these six apps, you can make this job a little bit easier by seeing what others have to say about your competitors, including what they are saying about you.
 When you think of the Internet of Things, does your mind immediately wander into the realm of connected devices that change the way we interact with each other? Or, does it consider the security issues that can potentially become a threat to your entire network and technology infrastructure? Hopefully it’s a little of both, with an emphasis placed on security.
When you think of the Internet of Things, does your mind immediately wander into the realm of connected devices that change the way we interact with each other? Or, does it consider the security issues that can potentially become a threat to your entire network and technology infrastructure? Hopefully it’s a little of both, with an emphasis placed on security.
 Just like Silk Road (the illegal online black market designed to smuggle drugs around the world), there exists an online trade for zero-day exploits. Unsurprisingly, hackers find it exceptionally lucrative to sell these exploits for profit. Now, there’s a new marketplace where hackers can get their hands on these vulnerabilities, and it’s all thanks to the anonymity of the Darknet.
Just like Silk Road (the illegal online black market designed to smuggle drugs around the world), there exists an online trade for zero-day exploits. Unsurprisingly, hackers find it exceptionally lucrative to sell these exploits for profit. Now, there’s a new marketplace where hackers can get their hands on these vulnerabilities, and it’s all thanks to the anonymity of the Darknet.
 When it comes to challenges, there’s no better place to turn to than the Internet. However, the Internet is also saturated with useless, time-wasting videos and articles that are meant to stimulate the mind and destroy boredom. In the face of all of this media, a lone CollegeHumor video challenges a user to endure boredom for a measly three minutes.
When it comes to challenges, there’s no better place to turn to than the Internet. However, the Internet is also saturated with useless, time-wasting videos and articles that are meant to stimulate the mind and destroy boredom. In the face of all of this media, a lone CollegeHumor video challenges a user to endure boredom for a measly three minutes.
 We all know how annoying WiFi can be at times. Sometimes it’s simply a bad connection, or perhaps there are too many devices accessing your network. Or, maybe it’s your sneaky neighbor stealing your WiFi. Regardless of what the cause is, there’s a way to check your WiFi usage in the Windows operating system.
We all know how annoying WiFi can be at times. Sometimes it’s simply a bad connection, or perhaps there are too many devices accessing your network. Or, maybe it’s your sneaky neighbor stealing your WiFi. Regardless of what the cause is, there’s a way to check your WiFi usage in the Windows operating system.
 When the Internet was first established, malware and hacking were in their infancy, and not as much of an immediate problem as they are today. Thanks to this fact, the Internet wasn’t really created with a certain security design in mind, and has instead adapted to shifts in its environment. Unfortunately, as hackers grow more powerful, several of these patchwork protocols are growing outdated.
When the Internet was first established, malware and hacking were in their infancy, and not as much of an immediate problem as they are today. Thanks to this fact, the Internet wasn’t really created with a certain security design in mind, and has instead adapted to shifts in its environment. Unfortunately, as hackers grow more powerful, several of these patchwork protocols are growing outdated.
 Most search engines are pretty good at keeping malicious websites out of your search results, but just like any other piece of software on your computer, some search engines do a better job of keeping these threats out of your immediate access. According to TV-Test, a German independent testing lab, there’s a huge difference between the security of the world’s top search engines, like Bing and Google.
Most search engines are pretty good at keeping malicious websites out of your search results, but just like any other piece of software on your computer, some search engines do a better job of keeping these threats out of your immediate access. According to TV-Test, a German independent testing lab, there’s a huge difference between the security of the world’s top search engines, like Bing and Google.
 For those with weak stomachs, it’s not recommended to go back and read an email that was just sent. In doing so, a spelling or grammar error is likely to be found, which will cause one’s stomach to turn and fill with regret. If only there was a do-over button. Thanks to the new app called Pluto Mail, there is one.
For those with weak stomachs, it’s not recommended to go back and read an email that was just sent. In doing so, a spelling or grammar error is likely to be found, which will cause one’s stomach to turn and fill with regret. If only there was a do-over button. Thanks to the new app called Pluto Mail, there is one.
 When a dining establishment goes out of business, it usually doesn’t make the news. After all, running a restaurant is a risky endeavor. However, for one Washington D.C. eatery, it’s blaming its failure a Google Places mishap, which makes you think twice about how important it is for your business to have its online information properly displayed.
When a dining establishment goes out of business, it usually doesn’t make the news. After all, running a restaurant is a risky endeavor. However, for one Washington D.C. eatery, it’s blaming its failure a Google Places mishap, which makes you think twice about how important it is for your business to have its online information properly displayed.
 The world of online currency is a strange, bizarre realm. While it’s designed for online transactions, it has gone from the somewhat useful (Bitcoin) to just plain silly (Dogecoin). However, there’s now an anonymous cryptocurrency available for use called Darkcoin, which attempts to make online transactions more difficult to trace.
The world of online currency is a strange, bizarre realm. While it’s designed for online transactions, it has gone from the somewhat useful (Bitcoin) to just plain silly (Dogecoin). However, there’s now an anonymous cryptocurrency available for use called Darkcoin, which attempts to make online transactions more difficult to trace.
 The Internet of Things is changing the face of web-connected devices as we know it. Some would argue that the world isn’t ready for the IoT, but it’s on its way nonetheless. But what really constitutes the Internet of Things? InfoWorld suggests that a lot of what the public sees as the Internet of Things shouldn’t be classified as IoT devices. Therefore, we need a more substantial definition for this revolutionary phenomenon.
The Internet of Things is changing the face of web-connected devices as we know it. Some would argue that the world isn’t ready for the IoT, but it’s on its way nonetheless. But what really constitutes the Internet of Things? InfoWorld suggests that a lot of what the public sees as the Internet of Things shouldn’t be classified as IoT devices. Therefore, we need a more substantial definition for this revolutionary phenomenon.
 With the Internet of Things connecting more devices to the Internet, these devices can potentially be turned to nefarious use. Despite all of the benefits of the Internet of Things, like big data analytics, anything connected to the Internet is threatened by cyber crime to at least some degree. In fact, some professionals believe that the Internet of Things will usher in an era of new types of cyber crime; murder included.
With the Internet of Things connecting more devices to the Internet, these devices can potentially be turned to nefarious use. Despite all of the benefits of the Internet of Things, like big data analytics, anything connected to the Internet is threatened by cyber crime to at least some degree. In fact, some professionals believe that the Internet of Things will usher in an era of new types of cyber crime; murder included.
 Can you tell the difference between the two words, Internet and Intranet? The difference is much more than simply two letters. Both are valuable marketing tools, particularly for small businesses, but what exactly differentiates them from each other? The key to understanding this is a simple English lesson.
Can you tell the difference between the two words, Internet and Intranet? The difference is much more than simply two letters. Both are valuable marketing tools, particularly for small businesses, but what exactly differentiates them from each other? The key to understanding this is a simple English lesson.
 19 years ago, a class of fifth graders from Helena, Montana was featured in a PSA video that, looking back, made some eerily-close predictions about how the Internet is used today. When this PSA was shot in 1995, only 0.4% of the world's population regularly used the Internet. Today, nearly 39% of the world uses it, and for good reason, as predicted all those years ago.
19 years ago, a class of fifth graders from Helena, Montana was featured in a PSA video that, looking back, made some eerily-close predictions about how the Internet is used today. When this PSA was shot in 1995, only 0.4% of the world's population regularly used the Internet. Today, nearly 39% of the world uses it, and for good reason, as predicted all those years ago.
 We've all wasted time surfing the Internet, but as we know, there are unfortunately extremes to every action. Wasting time by mindlessly browsing Internet pages can certainly become a problem when it claims huge portions of your time at work, killing your productivity. Can you not seem to get away from surfing the Internet?
We've all wasted time surfing the Internet, but as we know, there are unfortunately extremes to every action. Wasting time by mindlessly browsing Internet pages can certainly become a problem when it claims huge portions of your time at work, killing your productivity. Can you not seem to get away from surfing the Internet?
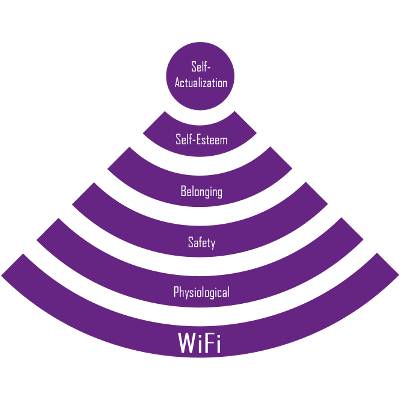 In 1943, psychologist Abraham Maslow published a paper about human motivation that would become the well-known Maslow's Hierarchy of Needs. His theory states that before self-actualization can be achieved, four needs must first be met, like esteem, belonging, safety, and physiological (the most basic which includes, air, food, water, etc.). In 2014, we feel the need to add one more layer to Maslow's pyramid: WiFi.
In 1943, psychologist Abraham Maslow published a paper about human motivation that would become the well-known Maslow's Hierarchy of Needs. His theory states that before self-actualization can be achieved, four needs must first be met, like esteem, belonging, safety, and physiological (the most basic which includes, air, food, water, etc.). In 2014, we feel the need to add one more layer to Maslow's pyramid: WiFi.
 With the NSA and Edward Snowden making headlines around the world, it's enough to make any user of the Internet think twice about online security and wonder if they are being monitored or not. Google Search has been a popular hub for third party monitoring, which makes Internet users ask, "Is there a more secure search engine available?" There is with DuckDuckGo.
With the NSA and Edward Snowden making headlines around the world, it's enough to make any user of the Internet think twice about online security and wonder if they are being monitored or not. Google Search has been a popular hub for third party monitoring, which makes Internet users ask, "Is there a more secure search engine available?" There is with DuckDuckGo.
 The Internet certainly has changed the way we live, work, shop, and communicate. We may think we're superior to previous generations because of all our Internet-based technology, but we have video proof that the Internet was actually conceptualized in 1969. In many ways, our parents and grandparents were spot on with their predictions. In other ways, not so much.
The Internet certainly has changed the way we live, work, shop, and communicate. We may think we're superior to previous generations because of all our Internet-based technology, but we have video proof that the Internet was actually conceptualized in 1969. In many ways, our parents and grandparents were spot on with their predictions. In other ways, not so much.
 Since the late 1990s, digital information, music, movies, software, and content has been at risk of being illegally shared worldwide for free. Peer-to-peer file sharing has forced entire industries to shift the way they do business as they try to counteract the illegal practice. The new Copyright Alert System will attempt to quell illegal file sharing.
Since the late 1990s, digital information, music, movies, software, and content has been at risk of being illegally shared worldwide for free. Peer-to-peer file sharing has forced entire industries to shift the way they do business as they try to counteract the illegal practice. The new Copyright Alert System will attempt to quell illegal file sharing.
 Perouse the YouTube comments on any popular video and it will appear like a teenybopper is texting a neo nazi. The level of stupidity seen in the comments of YouTube is the ultimate proof of human idiocy. Finally, after years of putting up with people's hate and ignorance, YouTube is cracking down on comments!
Perouse the YouTube comments on any popular video and it will appear like a teenybopper is texting a neo nazi. The level of stupidity seen in the comments of YouTube is the ultimate proof of human idiocy. Finally, after years of putting up with people's hate and ignorance, YouTube is cracking down on comments!
 Are you looking to enhance your business with new mobile technologies to give your workforce the competitive edge? If so, then we recommend that before you go out and purchase new mobile devices, you first need to understand the technology requirements of your organization. Here are four crucial needs you will want to consider.
Are you looking to enhance your business with new mobile technologies to give your workforce the competitive edge? If so, then we recommend that before you go out and purchase new mobile devices, you first need to understand the technology requirements of your organization. Here are four crucial needs you will want to consider.
 Even if your business doesn't have a website, or use social media, you still need to take advantage of at least one important Internet tool to direct people to your organization: Google Places. Getting your business mentioned on the Internet's biggest listing resource will make sure that anybody looking for you can find you.
Even if your business doesn't have a website, or use social media, you still need to take advantage of at least one important Internet tool to direct people to your organization: Google Places. Getting your business mentioned on the Internet's biggest listing resource will make sure that anybody looking for you can find you.
 Anybody who is a master of multitasking is a fan of YouTube. There's so much useful and entertaining content on YouTube that it's perfect for streaming media in the background while working on a project. Unfortunately, YouTube is a large application that eats up precious CPU resources and may slow down your computer.
Anybody who is a master of multitasking is a fan of YouTube. There's so much useful and entertaining content on YouTube that it's perfect for streaming media in the background while working on a project. Unfortunately, YouTube is a large application that eats up precious CPU resources and may slow down your computer.
 There are many different sleep solutions on the market; some are simple like a fluffier pillow, others are more elaborate like a sleep apnea CPAP mask that assists with breathing. According to a new study by the University of Tubingen in Germany, the best sleep solution may be syncing the sounds around you with the rhythms of your brain.
There are many different sleep solutions on the market; some are simple like a fluffier pillow, others are more elaborate like a sleep apnea CPAP mask that assists with breathing. According to a new study by the University of Tubingen in Germany, the best sleep solution may be syncing the sounds around you with the rhythms of your brain.
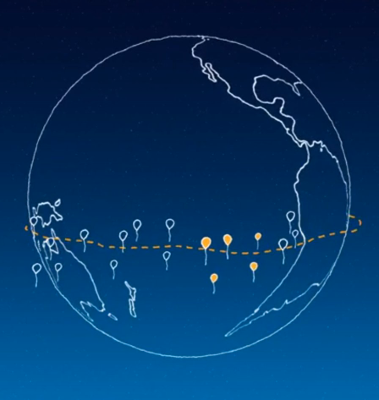 The benefits that come with a society that have Internet access can help people in dramatic ways. According to Google, only 1/3 of the world's population is enjoying these benefits. The rest of the world is out of reach from the Internet's communication lines and satellite signals. Google plans on bridging this gap by using balloons.
The benefits that come with a society that have Internet access can help people in dramatic ways. According to Google, only 1/3 of the world's population is enjoying these benefits. The rest of the world is out of reach from the Internet's communication lines and satellite signals. Google plans on bridging this gap by using balloons.
 We’re all familiar with the “Dummies” book series, they are helpful when it comes to understanding specific topics, but not all of us have the time to read a manual of information. We want to dummify web knowledge regarding the web’s ever changing buzzwords and platforms. This will help educate you on what web services and products are available for your company’s website. Every business owner should at least be aware of the website platform they are using and be fluent enough to understand its capabilities. If your website breaks, then having at least a basic understanding will make interacting with your website maintenance team go smoother, and give you a foot in the door if you ever want to take the plunge and learn more.
We’re all familiar with the “Dummies” book series, they are helpful when it comes to understanding specific topics, but not all of us have the time to read a manual of information. We want to dummify web knowledge regarding the web’s ever changing buzzwords and platforms. This will help educate you on what web services and products are available for your company’s website. Every business owner should at least be aware of the website platform they are using and be fluent enough to understand its capabilities. If your website breaks, then having at least a basic understanding will make interacting with your website maintenance team go smoother, and give you a foot in the door if you ever want to take the plunge and learn more.
 When you hear the phrase, "The machines are taking over," you may think of science fiction stories where robots become self-aware and enslave humanity. You may not have realized it, but the machines have already taken over; not with a violent uprising, but through what's called the Internet of Things (IoT).
When you hear the phrase, "The machines are taking over," you may think of science fiction stories where robots become self-aware and enslave humanity. You may not have realized it, but the machines have already taken over; not with a violent uprising, but through what's called the Internet of Things (IoT).
 The Internet was originally designed in 1989 as a tool for the European science agency CERN to help share information among physicist in universities around the world. On April 30th, 1993, the Internet went public. Back in 1993, Internet founders like Tim Berners-Lee did not likely realize that his invention would solve more problems than physics ever could.
The Internet was originally designed in 1989 as a tool for the European science agency CERN to help share information among physicist in universities around the world. On April 30th, 1993, the Internet went public. Back in 1993, Internet founders like Tim Berners-Lee did not likely realize that his invention would solve more problems than physics ever could.
 Do you have reservations about using a public cloud computing service to host your company’s data and applications? Despite strong security measures taken by public cloud computing companies, there are businesses that choose to play it safe and build their own private cloud infrastructure. SMBs also have a third cloud computing option which is to adopt a hybrid cloud infrastructure.
Do you have reservations about using a public cloud computing service to host your company’s data and applications? Despite strong security measures taken by public cloud computing companies, there are businesses that choose to play it safe and build their own private cloud infrastructure. SMBs also have a third cloud computing option which is to adopt a hybrid cloud infrastructure.
 Cloud computing is a hot business technology. Research firm Gartner surveyed businesses worldwide and found that 60% have increased their budgets for cloud services through 2014. Gartner also predicts that the cloud services market will increase 18.5% this year. Are you looking to migrate over to the cloud? Here are a few considerations before your business goes cloud crazy.
Cloud computing is a hot business technology. Research firm Gartner surveyed businesses worldwide and found that 60% have increased their budgets for cloud services through 2014. Gartner also predicts that the cloud services market will increase 18.5% this year. Are you looking to migrate over to the cloud? Here are a few considerations before your business goes cloud crazy.
 The Internet has given us many new and exciting ways to transact business. The newest frontier is in regards to a virtual currency called Bitcoins that is unregulated and accepted by Internet users worldwide. Bitcoins may be too much of a novelty for your business to take seriously, but that does not discredit it as an interesting investment opportunity.
The Internet has given us many new and exciting ways to transact business. The newest frontier is in regards to a virtual currency called Bitcoins that is unregulated and accepted by Internet users worldwide. Bitcoins may be too much of a novelty for your business to take seriously, but that does not discredit it as an interesting investment opportunity.
 E-mail and other forms of digital communication have revolutionized the way humans interact. Anybody old enough to remember life before e-mail (B.E.), can tell some great stories that include kooky characters like Mr. Stamp and Mrs. Envelope. E-mail has changed things; all of us use it every day, but how does it work?
E-mail and other forms of digital communication have revolutionized the way humans interact. Anybody old enough to remember life before e-mail (B.E.), can tell some great stories that include kooky characters like Mr. Stamp and Mrs. Envelope. E-mail has changed things; all of us use it every day, but how does it work?
 Anytime you take a step into the Internet, there's a pretty good chance that you are going to step in a fresh and steamy pile of spam. Spam can ruin your company's Internet footprint. Spam can also find its way into the depths of your website and stink up the whole place. It's especially embarrassing when you don't even know that you have spam on the bottom of your virtual shoe; here's how it got there.
Anytime you take a step into the Internet, there's a pretty good chance that you are going to step in a fresh and steamy pile of spam. Spam can ruin your company's Internet footprint. Spam can also find its way into the depths of your website and stink up the whole place. It's especially embarrassing when you don't even know that you have spam on the bottom of your virtual shoe; here's how it got there.
 Is your web browser's home page looking drab and boring? Do you wish that you could change it to something fresh and exciting but you just don't know how to do it? Introducing Home Page Settings! By using Home Page Settings, you can give your Web Browser that fresh look you have always wanted, and the best part is that it's free!
Is your web browser's home page looking drab and boring? Do you wish that you could change it to something fresh and exciting but you just don't know how to do it? Introducing Home Page Settings! By using Home Page Settings, you can give your Web Browser that fresh look you have always wanted, and the best part is that it's free!
 The evolution of Google from a search engine company renting a garage, to one of the largest companies on the planet, is a story that can truly boggle the mind. One cause of Google's growth is their investment in developing new technology. This is the case with the Google Spanner, which is a new technology designed to manage Google's growth.
The evolution of Google from a search engine company renting a garage, to one of the largest companies on the planet, is a story that can truly boggle the mind. One cause of Google's growth is their investment in developing new technology. This is the case with the Google Spanner, which is a new technology designed to manage Google's growth.
 In 2011, Ponemon Research surveyed 583 U.S. businesses and found that 90% of respondents reported that their company's computers had been breached at least once by hackers within the past year; 77% of these companies felt like they were attacked multiple times within the same year. If your SMB does not have any protection from hackers, then your sensitive data is at serious risk.
In 2011, Ponemon Research surveyed 583 U.S. businesses and found that 90% of respondents reported that their company's computers had been breached at least once by hackers within the past year; 77% of these companies felt like they were attacked multiple times within the same year. If your SMB does not have any protection from hackers, then your sensitive data is at serious risk.
 If you never connected your PC to the internet, then you could get away with not updating any of your software. Do to the changing nature of the internet, new security threats are constantly attacking your computer. Internet browsers are your door to the internet and require constant updating in order to keep your PC protected from these threats.
If you never connected your PC to the internet, then you could get away with not updating any of your software. Do to the changing nature of the internet, new security threats are constantly attacking your computer. Internet browsers are your door to the internet and require constant updating in order to keep your PC protected from these threats.
 It always feels a bit peculiar to come across a fax machine still being used in the modern office. With all of our digital advancements, the fax machine should have gone the way of the floppy disk. Contrary to common sense, it is estimated that there are 131 million fax machines still in operation around the world.
It always feels a bit peculiar to come across a fax machine still being used in the modern office. With all of our digital advancements, the fax machine should have gone the way of the floppy disk. Contrary to common sense, it is estimated that there are 131 million fax machines still in operation around the world.
 The concept behind company time is simple enough: you are employed, and therefore expected to do whatever you agreed upon while "on the clock." To be fair, you are given a few breaks to attend to personal matters; yet, as easy to grasp as this seems, the average employee wastes two hours of company time per day on the internet.
The concept behind company time is simple enough: you are employed, and therefore expected to do whatever you agreed upon while "on the clock." To be fair, you are given a few breaks to attend to personal matters; yet, as easy to grasp as this seems, the average employee wastes two hours of company time per day on the internet.
 Are you compiling your New Year's resolution list and looking for some help to achieve your goals? If one of your resolutions is to spend less time goofing off on the internet and more time being productive, then we want to share with you a helpful app called Freedom that will help achieve your resolution.
Are you compiling your New Year's resolution list and looking for some help to achieve your goals? If one of your resolutions is to spend less time goofing off on the internet and more time being productive, then we want to share with you a helpful app called Freedom that will help achieve your resolution.
 Internet bandwidth is a precious resource, and the amount your office can use is limited to whatever internet service package your company is signed up for. If your office is running short on bandwidth, then you will need to upgrade to a bigger package, which will be expensive. Before you spend money on upgrading, you should consider internet monitoring.
Internet bandwidth is a precious resource, and the amount your office can use is limited to whatever internet service package your company is signed up for. If your office is running short on bandwidth, then you will need to upgrade to a bigger package, which will be expensive. Before you spend money on upgrading, you should consider internet monitoring.
 Have you ever stopped and wondered where the internet is housed? Maybe all the websites are on a skyscraper-sized router? Maybe the internet all fits inside your computer? Most of the information is actually stored in data center facilities all over the world, and the sheer size and complexity of these centers will boggle your mind.
Have you ever stopped and wondered where the internet is housed? Maybe all the websites are on a skyscraper-sized router? Maybe the internet all fits inside your computer? Most of the information is actually stored in data center facilities all over the world, and the sheer size and complexity of these centers will boggle your mind.
 Taking screenshots of your desktop is infinitely useful (including when you get a strange error that you can't seem to repeat when IT is standing by).. Although the process of taking a screenshot has always felt a bit more cumbersome than it needs to be due to the additional steps of opening editing software, formatting the image, and saving the file. Lightshot is a solution that simplifies the entire screenshot process.
Taking screenshots of your desktop is infinitely useful (including when you get a strange error that you can't seem to repeat when IT is standing by).. Although the process of taking a screenshot has always felt a bit more cumbersome than it needs to be due to the additional steps of opening editing software, formatting the image, and saving the file. Lightshot is a solution that simplifies the entire screenshot process.
 The 2012 holiday online shopping season is shaping up to be the biggest yet. Harris Interactive conducted a survey regarding this holiday season, and found that 51% of Americans plan on shopping online this year. Everybody has different reasons to shop online, 71% of respondents thought they could find better deals, and 31% want to simply avoid the crowds.
The 2012 holiday online shopping season is shaping up to be the biggest yet. Harris Interactive conducted a survey regarding this holiday season, and found that 51% of Americans plan on shopping online this year. Everybody has different reasons to shop online, 71% of respondents thought they could find better deals, and 31% want to simply avoid the crowds.
 Using a strong password with complex combinations of letters and numbers will go a long way in protecting your account, but passwords provide only one level of protection against hackers. Additional levels of security can be added with multi-factor authentication. This is the best protection available for your internet accounts, and major technology companies have recently made this a reality for the public.
Using a strong password with complex combinations of letters and numbers will go a long way in protecting your account, but passwords provide only one level of protection against hackers. Additional levels of security can be added with multi-factor authentication. This is the best protection available for your internet accounts, and major technology companies have recently made this a reality for the public.
 It's the information age. If you are always on the go, or you work as a member of a team, it helps if your work is accessible remotely. The ability to have relevant files on hand is nice and at times can be essential to the welfare of your business. Below are a few cloud-based options that could offer you or your company a solution for your remote file access needs.
It's the information age. If you are always on the go, or you work as a member of a team, it helps if your work is accessible remotely. The ability to have relevant files on hand is nice and at times can be essential to the welfare of your business. Below are a few cloud-based options that could offer you or your company a solution for your remote file access needs.
 Prominent companies falling victim to hacker has become all too common in the news. Some of the larger breaches in security involve the compromise of thousands of customers' information. Definitely not the kind of press you want, not to mention the irreparable damage to your business. This can be a little scary for a small business owner, especially if you consider that these large companies have the best cyber security money can buy.
Prominent companies falling victim to hacker has become all too common in the news. Some of the larger breaches in security involve the compromise of thousands of customers' information. Definitely not the kind of press you want, not to mention the irreparable damage to your business. This can be a little scary for a small business owner, especially if you consider that these large companies have the best cyber security money can buy.