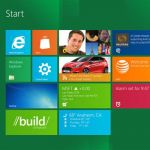
For corporations and individuals alike, computers are mandatory. Off-site, on-site, home portal access, and remote offices are more widespread than ever. The design of Windows 8 has given special consideration to businesses. Its format includes organization, availability, security, and compatibility that allow a more cohesive operating system. For small and medium businesses, Windows 8 will acclimate to their needs like no operating system ever before.
For corporations and individuals alike, computers are mandatory. Off-site, on-site, home portal access, and remote offices are more widespread than ever. The design of Windows 8 has given special consideration to businesses. Its format includes organization, availability, security, and compatibility that allow a more cohesive operating system. For small and medium businesses, Windows 8 will acclimate to their needs like no operating system ever before.
Directive Blogs
 Someone is laughing their way to the bank when it comes to printer ink prices, but it isn't small businesses. A gallon of printer ink can cost a minimum of $2,000. Granted, Upstate New York small businesses usually don't purchase a gallon of ink at a time. Suddenly, walking to the office printer and finding two copies of a 50-page .PDF file that had been printed accidentally and left for recycling would take on new significance.
Someone is laughing their way to the bank when it comes to printer ink prices, but it isn't small businesses. A gallon of printer ink can cost a minimum of $2,000. Granted, Upstate New York small businesses usually don't purchase a gallon of ink at a time. Suddenly, walking to the office printer and finding two copies of a 50-page .PDF file that had been printed accidentally and left for recycling would take on new significance.
 Android users may have some cause for concern. Considering its surging popularity, there is going to be a certain amount of rouge applications and other malware that targets the top iPhone OS. According to the popular anti-virus maker, Trend Micro, there are at least 20,000 applications that are malicious that target Google's Android OS. That is an increase of at least 400% since the beginning of 2012. By Christmas of this year, experts have given a conservative estimate that puts potential malware and rouge apps at around 150,000 different applications.
Android users may have some cause for concern. Considering its surging popularity, there is going to be a certain amount of rouge applications and other malware that targets the top iPhone OS. According to the popular anti-virus maker, Trend Micro, there are at least 20,000 applications that are malicious that target Google's Android OS. That is an increase of at least 400% since the beginning of 2012. By Christmas of this year, experts have given a conservative estimate that puts potential malware and rouge apps at around 150,000 different applications.
 Business owners and employees alike are inundated with email. According to a study done in 2011, as much as half of an employee's day is spent sifting through their email, and as the study puts it, "necessary, yet unproductive tasks." Freeing up that time and spending less time managing email can open a worker up to more productivity. Here's a quick and simple way to start organizing your inbox to free yourself from your email and get more done!
Business owners and employees alike are inundated with email. According to a study done in 2011, as much as half of an employee's day is spent sifting through their email, and as the study puts it, "necessary, yet unproductive tasks." Freeing up that time and spending less time managing email can open a worker up to more productivity. Here's a quick and simple way to start organizing your inbox to free yourself from your email and get more done!
 Nature can be pretty impressive. It can interrupt the day-to-day operations of businesses, cause major damage, and cost your business in expensive downtime. Having a good business continuity plan (and ensuring you have it set in place) can make or break your company when mother nature comes knocking at your door.
Nature can be pretty impressive. It can interrupt the day-to-day operations of businesses, cause major damage, and cost your business in expensive downtime. Having a good business continuity plan (and ensuring you have it set in place) can make or break your company when mother nature comes knocking at your door.
 Businesses are inundated with information, programs and quick solutions on making companies green. Some of these suggestions can be implemented today, others my take more time. However, going green, can save your organization significant amounts of money. Wasted paper, plastic cups and wasted electricity are all money literally thrown away. Here a few suggestions to get you off on the right foot:
Businesses are inundated with information, programs and quick solutions on making companies green. Some of these suggestions can be implemented today, others my take more time. However, going green, can save your organization significant amounts of money. Wasted paper, plastic cups and wasted electricity are all money literally thrown away. Here a few suggestions to get you off on the right foot:
 Protecting your business network from the threats lurking on the Internet is crucial for a small business. Threats of all shapes, sizes, and severities are out there and if they get into your network you could be looking at some serious issues ranging from data theft to extended downtime. Fortunately, there is a single solution available that can deliver a total security package to protect your business from virtually any outside threat.
Protecting your business network from the threats lurking on the Internet is crucial for a small business. Threats of all shapes, sizes, and severities are out there and if they get into your network you could be looking at some serious issues ranging from data theft to extended downtime. Fortunately, there is a single solution available that can deliver a total security package to protect your business from virtually any outside threat.
Does it seem like every day your network is suffering from a different issue? How about the same old issues that keep coming back? Think about how much time is wasted every day while you and your employees have to cope with viruses, malware, and oddball technology issues. What if we told you there is an easy solution that will eliminate 99% of these problems?
 Last time we talked about ways to standardize your Microsoft Word documents so the look and feel remains consistent throughout the document and between multiple documents. Today we are going to look at a more advanced trick that will let you take predefined content and data and allow yourself to pick and choose when you use it in a document.
Last time we talked about ways to standardize your Microsoft Word documents so the look and feel remains consistent throughout the document and between multiple documents. Today we are going to look at a more advanced trick that will let you take predefined content and data and allow yourself to pick and choose when you use it in a document.
 Do your documents look a little bland? Representing your brand is important whenever you do any corresponding, whether you are just using letter heads or creating custom documentation or project proposals. Microsoft Word makes it simple to standardize the look of your documents so your brand can shine through no matter what type of document you are creating.
Do your documents look a little bland? Representing your brand is important whenever you do any corresponding, whether you are just using letter heads or creating custom documentation or project proposals. Microsoft Word makes it simple to standardize the look of your documents so your brand can shine through no matter what type of document you are creating.
 Modern technology makes it easy to get things done from anywhere, allowing employees to work while on the go. One of the caveats of working while traveling is keeping focused. Unlike sitting in the office where an employee can focus, traveling puts workers in busy airports, coffee shops, or poolside at a hotel. Here are a few tips to help you focus on tasks while on the road.
Modern technology makes it easy to get things done from anywhere, allowing employees to work while on the go. One of the caveats of working while traveling is keeping focused. Unlike sitting in the office where an employee can focus, traveling puts workers in busy airports, coffee shops, or poolside at a hotel. Here are a few tips to help you focus on tasks while on the road.
 Having strong passwords for your online accounts is very important, but sometimes you may want a little more protection in the event your password gets stolen or someone forces their way through it. If you use Google's Gmail service, you can set up your account, then you will need two forms of authentication to get into your email.
Having strong passwords for your online accounts is very important, but sometimes you may want a little more protection in the event your password gets stolen or someone forces their way through it. If you use Google's Gmail service, you can set up your account, then you will need two forms of authentication to get into your email.
 Do you work in an office and sit in front of a desk all day? Chances are, you have experienced back pain or tight shoulders. Maybe you get headaches from staring at the computer all day. Well today we will discuss some tips on how to reduce the negative effects that office work can have on your body. Working these tips into your day can have a dramatic effect on your mental and physical health and you will feel all the better for it.
Do you work in an office and sit in front of a desk all day? Chances are, you have experienced back pain or tight shoulders. Maybe you get headaches from staring at the computer all day. Well today we will discuss some tips on how to reduce the negative effects that office work can have on your body. Working these tips into your day can have a dramatic effect on your mental and physical health and you will feel all the better for it.
 Think back a few years ago before the Apple ipad (if you are in the medical field, there is a good chance you'll relate to this). Remember back when "tablet" computers were essentially laptops sans-keyboard with little plastic styluses? Now kindergarteners are using tablets instead of chalk boards. What happened?
Think back a few years ago before the Apple ipad (if you are in the medical field, there is a good chance you'll relate to this). Remember back when "tablet" computers were essentially laptops sans-keyboard with little plastic styluses? Now kindergarteners are using tablets instead of chalk boards. What happened?
 Today, your employees are more and more technologically empowered. With the consumer electronics market teaming with amazing gadgets and high-end devices, cool tech is no longer reserved for fancy geek toys. With employees bringing in their own smartphones and tablets, mobile security becomes a big concern for small businesses.
Today, your employees are more and more technologically empowered. With the consumer electronics market teaming with amazing gadgets and high-end devices, cool tech is no longer reserved for fancy geek toys. With employees bringing in their own smartphones and tablets, mobile security becomes a big concern for small businesses.
S mall business owners and Entrepreneurs wear many hats. They have certain strengths and a drive to make money using the skills that they have. But there are many facets to running a business. Someone needs to do the accounting, the networking, inventory, manage employees, do sales calls and more. Then, someone needs to manage the technology.
mall business owners and Entrepreneurs wear many hats. They have certain strengths and a drive to make money using the skills that they have. But there are many facets to running a business. Someone needs to do the accounting, the networking, inventory, manage employees, do sales calls and more. Then, someone needs to manage the technology.
 The consumer electronics market is inundated with countless mobile devices with flashy interfaces, sleek profiles, and names that are more ridiculous than most car makes. Understandably, it's hard to keep up and when picking out a smartphone for yourself or your business, the demos at the store don't give you much of an insight. Here's an extensive cheat sheet on what to look for when making a new smartphone purchase.
The consumer electronics market is inundated with countless mobile devices with flashy interfaces, sleek profiles, and names that are more ridiculous than most car makes. Understandably, it's hard to keep up and when picking out a smartphone for yourself or your business, the demos at the store don't give you much of an insight. Here's an extensive cheat sheet on what to look for when making a new smartphone purchase.
 Technology is changing quickly and businesses are seeing a wide variety of options replacing traditional IT methodology that is driving change and productivity to businesses of all sizes. It's getting easier to take work with you with mobile devices and hosted services, but are these just expensive new toys or do they provide serious benefits to businesses?
Technology is changing quickly and businesses are seeing a wide variety of options replacing traditional IT methodology that is driving change and productivity to businesses of all sizes. It's getting easier to take work with you with mobile devices and hosted services, but are these just expensive new toys or do they provide serious benefits to businesses?
 There comes a time when you are looking at a new laptop and you are asked the question: Do you want a Solid State Drive, or a traditional Hard Disk Drive? Well here is a quick run-down of both technologies in the hopes of shedding some light on the issue. By the time you are done reading this article, you will be better able to answer that question.
There comes a time when you are looking at a new laptop and you are asked the question: Do you want a Solid State Drive, or a traditional Hard Disk Drive? Well here is a quick run-down of both technologies in the hopes of shedding some light on the issue. By the time you are done reading this article, you will be better able to answer that question.
 Microsoft Office and Windows 7 provide many keyboard shortcuts that can improve your ability to multitask and get things accomplished quickly. Most of these shortcuts will work in previous versions, like Windows XP, Vista and the Microsoft Server Operating Systems as well. Give them a try, and the next time your tech comes by, be sure to show off your new skills.
Microsoft Office and Windows 7 provide many keyboard shortcuts that can improve your ability to multitask and get things accomplished quickly. Most of these shortcuts will work in previous versions, like Windows XP, Vista and the Microsoft Server Operating Systems as well. Give them a try, and the next time your tech comes by, be sure to show off your new skills.
 Computer viruses are pretty serious threats, and can cause huge expensive issues for businesses. Many cases of malware and computer viruses actually use your computer to commit real crimes. The FBI states that hundreds of thousands of people will likely lose the ability to surf the web if they have a particular piece of malware.
Computer viruses are pretty serious threats, and can cause huge expensive issues for businesses. Many cases of malware and computer viruses actually use your computer to commit real crimes. The FBI states that hundreds of thousands of people will likely lose the ability to surf the web if they have a particular piece of malware.
Techies get pretty excited over neat new gadgets and integrating them into day-to-day life, so when we heard about Sony's new SmartWatch, it caught our attention. Will smart watches become the next thing in the not-so-distant future or will they become flops like New Coke and Betamax?
 Nobody likes thinking or talking about this (except maybe if you are in the insurance business), but businesses are fragile entities. Enough hardship and loss will greatly weaken the foundation that keeps the business running smoothly. What if your business suffered from a fire, devastating flood, or even a misfortunate bolt of lightning that destroys your server? Would you be able to pick up the pieces and start over?
Nobody likes thinking or talking about this (except maybe if you are in the insurance business), but businesses are fragile entities. Enough hardship and loss will greatly weaken the foundation that keeps the business running smoothly. What if your business suffered from a fire, devastating flood, or even a misfortunate bolt of lightning that destroys your server? Would you be able to pick up the pieces and start over?
 Global Payments, a credit card processing firm, announced that as many as 1.5 million credit card numbers were stolen due to a security breach last month. Issues like this seem more and more common place in the news and it is important to know what to do if you suspect that your credit card has been hacked.
Global Payments, a credit card processing firm, announced that as many as 1.5 million credit card numbers were stolen due to a security breach last month. Issues like this seem more and more common place in the news and it is important to know what to do if you suspect that your credit card has been hacked.
 We've seen a pattern over the years as Microsoft releases operating systems where every other operating system is great, while the releases in between are somewhat lacking. Windows 98 was pretty solid, as was XP, however the middle-child Windows ME? Not so much. This kind of progression is usually reserved for Star Trek films. What does this mean for Windows 8, the successor of the great Windows 7?
We've seen a pattern over the years as Microsoft releases operating systems where every other operating system is great, while the releases in between are somewhat lacking. Windows 98 was pretty solid, as was XP, however the middle-child Windows ME? Not so much. This kind of progression is usually reserved for Star Trek films. What does this mean for Windows 8, the successor of the great Windows 7?
Most digital cameras produce very high resolution images, which is fantastic for printing, but higher quality image files means larger file sizes, and these days images aren't quite as portable as they used to be. Fortunately, Outlook has a great feature to reduce the size of image attachments for you.
Over the past couple years we've seen a huge shift in the reliability and functionality of the tablet PC. What was once was a struggling market of just a few overpriced, bulky, devices that were neither practical nor stylish has become the next big consumer product. Tablets have been making it into the business world, supplementing smartphones as a new addition to mobile arsenals. We're going to highlight the best two tablets on the market that you can buy right now.
There's a lot of buzz around Windows 8 for technology lovers, and for good reason. Microsoft is making it's next operating system dramatically different than previous incantations, and it sounds like we'll be seeing a lot of this OS in the future on a lot of different platforms, ranging from desktops and notebooks to tablets, and possibly even more.
We've been blogging a bit about ways to prepare for laptop theft and what to do if a company laptop is actually stolen. Laptop and mobile device theft is a widespread issue for businesses and can lead to data theft which can be extremely costly; much more than the mere price of the hardware. This issue is all too familiar with NASA, which admits that thousands of mobile device theft incidents have occurred over the past few years.
To most people, computer viruses are things that cause annoyance, downtime, and cost money to fix. That's pretty bad on it's own, but some viruses are much more complex than others and can be far more dangerous. Let's look at Stuxnet, coined as the first weapon made entirely out of code, and why it is so frightening.
Business owners, this one is definitely for you. You've probably experienced the fact that shaving expenses here and there can lead to more flexibility and long-term savings, but at what cost? Are you limiting your company by nixing those extra services and costs? Sometimes you can get more and still save money. Let's look at a few ways Upstate New York businesses can do just that.
The problem with carrying around an expensive, portable piece of equipment is that it's possible for someone to pick it up and run with it. According to LoJack, a security firm that focuses on stolen property, two million laptops are stolen each year. What should you do if you are a victim of laptop theft?
Unfortunately cell phone service providers are discovering that smartphone users love their bandwidth. With the majority of carriers dropping unlimited data plans, when a user goes over their limit massive charges can apply. Let's cover a few tips to limit the amount of bandwidth you use on your smartphone.
Google has gradually become a major part in our lives. Most of us use it every day to find answers, research products, and determine what Upstate New York restaurants are open on a Sunday night. Google is on our phones, we watch videos on YouTube, and we get from point A to point B with Google maps. So what does Google know about us?
Whether you are going completely paperless or just want to send digital copies of paper documents, there are a lot of solutions out there for quickly scanning a doc and converting it to PDF for easy archiving and emailing, but most of these devices aren't exactly portable. Here's a quick way to digitize documents with the camera on your Android smartphone.
There has been a growing trend where businesses are allowing more employees to work from home or other remote locations. Technology makes this possibly by letting users remote into their work environment securely as if they were sitting at their desk at the office. VoIP phone solutions can even bring the worker's office phone to them, no matter where they are.
Twitter is a fantastic networking resource for professionals, brands, and businesses. Having a strong presence on Twitter can mean more traffic to your website and an easy way to get in touch with customers and prospects. The hardest thing about diving into social media is knowing what to say. Here's a quick list with a few ideas to get you started.
Internet privacy is no new issue. Between malicious hackers trying to breach private information, governments trying to regulate it, and organizations trying to track as many metrics as they can, the Internet continues to chug along for the most part just fine. Are YOU concerned about Internet privacy?
Last time we went over how to dress up your PowerPoint presentations with SmartArt, a feature in many Microsoft Office applications. Today we're going to be showing you how to create charts to display various types of data in PowerPoint, but like before, these will work much the same in other Office products such as Microsoft Word.
Nobody wants to spend more than they have to, especially when it comes to those necessary evils like bills, utilities, insurance, and the general costs of keeping things running smoothly. At Directive, our goal is to provide outstanding enterprise-level solutions for small business prices. Let's talk about a few ways to cut long term IT costs.
This has been a pretty common topic for us on the Directive blog. We've seen a lot of Upstate New York clients and customers suffer the consequences when online retailers and other account providers experience a security breach. It is equally vital for consumers to know what to do in the event of a security breach as it is the company that is actually breached.
This month Google announced that their search results will now contain personal results from friends and connections made in Google+. Twitter, the real-time searchable social network, publicly announced that they thought this was not a good idea. Will personalizing search results make for a better Google experience or will it hurt? Let's take a look.
CES, a massive consumer electronics tradeshow, always presents some neat new gadgets and doodads to ogle over, and this year was no exception. One of the biggest hits at the event this year was Samsung's Transparent Smart Window. Describing it doesn't do it justice, hit the jump to see a video of it in action!
Hard drives have been getting bigger (capacity-wise) and cheaper over the past decade which is great news for everyone. Toshiba predicts that in 2012 that over 2 zettabytes (2 trillion gigabytes!) of data will be created and replicated (double from 2010). While costs are going down, data growth is still a challenge for data centers and IT administrators.
On the topic of identity theft, social media accounts are becoming a high target for hackers, especially for spreading malicious viruses. To some, losing control over their Facebook or Twitter accounts could be just as devastating as having their credit card stolen. Trouble is, for many users, having one login account stolen means hackers have access to their other accounts too.
When you mention the term 'disaster recovery,' most people think about the big ground-shattering events like earthquakes, fires, floods, tropical storms, etc. While these natural events are certainly disasters and devastating in their own right, smaller things can constitute as a disaster for your business, and they aren't seasonal.
Your identity has quite a lot of value, especially in the wrong hands. Security firm ZoneAlarm put together some numbers in 2011 concerning identity fraud, and it even shocked us. Let's talk about a few of these statistics and what it means.