Directive Blogs
 The computer mouse makes navigating your PC easy. However, the mouse isn't always the most efficient way to get computer work done. By taking advantage of keyboard shortcuts, you can shave precious seconds off your workflow and wow your coworkers with your computer prowess. Here are five time-saving keyboard shortcuts to get you started.
The computer mouse makes navigating your PC easy. However, the mouse isn't always the most efficient way to get computer work done. By taking advantage of keyboard shortcuts, you can shave precious seconds off your workflow and wow your coworkers with your computer prowess. Here are five time-saving keyboard shortcuts to get you started.
 With the holiday shopping season winding down, it's the busiest time of the for data collecting companies that compile information on the purchases you make. Are you aware of the extent that your purchases are being tracked? Knowing about data collection may make you want to buy all of your presents with cash.
With the holiday shopping season winding down, it's the busiest time of the for data collecting companies that compile information on the purchases you make. Are you aware of the extent that your purchases are being tracked? Knowing about data collection may make you want to buy all of your presents with cash.
 Social media has become a big part of business, and Twitter is one of the top sites. You may know Twitter as an app that lets you send short messages to "followers," however, there's so much more to this useful tool that has been embraced by 218.3 million users worldwide. Let's take a closer look at Twitter and how to utilize it for your business.
Social media has become a big part of business, and Twitter is one of the top sites. You may know Twitter as an app that lets you send short messages to "followers," however, there's so much more to this useful tool that has been embraced by 218.3 million users worldwide. Let's take a closer look at Twitter and how to utilize it for your business.
 2013 might go down in history as the bridge year between high-end handheld electronics and wearable gadgets that offer enhanced flexibility and access, but for now, the best electronics for communication, collaboration, and convenience are the handheld computers that we've learned to lean on. Below are some of the top smartphone options on the market.
2013 might go down in history as the bridge year between high-end handheld electronics and wearable gadgets that offer enhanced flexibility and access, but for now, the best electronics for communication, collaboration, and convenience are the handheld computers that we've learned to lean on. Below are some of the top smartphone options on the market.
 Around the holidays, we are often reminded how important it is to give, and graciously receive good will. One story that sparks these thoughts is Charles Dickens' classic tale, A Christmas Carol. For those of you who are not familiar with the story, Ebenezer Scrooge, a wealthy, shrewd miser gets visits from the three spirits of Christmas after he believes that Christmas is no better than a day of wasted profits. Scared out of his wits by the legacy he would leave behind if he didn't change, Scrooge's transforms into a generous and caring man, literally overnight. This story has been told several different ways over a century, but the premise is still the same, profits aren't always what matters most.
Around the holidays, we are often reminded how important it is to give, and graciously receive good will. One story that sparks these thoughts is Charles Dickens' classic tale, A Christmas Carol. For those of you who are not familiar with the story, Ebenezer Scrooge, a wealthy, shrewd miser gets visits from the three spirits of Christmas after he believes that Christmas is no better than a day of wasted profits. Scared out of his wits by the legacy he would leave behind if he didn't change, Scrooge's transforms into a generous and caring man, literally overnight. This story has been told several different ways over a century, but the premise is still the same, profits aren't always what matters most.
 New York Times tech column writer, David Pogue, recently presented a TED talk, in which he suggested his top ten time-saving technology tips. Each of David's tips were incredibly simple, but understated and carry the potential to save tech users time and effort. Do you know about these time-saving tips?
New York Times tech column writer, David Pogue, recently presented a TED talk, in which he suggested his top ten time-saving technology tips. Each of David's tips were incredibly simple, but understated and carry the potential to save tech users time and effort. Do you know about these time-saving tips?
 Big changes are happening in the world of technology, and it's important that your business stays on top of these changes in order to stay competitive. By taking advantage of the latest trends, you will be provided with solutions designed to maximize profits. Here are five of the latest trends you need to watch for in 2014.
Big changes are happening in the world of technology, and it's important that your business stays on top of these changes in order to stay competitive. By taking advantage of the latest trends, you will be provided with solutions designed to maximize profits. Here are five of the latest trends you need to watch for in 2014.
 For most small business owners, your average week includes several moments where you look at your expense sheet and search for ways to cut costs and improve the profitability, and thus, the sustainability of your company. Around the holidays, when business picks up for everyone, some small businesses run into problems that stunt their net profitability. The inability to spend the money that larger companies can, will often result in handcuffing a business' ability to compete.
For most small business owners, your average week includes several moments where you look at your expense sheet and search for ways to cut costs and improve the profitability, and thus, the sustainability of your company. Around the holidays, when business picks up for everyone, some small businesses run into problems that stunt their net profitability. The inability to spend the money that larger companies can, will often result in handcuffing a business' ability to compete.
 One IT problem that you may have heard about is server noise. A server unit is a noisy piece of equipment because it comes with multiple fans used to keep the machine cool. One big reason why servers are banished to their own room is because of all the noise they make. Here's what you can do to quiet your servers.
One IT problem that you may have heard about is server noise. A server unit is a noisy piece of equipment because it comes with multiple fans used to keep the machine cool. One big reason why servers are banished to their own room is because of all the noise they make. Here's what you can do to quiet your servers.
 It's time once again for holiday shopping, and you've got a plethora of technology choices before you. With so many options, it's easy to get confused and grab the first thing you come across. To help you avoid the stress of shopping for technology this holiday season, we've prepared for you this guide so you can be sure that you're purchasing the best item for people on your list.
It's time once again for holiday shopping, and you've got a plethora of technology choices before you. With so many options, it's easy to get confused and grab the first thing you come across. To help you avoid the stress of shopping for technology this holiday season, we've prepared for you this guide so you can be sure that you're purchasing the best item for people on your list.
 Concocting a comprehensive and concise marketing strategy is extremely important for any small business. Across the board, the average company uses between 8%-to-15% of their gross revenue to reinvest into marketing themselves. When you consider how large of a percentage of an organization's workable capital that really is, you'll begin to understand why companies are trying to find a solutions to cut their marketing costs. They need not look any further than the palm of their hand to find that very solution.
Concocting a comprehensive and concise marketing strategy is extremely important for any small business. Across the board, the average company uses between 8%-to-15% of their gross revenue to reinvest into marketing themselves. When you consider how large of a percentage of an organization's workable capital that really is, you'll begin to understand why companies are trying to find a solutions to cut their marketing costs. They need not look any further than the palm of their hand to find that very solution.
 Two of the latest trends in business culture are environmentally friendly green campaigns and Bring Your Own Device (BYOD) work environments. There are a few ways that a BYOD system can contribute to the success of your company's green campaign, as they both seek to use technology to increase everyday efficiency at the office.
Two of the latest trends in business culture are environmentally friendly green campaigns and Bring Your Own Device (BYOD) work environments. There are a few ways that a BYOD system can contribute to the success of your company's green campaign, as they both seek to use technology to increase everyday efficiency at the office.
 It's nice to get a shiny new computer that's fast, powerful, and has all the latest features. Before you install your new machine, you have to make a decision about what to do with your old one. Your old computer has been a faithful friend over the years so you may feel bad pitching it to the curb; instead, consider giving it a new home.
It's nice to get a shiny new computer that's fast, powerful, and has all the latest features. Before you install your new machine, you have to make a decision about what to do with your old one. Your old computer has been a faithful friend over the years so you may feel bad pitching it to the curb; instead, consider giving it a new home.
 Working in the IT industry means embracing change and the latest technology trends. Doing the same thing day-in and day-out is a luxury we don't have, and frankly, sounds kind of boring. Since computers were first invented, there's been a need to service them. Here's a look at how the IT service industry has changed over the past 50 years.
Working in the IT industry means embracing change and the latest technology trends. Doing the same thing day-in and day-out is a luxury we don't have, and frankly, sounds kind of boring. Since computers were first invented, there's been a need to service them. Here's a look at how the IT service industry has changed over the past 50 years.
 If you've never taken advantage of remote support to remedy an IT problem, then you're likely doing IT support the hard way by having a technician physically take care of every issue. While it's always nice to chat with your friendly tech, you may be able to save yourself a whole lot of time and money by taking care of the issue with remote support.
If you've never taken advantage of remote support to remedy an IT problem, then you're likely doing IT support the hard way by having a technician physically take care of every issue. While it's always nice to chat with your friendly tech, you may be able to save yourself a whole lot of time and money by taking care of the issue with remote support.
 You may feel like your computer network is immune to data loss, but according to a study by Blackblaze.com, 46% of users experience data loss every year. Whether it's from something big like a natural disaster, or minor like improperly removing a flash drive, every form of data loss is costly and can be prevented with a data backup plan.
You may feel like your computer network is immune to data loss, but according to a study by Blackblaze.com, 46% of users experience data loss every year. Whether it's from something big like a natural disaster, or minor like improperly removing a flash drive, every form of data loss is costly and can be prevented with a data backup plan.
 Mobile technology use is growing at such a fast rate that it's proving to be more than a trend. In the U.S., 56% of adults own a smartphone, and for businesses with an Internet presence, 31% of conversions took place over a mobile device last year. This mobile revolution has huge implications for how your business reaches new customers.
Mobile technology use is growing at such a fast rate that it's proving to be more than a trend. In the U.S., 56% of adults own a smartphone, and for businesses with an Internet presence, 31% of conversions took place over a mobile device last year. This mobile revolution has huge implications for how your business reaches new customers.
 On December 3, 2013, security company Trustwave discovered over two million stolen user passwords for popular online services like Facebook, LinkedIn, Google, Twitter, Yahoo, and 93,000 other websites. There's a high probability that you use one of the services affected by the hack. Is your personal information compromised?
On December 3, 2013, security company Trustwave discovered over two million stolen user passwords for popular online services like Facebook, LinkedIn, Google, Twitter, Yahoo, and 93,000 other websites. There's a high probability that you use one of the services affected by the hack. Is your personal information compromised?
 Microsoft is well known for their software, but manufacturing tablet computers is a new venture for the tech giant. It's been almost a year since Microsoft's signature tablet the Surface Pro was released, and now the second generation of Surface, the Surface Pro 2, is available. Here's an overview on how the new tablet stacks up.
Microsoft is well known for their software, but manufacturing tablet computers is a new venture for the tech giant. It's been almost a year since Microsoft's signature tablet the Surface Pro was released, and now the second generation of Surface, the Surface Pro 2, is available. Here's an overview on how the new tablet stacks up.
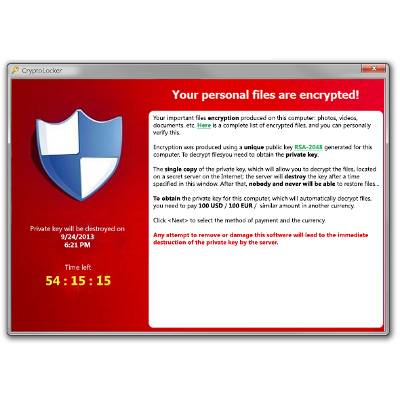 In September, a new ransomware came on the scene and it's been wreaking havoc on computers the world over ever since. Given the name CryptoLocker, it's capable of taking over your system, encrypting your files, and literally holding your data ransom in order to extort money from you. If you don't pay, then your files are deleted. What's an honest business to do against such a threat?
In September, a new ransomware came on the scene and it's been wreaking havoc on computers the world over ever since. Given the name CryptoLocker, it's capable of taking over your system, encrypting your files, and literally holding your data ransom in order to extort money from you. If you don't pay, then your files are deleted. What's an honest business to do against such a threat?
 Installing a VPN solution is perhaps the best move you can make to ensure the security of your network, and the files that it transports. Whether you send files between your workplace and home or to remote locations around the globe, VPN can help ensure their safety. What exactly is VPN, and why should your company be using it?
Installing a VPN solution is perhaps the best move you can make to ensure the security of your network, and the files that it transports. Whether you send files between your workplace and home or to remote locations around the globe, VPN can help ensure their safety. What exactly is VPN, and why should your company be using it?
 It's important to understand how long your hard drive will last so you can minimize the risk of data loss from a drive failure. Disk hard drives are made up of tiny parts with platters that rotate at thousands of RPMs, which makes it the most vulnerable component of your PC. How much life is left on your server's hard drive?
It's important to understand how long your hard drive will last so you can minimize the risk of data loss from a drive failure. Disk hard drives are made up of tiny parts with platters that rotate at thousands of RPMs, which makes it the most vulnerable component of your PC. How much life is left on your server's hard drive?
 Wired telephone service, also known as the Public Switched Telephone Network (PSTN), is seemingly nearing their extinction. This is thanks to the more economical and convenient Voice over Internet Protocol (VoIP) telephone option. Until recently, nearly every American home was connected to the PSTN, but by 2015, this option will see a 75% decrease. What does this mean for your business?
Wired telephone service, also known as the Public Switched Telephone Network (PSTN), is seemingly nearing their extinction. This is thanks to the more economical and convenient Voice over Internet Protocol (VoIP) telephone option. Until recently, nearly every American home was connected to the PSTN, but by 2015, this option will see a 75% decrease. What does this mean for your business?
 Language is one of the biggest contributors to determining office culture. For example, a workplace where the management motivates with threats will be a completely different environment than an office where encouragement is liberally applied. The allowance or forbiddance of swearing is another major indicator of your company's culture. How does the language in your office reflect your company's values?
Language is one of the biggest contributors to determining office culture. For example, a workplace where the management motivates with threats will be a completely different environment than an office where encouragement is liberally applied. The allowance or forbiddance of swearing is another major indicator of your company's culture. How does the language in your office reflect your company's values?
 By now the vast majority of people have settled into using the Internet as a 24-hour shopping center, where almost anything imaginable can be purchased and shipped right to your door. From goods to services, everything under the sun has a digital price tag. While most of us have used a credit card to buy something online, many of us have alternatively chosen a more secure option, especially when closing deals with individuals on online auction sites like eBay. That option has traditionally been PayPal, which in many ways, has helped to revolutionize the way people transfer money. In fact, PayPal has been so successful, and essential to eBay's success, that eBay bought the company in 2002.
By now the vast majority of people have settled into using the Internet as a 24-hour shopping center, where almost anything imaginable can be purchased and shipped right to your door. From goods to services, everything under the sun has a digital price tag. While most of us have used a credit card to buy something online, many of us have alternatively chosen a more secure option, especially when closing deals with individuals on online auction sites like eBay. That option has traditionally been PayPal, which in many ways, has helped to revolutionize the way people transfer money. In fact, PayPal has been so successful, and essential to eBay's success, that eBay bought the company in 2002.
 When considering network and computing infrastructure security for your business, you don't usually think about about alternative routes of delivery for these solutions; and especially don't consider that this technology is available without the traditional appliance. Now, comprehensive security solutions for your network, server, and end-user is available as a service, in the cloud.
When considering network and computing infrastructure security for your business, you don't usually think about about alternative routes of delivery for these solutions; and especially don't consider that this technology is available without the traditional appliance. Now, comprehensive security solutions for your network, server, and end-user is available as a service, in the cloud.
 We hope that this isn't the first time you've heard about Microsoft ending support for their popular Windows XP OS on April 8, 2014. Microsoft has been warning users of this "death date" for years, yet we still come across businesses and consumers that are just now getting the memo. You may have to help get the message out!
We hope that this isn't the first time you've heard about Microsoft ending support for their popular Windows XP OS on April 8, 2014. Microsoft has been warning users of this "death date" for years, yet we still come across businesses and consumers that are just now getting the memo. You may have to help get the message out!
 The importance of backing up your company's data cannot be stressed enough. Data is your business' most valuable asset, as evidenced by the fact that companies unable to access their data for ten days after a major disaster (like Hurricane Sandy that hit the mid atlantic and northeast U.S) will not survive the next fiscal year. Here's how to protect your business with data backup.
The importance of backing up your company's data cannot be stressed enough. Data is your business' most valuable asset, as evidenced by the fact that companies unable to access their data for ten days after a major disaster (like Hurricane Sandy that hit the mid atlantic and northeast U.S) will not survive the next fiscal year. Here's how to protect your business with data backup.
 The Internet certainly has changed the way we live, work, shop, and communicate. We may think we're superior to previous generations because of all our Internet-based technology, but we have video proof that the Internet was actually conceptualized in 1969. In many ways, our parents and grandparents were spot on with their predictions. In other ways, not so much.
The Internet certainly has changed the way we live, work, shop, and communicate. We may think we're superior to previous generations because of all our Internet-based technology, but we have video proof that the Internet was actually conceptualized in 1969. In many ways, our parents and grandparents were spot on with their predictions. In other ways, not so much.
 Since the late 1990s, digital information, music, movies, software, and content has been at risk of being illegally shared worldwide for free. Peer-to-peer file sharing has forced entire industries to shift the way they do business as they try to counteract the illegal practice. The new Copyright Alert System will attempt to quell illegal file sharing.
Since the late 1990s, digital information, music, movies, software, and content has been at risk of being illegally shared worldwide for free. Peer-to-peer file sharing has forced entire industries to shift the way they do business as they try to counteract the illegal practice. The new Copyright Alert System will attempt to quell illegal file sharing.
 How does it make you feel having to call IT support? If you've never talked with one of our IT technicians, then you may think of the stereotypical scenario of dealing with an incoherent foreigner and dread making the call. We feel IT Support should be quick, easy, and resolve the problem, not test the limits of your patience.
How does it make you feel having to call IT support? If you've never talked with one of our IT technicians, then you may think of the stereotypical scenario of dealing with an incoherent foreigner and dread making the call. We feel IT Support should be quick, easy, and resolve the problem, not test the limits of your patience.
 It's no secret that Microsoft is trying to implement a full court press regarding the Windows RT operating system by trying to get it on as many tablets and phones as possible. However up until this point the only company still producing these devices was Microsoft itself. Now Nokia has entered the fray with their Lumia 2520. Microsoft recently purchase Nokia, however, the merger will not be complete until sometime next year, so this still feels, looks like, and operates the way you would expect a Nokia product to.
It's no secret that Microsoft is trying to implement a full court press regarding the Windows RT operating system by trying to get it on as many tablets and phones as possible. However up until this point the only company still producing these devices was Microsoft itself. Now Nokia has entered the fray with their Lumia 2520. Microsoft recently purchase Nokia, however, the merger will not be complete until sometime next year, so this still feels, looks like, and operates the way you would expect a Nokia product to.
 Thanks to cloud computing technology, many businesses are taking advantage of having a mobile workforce by allowing their staff to work from home. Working from home can be beneficial by making workers more productive, saving employees' time and money from commuting, and increasing worker satisfaction, but how can you know for sure if work is really getting done?
Thanks to cloud computing technology, many businesses are taking advantage of having a mobile workforce by allowing their staff to work from home. Working from home can be beneficial by making workers more productive, saving employees' time and money from commuting, and increasing worker satisfaction, but how can you know for sure if work is really getting done?
 After you've finished with that incriminating file (you know which file we're talking about), you will drag and drop it into the Recycling Bin. You may think that just because you selected "Empty Recycling Bin" that the evidence is gone forever, but that's not exactly how the Recycling Bin works. You will need a more permanent solution to completely cover your tracks.
After you've finished with that incriminating file (you know which file we're talking about), you will drag and drop it into the Recycling Bin. You may think that just because you selected "Empty Recycling Bin" that the evidence is gone forever, but that's not exactly how the Recycling Bin works. You will need a more permanent solution to completely cover your tracks.
 Do you have what it takes to win the annual National Texting Championship? 17-year-old Austin Wierschke has the texting speed, dexterity, and accuracy to be crowned the most recent texting champion, an accomplishment accredited to sending 500 texts a day for training! This is a major achievement for young Alex, but does it translate to a hirable skill?
Do you have what it takes to win the annual National Texting Championship? 17-year-old Austin Wierschke has the texting speed, dexterity, and accuracy to be crowned the most recent texting champion, an accomplishment accredited to sending 500 texts a day for training! This is a major achievement for young Alex, but does it translate to a hirable skill?
 One of the biggest time wasters we all face is sorting through our email inbox. This is a tedious task made worse because you have to sort through emails from the same sources every day, like newsletters and social media updates. Here's a tip to help you better organize your incoming Gmail messages.
One of the biggest time wasters we all face is sorting through our email inbox. This is a tedious task made worse because you have to sort through emails from the same sources every day, like newsletters and social media updates. Here's a tip to help you better organize your incoming Gmail messages.
 Did you know that your computer may have the capability to be turned on and off without ever physically pushing its power button? Besides helping you feel like a wizard, your computer's Wake-on-LAN feature has many convenient applications for your business, including saving time and energy, and aiding your campaign to create a greener workplace.
Did you know that your computer may have the capability to be turned on and off without ever physically pushing its power button? Besides helping you feel like a wizard, your computer's Wake-on-LAN feature has many convenient applications for your business, including saving time and energy, and aiding your campaign to create a greener workplace.
 Have you been frustrated with your employees lately? Maybe they aren't getting projects done on time, or aren't producing at a very high quality. Have you ever considered that you have substantial control over their job performance? People only work if they are motivated to do so. Here are six ways to motivate your employees.
Have you been frustrated with your employees lately? Maybe they aren't getting projects done on time, or aren't producing at a very high quality. Have you ever considered that you have substantial control over their job performance? People only work if they are motivated to do so. Here are six ways to motivate your employees.
 The latest news in office technology movements is the shift toward BYOD (Bring Your Own Device) environments; in which employees are bringing their own mobile devices to work. All the cool kids are doing it, but should you? Before you follow the trend and allow your employees to bring their devices to work, you should consider these risks.
The latest news in office technology movements is the shift toward BYOD (Bring Your Own Device) environments; in which employees are bringing their own mobile devices to work. All the cool kids are doing it, but should you? Before you follow the trend and allow your employees to bring their devices to work, you should consider these risks.
 You hear a lot about "migrating to the cloud." Using Internet technologies, cloud computing gives users scalable IT solutions that are hosted offsite in data centers, which look nothing like clouds. Cloud computing is a hot trend that many companies are taking advantage of, but is the cloud right for your organization?
You hear a lot about "migrating to the cloud." Using Internet technologies, cloud computing gives users scalable IT solutions that are hosted offsite in data centers, which look nothing like clouds. Cloud computing is a hot trend that many companies are taking advantage of, but is the cloud right for your organization?
 As commonplace as cellphones are today, it's hard to imagine that there was a time in the 1980's when this technology was first introduced and the benefits had to be explained. Here's an old cellphone commercial from Motorola about "the booming industry of cellular radio telephones." Times sure have changed!
As commonplace as cellphones are today, it's hard to imagine that there was a time in the 1980's when this technology was first introduced and the benefits had to be explained. Here's an old cellphone commercial from Motorola about "the booming industry of cellular radio telephones." Times sure have changed!
 Apple is at it again. After record breaking sales of the new iPhone 5s, Apple announced a new product line with confidence. CEO Tim Cooke and his staff recently launched new MacBook models, the Mac Pro workstation, a new OS, a new iPad mini model, and the most anticipated highlight; the new iPad Air.
Apple is at it again. After record breaking sales of the new iPhone 5s, Apple announced a new product line with confidence. CEO Tim Cooke and his staff recently launched new MacBook models, the Mac Pro workstation, a new OS, a new iPad mini model, and the most anticipated highlight; the new iPad Air.
 At a recent security event, VP of Gartner Neil MacDonald broke down the fundamentals of IT security into four categories, "Information security was never about device lockdown, or dictating applications, or building firewalls. It was always about protecting the confidentiality, the integrity, the authenticity, the availability of information." Here's a closer look at these four security qualities.
At a recent security event, VP of Gartner Neil MacDonald broke down the fundamentals of IT security into four categories, "Information security was never about device lockdown, or dictating applications, or building firewalls. It was always about protecting the confidentiality, the integrity, the authenticity, the availability of information." Here's a closer look at these four security qualities.
 The world you do business in is a pretty dangerous and messed up place, and things always seem to be getting worse. Thankfully, security technology is improving, which helps offset the risks of living in a perilous world. You can take advantage of these security improvements by installing intelligent surveillance cameras for your business.
The world you do business in is a pretty dangerous and messed up place, and things always seem to be getting worse. Thankfully, security technology is improving, which helps offset the risks of living in a perilous world. You can take advantage of these security improvements by installing intelligent surveillance cameras for your business.
 Your company's technology infrastructure is made up of several complex systems that all work together in order to keep your business running smoothly. Your IT infrastructure functions much in the same way as another type of infrastructure, your house. It's surprising how much you can learn about computer networking by looking at "This Old House."
Your company's technology infrastructure is made up of several complex systems that all work together in order to keep your business running smoothly. Your IT infrastructure functions much in the same way as another type of infrastructure, your house. It's surprising how much you can learn about computer networking by looking at "This Old House."
 We are in a unique time of Windows OS transitions. The redesigned Windows 8 has been out for one year, and the first major update to it (Windows 8.1) was just released. Additionally, the popular Windows XP expires in April, forcing everybody to upgrade and choose between Windows 7 and 8. Which OS will your business go with?
We are in a unique time of Windows OS transitions. The redesigned Windows 8 has been out for one year, and the first major update to it (Windows 8.1) was just released. Additionally, the popular Windows XP expires in April, forcing everybody to upgrade and choose between Windows 7 and 8. Which OS will your business go with?
 As your company grows and enters into more competitive markets, your ability to access reliable and accurate data is of the utmost importance. Ginni Rometty; CEO, president, and chair of IBM, shared her insight on data management in her speech on October 2nd at the IBM InterConnect 2013 event. Here are three benefits of successful data management according to Rometty.
As your company grows and enters into more competitive markets, your ability to access reliable and accurate data is of the utmost importance. Ginni Rometty; CEO, president, and chair of IBM, shared her insight on data management in her speech on October 2nd at the IBM InterConnect 2013 event. Here are three benefits of successful data management according to Rometty.
 What is the scariest situation you can imagine? Being chased by a werewolf? How about being boiled alive in a witches brew? Or what about succumbing to a zombie hoard? For people that are nomophobic, these monster-filled situations would be preferred compared to their greatest fear; being without their cell phone!
What is the scariest situation you can imagine? Being chased by a werewolf? How about being boiled alive in a witches brew? Or what about succumbing to a zombie hoard? For people that are nomophobic, these monster-filled situations would be preferred compared to their greatest fear; being without their cell phone!
 What are you terrified of? Spiders? Heights? Deep water? Financial problems? Shockingly, the greatest anxiety among humans is public speaking, even ranking above the fear of death! But, for some people, these things would be readily faced in lieu of their greatest fear; being cell phone-less! Oh, the horror!
What are you terrified of? Spiders? Heights? Deep water? Financial problems? Shockingly, the greatest anxiety among humans is public speaking, even ranking above the fear of death! But, for some people, these things would be readily faced in lieu of their greatest fear; being cell phone-less! Oh, the horror!
 Recently, Adobe sent out e-mails and letters to users notifying everyone of a security breach. "The attackers may have obtained access to your Adobe ID and encrypted password." The obvious question here is, "How do I protect myself and my business from such attacks?" The unfortunate answer is you can't, but you can marginalize the impact by taking some common sense measures.
Recently, Adobe sent out e-mails and letters to users notifying everyone of a security breach. "The attackers may have obtained access to your Adobe ID and encrypted password." The obvious question here is, "How do I protect myself and my business from such attacks?" The unfortunate answer is you can't, but you can marginalize the impact by taking some common sense measures.
 If your business has never experienced a major computer problem, then it's easy to underestimate just how damaging downtime can be. This conclusion can be drawn from a recent survey of small business owners, where 65% estimated they would only lose $500 if their company's network went down for a day. In reality, downtime is much more costly than $500.
If your business has never experienced a major computer problem, then it's easy to underestimate just how damaging downtime can be. This conclusion can be drawn from a recent survey of small business owners, where 65% estimated they would only lose $500 if their company's network went down for a day. In reality, downtime is much more costly than $500.
 One year ago, Microsoft took a big gamble when they released Windows 8 with a new user interface that strayed from their successful twenty year-old template. Throughout the year, Microsoft has been listening to user feedback and they have recently addressed the biggest issues with Windows 8.1, the first major upgrade to Microsoft's newest OS.
One year ago, Microsoft took a big gamble when they released Windows 8 with a new user interface that strayed from their successful twenty year-old template. Throughout the year, Microsoft has been listening to user feedback and they have recently addressed the biggest issues with Windows 8.1, the first major upgrade to Microsoft's newest OS.
 The way you treat customers, handle their feedback, and serve their needs can be the most powerful selling point of your business. Customer satisfaction comes down to the way customers feel after they've made a purchase. Your customer service policy can either make or break your business. Here's how to bulletproof your customer service policy.
The way you treat customers, handle their feedback, and serve their needs can be the most powerful selling point of your business. Customer satisfaction comes down to the way customers feel after they've made a purchase. Your customer service policy can either make or break your business. Here's how to bulletproof your customer service policy.
 As a small business, your goal should not only be to survive, but to thrive. Many times, small businesses try to cut costs by not purchasing essential equipment and services. Unfortunately, because of its cost, technology ends up on the backburner of the priority list. Don't cut corners. Here are seven tech assets you need to invest in.
As a small business, your goal should not only be to survive, but to thrive. Many times, small businesses try to cut costs by not purchasing essential equipment and services. Unfortunately, because of its cost, technology ends up on the backburner of the priority list. Don't cut corners. Here are seven tech assets you need to invest in.
 The modern IT landscape is dramatically changing from a model where an IT department controls everything, to companies outsourcing their IT services. This paradigm shift challenges older ideas about traditional network security equating ownership and control with strong security. Does your business view IT outsourcing as a security help or a hindrance?
The modern IT landscape is dramatically changing from a model where an IT department controls everything, to companies outsourcing their IT services. This paradigm shift challenges older ideas about traditional network security equating ownership and control with strong security. Does your business view IT outsourcing as a security help or a hindrance?
 With all the personal information users entrust to Facebook, it's no surprise that scammers are also on Facebook, often posing as friends. When using Facebook, you will need to be aware of this scam in order to keep your personal information safe. Here are four characteristics of a fake Facebook profile that you should consider before confirming a friendship.
With all the personal information users entrust to Facebook, it's no surprise that scammers are also on Facebook, often posing as friends. When using Facebook, you will need to be aware of this scam in order to keep your personal information safe. Here are four characteristics of a fake Facebook profile that you should consider before confirming a friendship.
 Perouse the YouTube comments on any popular video and it will appear like a teenybopper is texting a neo nazi. The level of stupidity seen in the comments of YouTube is the ultimate proof of human idiocy. Finally, after years of putting up with people's hate and ignorance, YouTube is cracking down on comments!
Perouse the YouTube comments on any popular video and it will appear like a teenybopper is texting a neo nazi. The level of stupidity seen in the comments of YouTube is the ultimate proof of human idiocy. Finally, after years of putting up with people's hate and ignorance, YouTube is cracking down on comments!
 Improving your computer's startup time is a great way to get more productivity out of your work day. Studies have shown that people are most productive during the early hours of the day; therefore, you don't want to waste your best hours waiting for a PC to load. Here are three easy tips you can do to improve your PC's boot up time.
Improving your computer's startup time is a great way to get more productivity out of your work day. Studies have shown that people are most productive during the early hours of the day; therefore, you don't want to waste your best hours waiting for a PC to load. Here are three easy tips you can do to improve your PC's boot up time.
 When experiencing a computer problem, what is the first thing you do to troubleshoot it? If you are an experienced PC user, then you will try turning your machine on and off again. Your computer's restart button can feel like a magic wand that takes care of any issue, but do you know how this fix-it wizardry works?
When experiencing a computer problem, what is the first thing you do to troubleshoot it? If you are an experienced PC user, then you will try turning your machine on and off again. Your computer's restart button can feel like a magic wand that takes care of any issue, but do you know how this fix-it wizardry works?
 You've seen them around everywhere. Every time you watch TV, look at a poster, listen to the news, or have a conversation with a teenager, you'll be exposed to the term "hashtag". What are hashtags exactly? What do they do? Why should you care about them? How can they help your business? #readmoretofindout
You've seen them around everywhere. Every time you watch TV, look at a poster, listen to the news, or have a conversation with a teenager, you'll be exposed to the term "hashtag". What are hashtags exactly? What do they do? Why should you care about them? How can they help your business? #readmoretofindout
 According to a new study from the International Data Corporation, tablets are expected to outsell PCs for the first time in the fourth quarter of 2014. While mobile device sales have been trending this way for years, this is the first time the mighty PC will be dethroned by a gadget. What does this mean for your business?
According to a new study from the International Data Corporation, tablets are expected to outsell PCs for the first time in the fourth quarter of 2014. While mobile device sales have been trending this way for years, this is the first time the mighty PC will be dethroned by a gadget. What does this mean for your business?
 Mobile devices give you the ability to always be connected with the virtual world. It may seem like this is great for productivity because you feel like more work is getting done; but could it be that constant connectivity is wearing us down? In light of the stresses caused from being connected, it's good to unplug and recharge your brain.
Mobile devices give you the ability to always be connected with the virtual world. It may seem like this is great for productivity because you feel like more work is getting done; but could it be that constant connectivity is wearing us down? In light of the stresses caused from being connected, it's good to unplug and recharge your brain.
 Every once ina while, a radical piece of technology is introduced to the market that has the potential to change everything. Over the last half century alone, digital music, cell phones, GPS technology, PCs, and much more hit the market and changed the way technology is incorporated into our daily lives and workplaces. Is Google Glass the next revolutionary gadget?
Every once ina while, a radical piece of technology is introduced to the market that has the potential to change everything. Over the last half century alone, digital music, cell phones, GPS technology, PCs, and much more hit the market and changed the way technology is incorporated into our daily lives and workplaces. Is Google Glass the next revolutionary gadget?
 In its infancy, social media was adopted by teenagers and used to share personal opinions. Many businesses took their sweet time adopting social media as part of their marketing strategy, supposing it to be a fad. Now that social media has grown up, almost every business has a social media presence, yet many companies still ban its use in the workplace.
In its infancy, social media was adopted by teenagers and used to share personal opinions. Many businesses took their sweet time adopting social media as part of their marketing strategy, supposing it to be a fad. Now that social media has grown up, almost every business has a social media presence, yet many companies still ban its use in the workplace.
 If you are still running your business or home PC on Windows XP, then it's vital that you upgrade to a newer OS. Yes, your decade-old Windows XP system may be working just fine, and therefore, you may not feel the urgency to upgrade, but you will feel the heat next year when Microsoft stops supporting its popular operating system.
If you are still running your business or home PC on Windows XP, then it's vital that you upgrade to a newer OS. Yes, your decade-old Windows XP system may be working just fine, and therefore, you may not feel the urgency to upgrade, but you will feel the heat next year when Microsoft stops supporting its popular operating system.
 Have you ever talked with an IT technician about how technology works, and one minute into their explanation you zone out and can't understand a word they're saying? They're speaking English, you recognize the words, yet you can't make sense of anything. In situations like this, you need an interpreter that speaks technologese, we can help.
Have you ever talked with an IT technician about how technology works, and one minute into their explanation you zone out and can't understand a word they're saying? They're speaking English, you recognize the words, yet you can't make sense of anything. In situations like this, you need an interpreter that speaks technologese, we can help.
 Remember when a family's home had only one phone line and someone else would pick up the phone in the middle of a call? There would be a click, a pause, the caller would then ask, "Is someone on the other line?" A hasty hang-up click would then follow. With VoIP, you can listen in on phone calls without being detected!
Remember when a family's home had only one phone line and someone else would pick up the phone in the middle of a call? There would be a click, a pause, the caller would then ask, "Is someone on the other line?" A hasty hang-up click would then follow. With VoIP, you can listen in on phone calls without being detected!
 First introduced by Xerox back in the 1964, the fax machine, or Long Distance Xerography as it was called then, was the hottest office productivity tool of its day. This new technology saved workers from having to send documents via mail, which dramatically improved office communications. Nearly fifty years later, and the fax machine has become a hindrance to office productivity.
First introduced by Xerox back in the 1964, the fax machine, or Long Distance Xerography as it was called then, was the hottest office productivity tool of its day. This new technology saved workers from having to send documents via mail, which dramatically improved office communications. Nearly fifty years later, and the fax machine has become a hindrance to office productivity.
 You can connect to over 2.7 billion people over the Internet, but you probably shouldn't. There are many people on the Internet with bad intentions, along with several websites that can harm your business. With a Unified Threat Management (UTM) tool, you can protect your business by filtering out the worst of the web.
You can connect to over 2.7 billion people over the Internet, but you probably shouldn't. There are many people on the Internet with bad intentions, along with several websites that can harm your business. With a Unified Threat Management (UTM) tool, you can protect your business by filtering out the worst of the web.
 What would happen if your business experienced a disaster and your sensitive information was erased? If you don't have a business continuity plan in place that includes data backup and recovery, then it's highly unlikely your company will survive. To protect your business, you will want to consider and choose one of these three backup solutions.
What would happen if your business experienced a disaster and your sensitive information was erased? If you don't have a business continuity plan in place that includes data backup and recovery, then it's highly unlikely your company will survive. To protect your business, you will want to consider and choose one of these three backup solutions.
 Have you ever wondered how cloud computing got its name? Despite popular opinion, cloud computing has nothing to do with the clouds in the sky. Instead, information is transferred to and from data centers, which are shaped nothing like clouds. Yet, there are similarities between the two clouds. We will compare them side-by-side to help you better understand cloud computing.
Have you ever wondered how cloud computing got its name? Despite popular opinion, cloud computing has nothing to do with the clouds in the sky. Instead, information is transferred to and from data centers, which are shaped nothing like clouds. Yet, there are similarities between the two clouds. We will compare them side-by-side to help you better understand cloud computing.
 Wouldn't you like to be more productive at work? For most of us, increased productivity means making more money, spending more time on what matters most (family, friends, etc.), and simply just feeling better. Many of us seek to increase productivity with elaborate and complicated methods. Here are five ways to increase your productivity, starting today.
Wouldn't you like to be more productive at work? For most of us, increased productivity means making more money, spending more time on what matters most (family, friends, etc.), and simply just feeling better. Many of us seek to increase productivity with elaborate and complicated methods. Here are five ways to increase your productivity, starting today.
 With traditional IT support, there's room for humorous-yet-frustrating mistakes stemming from miscommunication. Having a user with limited knowledge about computers describe their problem to an IT technician with limited patience is a recipe for disaster. Thankfully, new IT support tools make communication between users and IT support much easier.
With traditional IT support, there's room for humorous-yet-frustrating mistakes stemming from miscommunication. Having a user with limited knowledge about computers describe their problem to an IT technician with limited patience is a recipe for disaster. Thankfully, new IT support tools make communication between users and IT support much easier.
 With all the advancements in security technology, it's only a matter of time before clunky passwords are replaced with a more secure and more convenient solution. Unlocking your technology with a fingerprint reader is an easy and fun alternative that's being integrated with some of the latest devices; but how safe are fingerprint readers?
With all the advancements in security technology, it's only a matter of time before clunky passwords are replaced with a more secure and more convenient solution. Unlocking your technology with a fingerprint reader is an easy and fun alternative that's being integrated with some of the latest devices; but how safe are fingerprint readers?
 Do you let the batteries in your mobile devices fully deplete before recharging? If so, then you may be doing this based on some scientific-sounding advice you once heard. This advice has been around for years, and battery technology has dramatically advanced, which makes us ask the questions, "Is it still necessary to fully deplete your battery before recharging?"
Do you let the batteries in your mobile devices fully deplete before recharging? If so, then you may be doing this based on some scientific-sounding advice you once heard. This advice has been around for years, and battery technology has dramatically advanced, which makes us ask the questions, "Is it still necessary to fully deplete your battery before recharging?"
 In our last blog article, we introduced the IT trend of employees bringing in their personal devices to work (BYOD). We looked at 5 ways BYOD can help your business, but BYOD is not without risks. In part 2, we will cover five risks BYOD brings to your company's network and what you can to do manage them.
In our last blog article, we introduced the IT trend of employees bringing in their personal devices to work (BYOD). We looked at 5 ways BYOD can help your business, but BYOD is not without risks. In part 2, we will cover five risks BYOD brings to your company's network and what you can to do manage them.
 In a recent survey of small businesses, only 13% of respondents believed themselves to be susceptible to a disaster resulting in data loss. That means 87% of small businesses must be located in a fortress where they are protected from every natural disaster--yeah right! No business is immune from disaster; therefore, every company needs a disaster plan.
In a recent survey of small businesses, only 13% of respondents believed themselves to be susceptible to a disaster resulting in data loss. That means 87% of small businesses must be located in a fortress where they are protected from every natural disaster--yeah right! No business is immune from disaster; therefore, every company needs a disaster plan.
 The latest trend in business technology is employees bringing in their personal devices to work. This trend is commonly referred to as BYOD (Bring Your Own Device), and it's presenting businesses with both new opportunities and challenges. We will breakdown BYOD into 2 parts; benefits and risks. In part 1, we will look at five benefits of BYOD.
The latest trend in business technology is employees bringing in their personal devices to work. This trend is commonly referred to as BYOD (Bring Your Own Device), and it's presenting businesses with both new opportunities and challenges. We will breakdown BYOD into 2 parts; benefits and risks. In part 1, we will look at five benefits of BYOD.