The history of movies is rooted in technological advancement. After all, there are well over 100,000 still photographs in any feature length motion picture. The persistence of vision allows for these images to be strung together by our perception to form the images we see. It didn’t take long after the discovery of this phenomenon for it to be utilized as entertainment, and giving birth to cinema as we’ve come to know it.
The history of movies is rooted in technological advancement. After all, there are well over 100,000 still photographs in any feature length motion picture. The persistence of vision allows for these images to be strung together by our perception to form the images we see. It didn’t take long after the discovery of this phenomenon for it to be utilized as entertainment, and giving birth to cinema as we’ve come to know it.
Directive Blogs
 Businesses look to technology to solve their problems and make operations more efficient, and rightfully so, after all, technology is synonymous with “solution.” Although, just purchasing new technology isn’t enough to automatically see the desired results. New technology must be accompanied by intentional implementation efforts, which includes adapting it to your company’s culture. In other words, working with people.
Businesses look to technology to solve their problems and make operations more efficient, and rightfully so, after all, technology is synonymous with “solution.” Although, just purchasing new technology isn’t enough to automatically see the desired results. New technology must be accompanied by intentional implementation efforts, which includes adapting it to your company’s culture. In other words, working with people.
 In today's technology world, a lot of businesses are opting to take advantage of virtualized servers. These offer various benefits, including the ability to consolidate your servers into a neat, controlled package. But according to a recent study by Symantec, virtual servers might not be as secure as once thought. In fact, they might not be any more secure than a physical server.
In today's technology world, a lot of businesses are opting to take advantage of virtualized servers. These offer various benefits, including the ability to consolidate your servers into a neat, controlled package. But according to a recent study by Symantec, virtual servers might not be as secure as once thought. In fact, they might not be any more secure than a physical server.
 In 1859, our planet was hit with the largest recorded solar flare. This particular flare was known as the Carrington Event and it produced auroras that could be seen all around the world, even as far south as the Caribbean. The 1859 solar flare caused minimal damage and was seen mainly as an oddity. If such a flare struck today, however, the world would erupt into chaos.
In 1859, our planet was hit with the largest recorded solar flare. This particular flare was known as the Carrington Event and it produced auroras that could be seen all around the world, even as far south as the Caribbean. The 1859 solar flare caused minimal damage and was seen mainly as an oddity. If such a flare struck today, however, the world would erupt into chaos.
 As a small business owner, you enjoy the ability to operate quickly when action is needed. You appreciate the ease of communication within your office, and you can get things accomplished simply and efficiently. At least, that's the goal; maybe things aren't so smooth. One way to fix that is by integrating an intranet into your workplace.
As a small business owner, you enjoy the ability to operate quickly when action is needed. You appreciate the ease of communication within your office, and you can get things accomplished simply and efficiently. At least, that's the goal; maybe things aren't so smooth. One way to fix that is by integrating an intranet into your workplace.
 The concept behind BYOD seems really good--employees bring their personal devices to work and use them to accomplish company projects. Initially, BYOD was well received, but after reviewing the security risks, more companies are opting out of it. Is there another way to use mobile devices at work without all the hassle and risks of BYOD?
The concept behind BYOD seems really good--employees bring their personal devices to work and use them to accomplish company projects. Initially, BYOD was well received, but after reviewing the security risks, more companies are opting out of it. Is there another way to use mobile devices at work without all the hassle and risks of BYOD?
 The cloud is the next big thing for some businesses, but a lot of the time, there are too many options thrown at them all at once. They aren’t sure what the best path is for their business. A cloud solution can provide your company with a lot of benefits, but you want only the best for your business.
The cloud is the next big thing for some businesses, but a lot of the time, there are too many options thrown at them all at once. They aren’t sure what the best path is for their business. A cloud solution can provide your company with a lot of benefits, but you want only the best for your business.
 The Vestal, NY location of UPS has recently notified customers that they have been the victim of a data breach that has affected over 50 stores. According to a spokeswoman for UPS, any customer who had used a credit or debit card at the affected stores between April 29, 2014 and August 11, 2014 could be impacted.
The Vestal, NY location of UPS has recently notified customers that they have been the victim of a data breach that has affected over 50 stores. According to a spokeswoman for UPS, any customer who had used a credit or debit card at the affected stores between April 29, 2014 and August 11, 2014 could be impacted.
 Every business owner understands the importance of planning and the proper implementation of said plans. However, after everything is set up, it's easy to overlook the testing of one's plans, which can really come back to hurt you when all of your careful planning falls apart. Nowhere is this more true than with data recovery.
Every business owner understands the importance of planning and the proper implementation of said plans. However, after everything is set up, it's easy to overlook the testing of one's plans, which can really come back to hurt you when all of your careful planning falls apart. Nowhere is this more true than with data recovery.
 Keep It Simple Stupid, aka KISS, is a sure way to find success in business. By keeping operations simple, the cost of doing business is reduced, there's less room for error, and more people understand what's going on. Your IT infrastructure is at the heart of your organization, keeping IT simple will help your business kiss many of its problems goodbye!
Keep It Simple Stupid, aka KISS, is a sure way to find success in business. By keeping operations simple, the cost of doing business is reduced, there's less room for error, and more people understand what's going on. Your IT infrastructure is at the heart of your organization, keeping IT simple will help your business kiss many of its problems goodbye!
 The office is a unique place designed solely for the purpose of getting work done. Therefore, no matter how your workplace is designed, there's always room to improve it in order to squeeze out a few more precious minutes of productivity from each worker. As productivity goes, every minute saved adds up!
The office is a unique place designed solely for the purpose of getting work done. Therefore, no matter how your workplace is designed, there's always room to improve it in order to squeeze out a few more precious minutes of productivity from each worker. As productivity goes, every minute saved adds up!
 Crime might pay for those bold enough to do it, but that doesn't mean everyone should. Hackers likely don't take into account the fact that they are costing the world countless millions of dollars in damage only to further their own gain, and their influence can have far-reaching effects on people all over the world, let alone your business.
Crime might pay for those bold enough to do it, but that doesn't mean everyone should. Hackers likely don't take into account the fact that they are costing the world countless millions of dollars in damage only to further their own gain, and their influence can have far-reaching effects on people all over the world, let alone your business.
 Do you see those black clouds culminating on the horizon? They represent the possibility that hackers will gain access to your cloud storage. Though it is protected a number of ways, it will not stop an experienced hacker. To them, your defenses are as transparent as those thin, wispy, cirrus clouds that are so welcome on a boiling hot summer day.
Do you see those black clouds culminating on the horizon? They represent the possibility that hackers will gain access to your cloud storage. Though it is protected a number of ways, it will not stop an experienced hacker. To them, your defenses are as transparent as those thin, wispy, cirrus clouds that are so welcome on a boiling hot summer day.
 When it comes to hosting a party, it can be exhausting – it's a matter of space, cost, and responsibility, among other things. If you're too busy trying to organize everything, nobody will get to see the best side of you. Wouldn't it be so much easier to just hire someone to take care of the details? You would actually be able to enjoy your party!
When it comes to hosting a party, it can be exhausting – it's a matter of space, cost, and responsibility, among other things. If you're too busy trying to organize everything, nobody will get to see the best side of you. Wouldn't it be so much easier to just hire someone to take care of the details? You would actually be able to enjoy your party!
 When you experience an error or a performance issue with your company's computer system, you will troubleshoot the problem in hopes of resolving it quickly. Before you open the case of your hardware and start messing with components, check your cables. Even a small cabling issue can cause big problems with your entire network.
When you experience an error or a performance issue with your company's computer system, you will troubleshoot the problem in hopes of resolving it quickly. Before you open the case of your hardware and start messing with components, check your cables. Even a small cabling issue can cause big problems with your entire network.
 The first step toward properly running a business is realizing that you aren't the average consumer. You don't spend half an hour a day writing checks to pay for your bills - in fact, some of your employees probably do just that all day. The truth of the matter is that everything to a business owner is on a much larger scale than the average consumer - that includes purchasing your technology.
The first step toward properly running a business is realizing that you aren't the average consumer. You don't spend half an hour a day writing checks to pay for your bills - in fact, some of your employees probably do just that all day. The truth of the matter is that everything to a business owner is on a much larger scale than the average consumer - that includes purchasing your technology.
 Every business knows about "spending money in order to make money." Dropping cash on advertising and hiring key personnel are classic examples of this. However, "spending money on risk prevention in order to save money by avoiding expensive problems, and thereby making money," isn't as well known. Perhaps because it's harder to explain.
Every business knows about "spending money in order to make money." Dropping cash on advertising and hiring key personnel are classic examples of this. However, "spending money on risk prevention in order to save money by avoiding expensive problems, and thereby making money," isn't as well known. Perhaps because it's harder to explain.
 There's no denying that maintaining an IT infrastructure is a major expense. Not only is the equipment expensive to purchase, but it often comes with a larger-than-expected price tag to maintain. One of the best ways that you can cut back on the expenses of owning and operating an IT infrastructure is by taking advantage of desktop virtualization.
There's no denying that maintaining an IT infrastructure is a major expense. Not only is the equipment expensive to purchase, but it often comes with a larger-than-expected price tag to maintain. One of the best ways that you can cut back on the expenses of owning and operating an IT infrastructure is by taking advantage of desktop virtualization.
 Cloud computing is making everything easier for businesses. Companies utilizing IT infrastructures before cloud computing existed know exactly what we're talking about here. A quick analysis of organizations before and after the cloud perfectly exemplifies how cloud computing is making revolutionary changes to the way we do business.
Cloud computing is making everything easier for businesses. Companies utilizing IT infrastructures before cloud computing existed know exactly what we're talking about here. A quick analysis of organizations before and after the cloud perfectly exemplifies how cloud computing is making revolutionary changes to the way we do business.
 When your server experiences an issue, you have to act fast and take care of it before the issue turns into a problem. If a server problem is left unresolved, it can spread across your network and negatively affect operations. This is why it's best to take care of a server issue as soon as it's discovered.
When your server experiences an issue, you have to act fast and take care of it before the issue turns into a problem. If a server problem is left unresolved, it can spread across your network and negatively affect operations. This is why it's best to take care of a server issue as soon as it's discovered.
A common server problem is... what was it again? Oh, right. Memory failure!
 If your wireless router is an archaic piece of machinery from the turn of the century, you owe it to yourself to upgrade to something a little less dusty. Depending on your Internet connection, increasing your bandwidth is a tricky matter, and the easiest way to do so is by upgrading your wireless router. These next-gen routers are simple to use and don't require passwords; something that both increases network security and ease of use.
If your wireless router is an archaic piece of machinery from the turn of the century, you owe it to yourself to upgrade to something a little less dusty. Depending on your Internet connection, increasing your bandwidth is a tricky matter, and the easiest way to do so is by upgrading your wireless router. These next-gen routers are simple to use and don't require passwords; something that both increases network security and ease of use.
 For years, IT departments have been stereotyped as an antisocial bunch hiding in the shadows of server rooms, only coming out when a fellow employee experiences a problem with their workstation or a new gadget is released. Today, thanks to the prevalence of technology in every aspect of business, technicians are on the forefront of major business decisions and this stereotype is no more!
For years, IT departments have been stereotyped as an antisocial bunch hiding in the shadows of server rooms, only coming out when a fellow employee experiences a problem with their workstation or a new gadget is released. Today, thanks to the prevalence of technology in every aspect of business, technicians are on the forefront of major business decisions and this stereotype is no more!
 It's been said that a company's data is its most important resource. If this is true, then is it possible to assign a monetary value to your files? If you attempted to do so, you may come to the conclusion that your company's data is more valuable than anything else in your business, maybe even your own job!
It's been said that a company's data is its most important resource. If this is true, then is it possible to assign a monetary value to your files? If you attempted to do so, you may come to the conclusion that your company's data is more valuable than anything else in your business, maybe even your own job!
 Fifteen years ago, a simple oversight in technology development caused worldwide panic. The crisis was Y2K, and the fear was that, on New Year's Eve, computers would reset to 1900 instead of 2000, causing all technology to fail. Thankfully, New Years Eve came and went without incident and people got worked up over nothing. You've heard story, but you may not have heard about all the work IT companies did to save the day!
Fifteen years ago, a simple oversight in technology development caused worldwide panic. The crisis was Y2K, and the fear was that, on New Year's Eve, computers would reset to 1900 instead of 2000, causing all technology to fail. Thankfully, New Years Eve came and went without incident and people got worked up over nothing. You've heard story, but you may not have heard about all the work IT companies did to save the day!
 Can you tell the difference between the two words, Internet and Intranet? The difference is much more than simply two letters. Both are valuable marketing tools, particularly for small businesses, but what exactly differentiates them from each other? The key to understanding this is a simple English lesson.
Can you tell the difference between the two words, Internet and Intranet? The difference is much more than simply two letters. Both are valuable marketing tools, particularly for small businesses, but what exactly differentiates them from each other? The key to understanding this is a simple English lesson.
 Your PC's CPU (Central Processing Unit) is one of the many delecate components inside your computer. The CPU essentially does all of the thinking that your PC needs to do, processing instructions from your operating system and all of your programs. That might not seem like a big deal, but most CPUs today handle billions of processes every second. It doesn't store data (that's the hard drive) but if the CPU fails to work properly, you won't be getting much work done.
Your PC's CPU (Central Processing Unit) is one of the many delecate components inside your computer. The CPU essentially does all of the thinking that your PC needs to do, processing instructions from your operating system and all of your programs. That might not seem like a big deal, but most CPUs today handle billions of processes every second. It doesn't store data (that's the hard drive) but if the CPU fails to work properly, you won't be getting much work done.
 The trend of employees bringing in their own mobile devices to the office and using them for work purposes (BYOD) is growing rapidly. In fact, a new report from Juniper Research forecasts that by 2018, more than one billion employee-owned devices will be used in enterprises. A trend this big means that organizations have to take BYOD seriously.
The trend of employees bringing in their own mobile devices to the office and using them for work purposes (BYOD) is growing rapidly. In fact, a new report from Juniper Research forecasts that by 2018, more than one billion employee-owned devices will be used in enterprises. A trend this big means that organizations have to take BYOD seriously.
 Trivia time! Do you know what device was invented in 1892 that changed the face of offices around the world? If you guessed the fax machine then you're close, but you need to think further ahead by almost 50 years (the first fax machine was patented in 1843 by Alexander Bain). More influential than even the fax machine is the file cabinet, established in 1892.
Trivia time! Do you know what device was invented in 1892 that changed the face of offices around the world? If you guessed the fax machine then you're close, but you need to think further ahead by almost 50 years (the first fax machine was patented in 1843 by Alexander Bain). More influential than even the fax machine is the file cabinet, established in 1892.
 Hackers have many different tools at their disposal to access your computer. Some of these tools can even control your machine! When a hacker controls your PC, your computer is now part of a network made up of other compromised devices that they control. This compromised network is known as a botnet, and you don't want to be part of it!
Hackers have many different tools at their disposal to access your computer. Some of these tools can even control your machine! When a hacker controls your PC, your computer is now part of a network made up of other compromised devices that they control. This compromised network is known as a botnet, and you don't want to be part of it!
 It takes a special kind of person to give great customer service. If someone can't pick up on social cues, or if they have a low tolerance for repetitive questions, they will end up offending a lot of customers. To assist our clients with their IT problems, we make sure to hire the most helpful customer service representatives that we can find.
It takes a special kind of person to give great customer service. If someone can't pick up on social cues, or if they have a low tolerance for repetitive questions, they will end up offending a lot of customers. To assist our clients with their IT problems, we make sure to hire the most helpful customer service representatives that we can find.
 If you're still running your business or home PC on Windows XP, then it's vital that you upgrade to a newer OS. Yes, your decade-old Windows XP system may be working just fine, and therefore, you may not feel the urgency to upgrade, but you will feel the heat when Microsoft stops supporting its popular OS--in just a few short days!
If you're still running your business or home PC on Windows XP, then it's vital that you upgrade to a newer OS. Yes, your decade-old Windows XP system may be working just fine, and therefore, you may not feel the urgency to upgrade, but you will feel the heat when Microsoft stops supporting its popular OS--in just a few short days!
 It seems odd, but people are declaring 3D printers to be the technology that's going to revolutionize the future while simultaneously moving away from paper printers. Let talk about the printers you use for your business. A print server solution will help you transition away from your current printer setup so that you can take advantage of cool futuristic technologies!
It seems odd, but people are declaring 3D printers to be the technology that's going to revolutionize the future while simultaneously moving away from paper printers. Let talk about the printers you use for your business. A print server solution will help you transition away from your current printer setup so that you can take advantage of cool futuristic technologies!
 Technology is a major part of everything your business does. Therefore, you need a technology partner that does more than just fixes your computers. For example, if your smartphone decided that, "today is a good day to die," then it wouldn't matter how great your workstation was running, your day would still be ruined.
Technology is a major part of everything your business does. Therefore, you need a technology partner that does more than just fixes your computers. For example, if your smartphone decided that, "today is a good day to die," then it wouldn't matter how great your workstation was running, your day would still be ruined.
 Because you manage a business, we don't have to convince you of the benefits of planning ahead. For example, having an onboarding strategy in place for hiring a new employee will get them acclimated more quickly, which will help them contribute to boosting your bottom line faster. Similarly, planning your IT network maintenances will benefit your organization.
Because you manage a business, we don't have to convince you of the benefits of planning ahead. For example, having an onboarding strategy in place for hiring a new employee will get them acclimated more quickly, which will help them contribute to boosting your bottom line faster. Similarly, planning your IT network maintenances will benefit your organization.
 By now, you have hopefully heard about Windows XP being no longer supported by Microsoft come April, but what you may have missed is that there's another popular Windows OS, Windows Server 2003, that's also set to expire relatively soon. July 14, 2015 is the end of support date for Windows Server 2003. Have you made plans to upgrade?
By now, you have hopefully heard about Windows XP being no longer supported by Microsoft come April, but what you may have missed is that there's another popular Windows OS, Windows Server 2003, that's also set to expire relatively soon. July 14, 2015 is the end of support date for Windows Server 2003. Have you made plans to upgrade?
 Due to the irreplaceable nature of data, server units may be your company's most important assets. Therefore, when it comes time to purchase a new server, you will want to make sure that your new unit will be exactly what your business needs. Getting a model that's too small or too powerful can be costly. Here's what to look for when purchasing a new server.
Due to the irreplaceable nature of data, server units may be your company's most important assets. Therefore, when it comes time to purchase a new server, you will want to make sure that your new unit will be exactly what your business needs. Getting a model that's too small or too powerful can be costly. Here's what to look for when purchasing a new server.
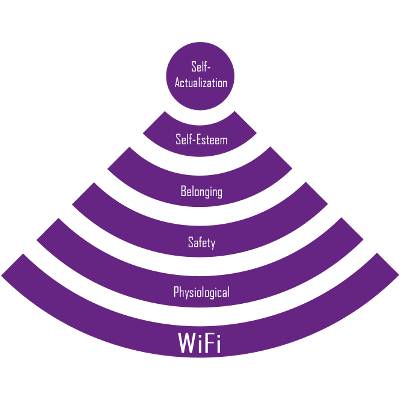 In 1943, psychologist Abraham Maslow published a paper about human motivation that would become the well-known Maslow's Hierarchy of Needs. His theory states that before self-actualization can be achieved, four needs must first be met, like esteem, belonging, safety, and physiological (the most basic which includes, air, food, water, etc.). In 2014, we feel the need to add one more layer to Maslow's pyramid: WiFi.
In 1943, psychologist Abraham Maslow published a paper about human motivation that would become the well-known Maslow's Hierarchy of Needs. His theory states that before self-actualization can be achieved, four needs must first be met, like esteem, belonging, safety, and physiological (the most basic which includes, air, food, water, etc.). In 2014, we feel the need to add one more layer to Maslow's pyramid: WiFi.
 Simplifying a complicated procedure is a sure way to get ahead. An enterprise's communication system can be extremely complicated with everything a business needs out of it. Voice over Internet Protocol, aka VoIP, is a solution that can simplify your entire communications system. Simplifying something major like communication will benefit your business in many ways.
Simplifying a complicated procedure is a sure way to get ahead. An enterprise's communication system can be extremely complicated with everything a business needs out of it. Voice over Internet Protocol, aka VoIP, is a solution that can simplify your entire communications system. Simplifying something major like communication will benefit your business in many ways.
 It's good to backup your data, but can you have too much of a good thing? While this may be the case for several enjoyable activities like partying and buffets, this isn't the case with data backup. In fact, the more layers of data backup you have, the more secure you will be. How good is your data backup solution?
It's good to backup your data, but can you have too much of a good thing? While this may be the case for several enjoyable activities like partying and buffets, this isn't the case with data backup. In fact, the more layers of data backup you have, the more secure you will be. How good is your data backup solution?
 One of the purposes of technology is to help your business grow. The best way to achieve this goal is to be intentional with your technology. Sometimes running a business can be so hectic that keeping up with your technology becomes an afterthought. Neglecting your technology can eat into your organization's profits; therefore, it makes more sense to outsource your IT.
One of the purposes of technology is to help your business grow. The best way to achieve this goal is to be intentional with your technology. Sometimes running a business can be so hectic that keeping up with your technology becomes an afterthought. Neglecting your technology can eat into your organization's profits; therefore, it makes more sense to outsource your IT.
 Remember back when buying mobile devices for your business meant choosing between a handful of laptops? Thanks to the increased proliferation of devices like smartphones, tablets, netbooks, and the development new hybrid models, it's become quite the task to pick out the right make and model. Here are five questions to consider when picking out mobile devices for your organization.
Remember back when buying mobile devices for your business meant choosing between a handful of laptops? Thanks to the increased proliferation of devices like smartphones, tablets, netbooks, and the development new hybrid models, it's become quite the task to pick out the right make and model. Here are five questions to consider when picking out mobile devices for your organization.
 One of the most common ways computer viruses spread is through email. Most of the malware-carrying messages are caught in your account's spam filter, so you don't have to worry about those. It's the malicious emails that make it to your inbox that you need to be mindful of, and phishing emails are by far the most dangerous.
One of the most common ways computer viruses spread is through email. Most of the malware-carrying messages are caught in your account's spam filter, so you don't have to worry about those. It's the malicious emails that make it to your inbox that you need to be mindful of, and phishing emails are by far the most dangerous.
 It's nice to get a shiny new computer that's fast, powerful, and has all the latest features. Before you install your new machine, you have to make a decision about what to do with your old one. Your old computer has been a faithful friend over the years so you may feel bad pitching it to the curb; instead, consider giving it a new home.
It's nice to get a shiny new computer that's fast, powerful, and has all the latest features. Before you install your new machine, you have to make a decision about what to do with your old one. Your old computer has been a faithful friend over the years so you may feel bad pitching it to the curb; instead, consider giving it a new home.
 Working in the IT industry means embracing change and the latest technology trends. Doing the same thing day-in and day-out is a luxury we don't have, and frankly, sounds kind of boring. Since computers were first invented, there's been a need to service them. Here's a look at how the IT service industry has changed over the past 50 years.
Working in the IT industry means embracing change and the latest technology trends. Doing the same thing day-in and day-out is a luxury we don't have, and frankly, sounds kind of boring. Since computers were first invented, there's been a need to service them. Here's a look at how the IT service industry has changed over the past 50 years.
 If you've never taken advantage of remote support to remedy an IT problem, then you're likely doing IT support the hard way by having a technician physically take care of every issue. While it's always nice to chat with your friendly tech, you may be able to save yourself a whole lot of time and money by taking care of the issue with remote support.
If you've never taken advantage of remote support to remedy an IT problem, then you're likely doing IT support the hard way by having a technician physically take care of every issue. While it's always nice to chat with your friendly tech, you may be able to save yourself a whole lot of time and money by taking care of the issue with remote support.
 You may feel like your computer network is immune to data loss, but according to a study by Blackblaze.com, 46% of users experience data loss every year. Whether it's from something big like a natural disaster, or minor like improperly removing a flash drive, every form of data loss is costly and can be prevented with a data backup plan.
You may feel like your computer network is immune to data loss, but according to a study by Blackblaze.com, 46% of users experience data loss every year. Whether it's from something big like a natural disaster, or minor like improperly removing a flash drive, every form of data loss is costly and can be prevented with a data backup plan.
 At a recent security event, VP of Gartner Neil MacDonald broke down the fundamentals of IT security into four categories, "Information security was never about device lockdown, or dictating applications, or building firewalls. It was always about protecting the confidentiality, the integrity, the authenticity, the availability of information." Here's a closer look at these four security qualities.
At a recent security event, VP of Gartner Neil MacDonald broke down the fundamentals of IT security into four categories, "Information security was never about device lockdown, or dictating applications, or building firewalls. It was always about protecting the confidentiality, the integrity, the authenticity, the availability of information." Here's a closer look at these four security qualities.
 The world you do business in is a pretty dangerous and messed up place, and things always seem to be getting worse. Thankfully, security technology is improving, which helps offset the risks of living in a perilous world. You can take advantage of these security improvements by installing intelligent surveillance cameras for your business.
The world you do business in is a pretty dangerous and messed up place, and things always seem to be getting worse. Thankfully, security technology is improving, which helps offset the risks of living in a perilous world. You can take advantage of these security improvements by installing intelligent surveillance cameras for your business.
 Your company's technology infrastructure is made up of several complex systems that all work together in order to keep your business running smoothly. Your IT infrastructure functions much in the same way as another type of infrastructure, your house. It's surprising how much you can learn about computer networking by looking at "This Old House."
Your company's technology infrastructure is made up of several complex systems that all work together in order to keep your business running smoothly. Your IT infrastructure functions much in the same way as another type of infrastructure, your house. It's surprising how much you can learn about computer networking by looking at "This Old House."
 We are in a unique time of Windows OS transitions. The redesigned Windows 8 has been out for one year, and the first major update to it (Windows 8.1) was just released. Additionally, the popular Windows XP expires in April, forcing everybody to upgrade and choose between Windows 7 and 8. Which OS will your business go with?
We are in a unique time of Windows OS transitions. The redesigned Windows 8 has been out for one year, and the first major update to it (Windows 8.1) was just released. Additionally, the popular Windows XP expires in April, forcing everybody to upgrade and choose between Windows 7 and 8. Which OS will your business go with?
 Remember when a family's home had only one phone line and someone else would pick up the phone in the middle of a call? There would be a click, a pause, the caller would then ask, "Is someone on the other line?" A hasty hang-up click would then follow. With VoIP, you can listen in on phone calls without being detected!
Remember when a family's home had only one phone line and someone else would pick up the phone in the middle of a call? There would be a click, a pause, the caller would then ask, "Is someone on the other line?" A hasty hang-up click would then follow. With VoIP, you can listen in on phone calls without being detected!
 First introduced by Xerox back in the 1964, the fax machine, or Long Distance Xerography as it was called then, was the hottest office productivity tool of its day. This new technology saved workers from having to send documents via mail, which dramatically improved office communications. Nearly fifty years later, and the fax machine has become a hindrance to office productivity.
First introduced by Xerox back in the 1964, the fax machine, or Long Distance Xerography as it was called then, was the hottest office productivity tool of its day. This new technology saved workers from having to send documents via mail, which dramatically improved office communications. Nearly fifty years later, and the fax machine has become a hindrance to office productivity.
 You can connect to over 2.7 billion people over the Internet, but you probably shouldn't. There are many people on the Internet with bad intentions, along with several websites that can harm your business. With a Unified Threat Management (UTM) tool, you can protect your business by filtering out the worst of the web.
You can connect to over 2.7 billion people over the Internet, but you probably shouldn't. There are many people on the Internet with bad intentions, along with several websites that can harm your business. With a Unified Threat Management (UTM) tool, you can protect your business by filtering out the worst of the web.
 What would happen if your business experienced a disaster and your sensitive information was erased? If you don't have a business continuity plan in place that includes data backup and recovery, then it's highly unlikely your company will survive. To protect your business, you will want to consider and choose one of these three backup solutions.
What would happen if your business experienced a disaster and your sensitive information was erased? If you don't have a business continuity plan in place that includes data backup and recovery, then it's highly unlikely your company will survive. To protect your business, you will want to consider and choose one of these three backup solutions.
 The growing popularity of employees bringing in their own devices into the workplace (BYOD) is challenging the traditional model of IT for businesses. Many companies are embracing BYOD and adapting their IT networks accordingly. With the way things are trending, it's important to ask yourself where all of this is heading, and consider what a fully realized BYOD environment will look like.
The growing popularity of employees bringing in their own devices into the workplace (BYOD) is challenging the traditional model of IT for businesses. Many companies are embracing BYOD and adapting their IT networks accordingly. With the way things are trending, it's important to ask yourself where all of this is heading, and consider what a fully realized BYOD environment will look like.
 We are doing business in a digital world. Technology has become so prevalent that the employee who pulls out a notebook at a meeting is now the odd man out. Yet, you will still find dated paper-consuming devices in modern offices like fax machines. Is it possible for an office to go completely paperless?
We are doing business in a digital world. Technology has become so prevalent that the employee who pulls out a notebook at a meeting is now the odd man out. Yet, you will still find dated paper-consuming devices in modern offices like fax machines. Is it possible for an office to go completely paperless?
 It's convenient to have an in-house IT technician. If your computer freezes up, you can call the IT department and they will swoop in and save the day. This is how in-house IT is supposed to work, but it's hard to hire anyone that's 100% reliable. We think it's actually more advantageous to outsource your IT; here are 5 reasons why.
It's convenient to have an in-house IT technician. If your computer freezes up, you can call the IT department and they will swoop in and save the day. This is how in-house IT is supposed to work, but it's hard to hire anyone that's 100% reliable. We think it's actually more advantageous to outsource your IT; here are 5 reasons why.
 There is a common misperception that strong anti-virus software is all you need to cover the security of your network. While anti-virus software is an important component to network security, there's more to it if you want a secure network. You need to also take into account the human factor, which can disable even the strongest software solution.
There is a common misperception that strong anti-virus software is all you need to cover the security of your network. While anti-virus software is an important component to network security, there's more to it if you want a secure network. You need to also take into account the human factor, which can disable even the strongest software solution.
 You can take out an insurance policy on anything, even a wedding. Insurance company Fireman will protect your big day against "nonrefundable expenses, including cancellation due to serious illness, injury, extreme weather, a missing caterer or officiate -- even a bankrupt event facility." Your businesses technology is important enough to insure; is there a policy to protect your tech?
You can take out an insurance policy on anything, even a wedding. Insurance company Fireman will protect your big day against "nonrefundable expenses, including cancellation due to serious illness, injury, extreme weather, a missing caterer or officiate -- even a bankrupt event facility." Your businesses technology is important enough to insure; is there a policy to protect your tech?
 As a business owner, you are always on the lookout for money saving solutions. Technology offers cost-effective options because it can be used to save money by implementing something new, instead of making cuts. A print server solution is one example of how upgrading your technology can save you money.
As a business owner, you are always on the lookout for money saving solutions. Technology offers cost-effective options because it can be used to save money by implementing something new, instead of making cuts. A print server solution is one example of how upgrading your technology can save you money.
 Upgrading your network and shopping for new technology can be a daunting task. Technology is expensive and it's an investment that will help your business grow, but that's only if you purchase what you need. A poor technology purchase can actually be a budget buster. To maximize your new technology purchases, it's worth it to partner with IT professionals.
Upgrading your network and shopping for new technology can be a daunting task. Technology is expensive and it's an investment that will help your business grow, but that's only if you purchase what you need. A poor technology purchase can actually be a budget buster. To maximize your new technology purchases, it's worth it to partner with IT professionals.
 You wouldn't make a major technology purchase without first researching it. A person who gives you advice is essentially putting their reputation on the line. When it comes to technology and our IT services, we will confidently offer you our expert advice in order to help provide you with the best solution possible. In business, this is called a guarantee!
You wouldn't make a major technology purchase without first researching it. A person who gives you advice is essentially putting their reputation on the line. When it comes to technology and our IT services, we will confidently offer you our expert advice in order to help provide you with the best solution possible. In business, this is called a guarantee!
 If it's been a few years since you setup your wireless network, then you may be overdue for an upgrade. Thanks to more devices having mobile capabilities, and more employees bringing their devices to work, wireless network technology has advanced quickly. Your old router might not be up for the new demands of the mobile office.
If it's been a few years since you setup your wireless network, then you may be overdue for an upgrade. Thanks to more devices having mobile capabilities, and more employees bringing their devices to work, wireless network technology has advanced quickly. Your old router might not be up for the new demands of the mobile office.
 There's a tidal wave of different consumer devices available on the market; smartphones, tablets, laptops, netbooks, and much more. Employees love their devices and love bringing them to work. If your company is allowing for Bring Your Own Device (BYOD), then you will want professional support to get the most out of it.
There's a tidal wave of different consumer devices available on the market; smartphones, tablets, laptops, netbooks, and much more. Employees love their devices and love bringing them to work. If your company is allowing for Bring Your Own Device (BYOD), then you will want professional support to get the most out of it.
 As a business, you have to market yourself. Fitting everything you do into a catch phrase doesn't do justice to your many services. We know the feeling. As an IT Company, we do much more than computer repair. In fact, we work hard to find solutions for every part of business, including areas you wouldn't suspect, like administration and more!
As a business, you have to market yourself. Fitting everything you do into a catch phrase doesn't do justice to your many services. We know the feeling. As an IT Company, we do much more than computer repair. In fact, we work hard to find solutions for every part of business, including areas you wouldn't suspect, like administration and more!
 The whole point of making a budget is to control costs. All it takes is one surprise to undo all the careful work of budget planning. No department is immune to unplanned expenses, and while it's impossible to totally prevent budget-busting expenses across the board, you can take action to turn many surprise expenses into controllable costs.
The whole point of making a budget is to control costs. All it takes is one surprise to undo all the careful work of budget planning. No department is immune to unplanned expenses, and while it's impossible to totally prevent budget-busting expenses across the board, you can take action to turn many surprise expenses into controllable costs.
 Many businesses are migrating their computing needs over to the cloud. In a worldwide survey, Gartner found that 60% of businesses have increased their budgets for cloud services through 2014. Yet, cloud computing may not be right for every business. For companies that would like cloud services, but may have cloud anxiety, going with a private cloud is a valid option.
Many businesses are migrating their computing needs over to the cloud. In a worldwide survey, Gartner found that 60% of businesses have increased their budgets for cloud services through 2014. Yet, cloud computing may not be right for every business. For companies that would like cloud services, but may have cloud anxiety, going with a private cloud is a valid option.
 When it comes to computer memory, redundancy is a good thing. The more places that you have your data backed up to, the better off you will be if something happens to your hard drive. RAID is a common hard drive formatting procedure that improves server performance and protects your data in the event of a crash.
When it comes to computer memory, redundancy is a good thing. The more places that you have your data backed up to, the better off you will be if something happens to your hard drive. RAID is a common hard drive formatting procedure that improves server performance and protects your data in the event of a crash.
 Every business needs to backup their data. If your company is hit with a disaster, and there is no backup in place, then it will be a critical hit to your operation. Backing up data with tape is a widely used solution, and while this is better than nothing, it is very inefficient compared to using BDR.
Every business needs to backup their data. If your company is hit with a disaster, and there is no backup in place, then it will be a critical hit to your operation. Backing up data with tape is a widely used solution, and while this is better than nothing, it is very inefficient compared to using BDR.
 We’re all familiar with the “Dummies” book series, they are helpful when it comes to understanding specific topics, but not all of us have the time to read a manual of information. We want to dummify web knowledge regarding the web’s ever changing buzzwords and platforms. This will help educate you on what web services and products are available for your company’s website. Every business owner should at least be aware of the website platform they are using and be fluent enough to understand its capabilities. If your website breaks, then having at least a basic understanding will make interacting with your website maintenance team go smoother, and give you a foot in the door if you ever want to take the plunge and learn more.
We’re all familiar with the “Dummies” book series, they are helpful when it comes to understanding specific topics, but not all of us have the time to read a manual of information. We want to dummify web knowledge regarding the web’s ever changing buzzwords and platforms. This will help educate you on what web services and products are available for your company’s website. Every business owner should at least be aware of the website platform they are using and be fluent enough to understand its capabilities. If your website breaks, then having at least a basic understanding will make interacting with your website maintenance team go smoother, and give you a foot in the door if you ever want to take the plunge and learn more.
 Do you feel tied down by your phone system? Traditional phone plans can be expensive and your phone bill will grow if you try to do more, like add lines and use extra features. One of the ways that the Internet can help your business save money and grow is by replacing expensive phone plans with Voice over Internet Protocol (VoIP).
Do you feel tied down by your phone system? Traditional phone plans can be expensive and your phone bill will grow if you try to do more, like add lines and use extra features. One of the ways that the Internet can help your business save money and grow is by replacing expensive phone plans with Voice over Internet Protocol (VoIP).
 Isn't it nice to have everything prepared for you? Of course it is. Whether it's having your dinner made for you when you get home, or having your car turned over to you fueled up and cleaned out, everybody appreciates having everything taken care of. In the world of technology, we take care of everything with our turnkey business management solutions.
Isn't it nice to have everything prepared for you? Of course it is. Whether it's having your dinner made for you when you get home, or having your car turned over to you fueled up and cleaned out, everybody appreciates having everything taken care of. In the world of technology, we take care of everything with our turnkey business management solutions.
 Servers have always been one of the more expensive yet crucial pieces of your IT infrastructure. A new development in servers is the microserver, which is a stripped down version of a server. The appeal is that they can be designed to handle one task efficiently, and therefore, use fewer resources while costing less to purchase and maintain.
Servers have always been one of the more expensive yet crucial pieces of your IT infrastructure. A new development in servers is the microserver, which is a stripped down version of a server. The appeal is that they can be designed to handle one task efficiently, and therefore, use fewer resources while costing less to purchase and maintain.
 We often talk about the need to back up your data, but did you know that it is also a best practice to back up your hardware? Backing up your hardware works differently than data backup; whereas data backup involves network devices and a cloud, backing up your hardware is a simple matter of having extra computer components on your premise.
We often talk about the need to back up your data, but did you know that it is also a best practice to back up your hardware? Backing up your hardware works differently than data backup; whereas data backup involves network devices and a cloud, backing up your hardware is a simple matter of having extra computer components on your premise.
 Michele Secor was born in the Oneonta area and lived in Vermont for many years before coming back to the area and joining our Accounting Department in October of 2012. She lives in Otego, NY with her husband Scott, 2 sons Ryan & Alex and their pet rabbit Mr. Fluff Fluff. Her hobbies include reading, home renovation and gardening. Michele enjoys spending time with her family, especially going camping in the summer and visiting the ocean as often as possible. As the Controller, Michele is an indispensable part of the Directive team.
Michele Secor was born in the Oneonta area and lived in Vermont for many years before coming back to the area and joining our Accounting Department in October of 2012. She lives in Otego, NY with her husband Scott, 2 sons Ryan & Alex and their pet rabbit Mr. Fluff Fluff. Her hobbies include reading, home renovation and gardening. Michele enjoys spending time with her family, especially going camping in the summer and visiting the ocean as often as possible. As the Controller, Michele is an indispensable part of the Directive team.
 Have you ever felt like your business is missing out on a big opportunity simply because you are unaware of it? In order to see a hidden opportunity, you need a fresh set of eyes. You need the help of an expert who knows what to look for, and you need regular input. This is exactly why we offer business technology reviews.
Have you ever felt like your business is missing out on a big opportunity simply because you are unaware of it? In order to see a hidden opportunity, you need a fresh set of eyes. You need the help of an expert who knows what to look for, and you need regular input. This is exactly why we offer business technology reviews.
 As busy as you are, the last thing that you want is to have one more thing to keep track of. This is why you have us take care of your IT infrastructure; it is worth it compared to learning how to troubleshoot each problem by yourself. Did you know that we can take care of more than just your computer network? With our vendor management service, we can also keep track of all of your technology.
As busy as you are, the last thing that you want is to have one more thing to keep track of. This is why you have us take care of your IT infrastructure; it is worth it compared to learning how to troubleshoot each problem by yourself. Did you know that we can take care of more than just your computer network? With our vendor management service, we can also keep track of all of your technology.
 The consumer adaptation of mobile devices continues to skyrocket. In America, there is a 46% ownership rate of smartphones among adults, this according to Pew Research. Tablets are also a booming market, projected to sell 1.2 billion units in 2013. If your business is not taking advantage of this trend, then you may be missing out on a golden opportunity.
The consumer adaptation of mobile devices continues to skyrocket. In America, there is a 46% ownership rate of smartphones among adults, this according to Pew Research. Tablets are also a booming market, projected to sell 1.2 billion units in 2013. If your business is not taking advantage of this trend, then you may be missing out on a golden opportunity.
 Using strong passwords is a critical part of keeping your network protected. For years we have been preaching the need to use complex passwords, along with the need to use different passwords for different accounts. As the technology of crackers (not the salted kind) improves, the need to be diligent about password security intensifies.
Using strong passwords is a critical part of keeping your network protected. For years we have been preaching the need to use complex passwords, along with the need to use different passwords for different accounts. As the technology of crackers (not the salted kind) improves, the need to be diligent about password security intensifies.
 When you’re trying to create an impressive layout and design for your website, that will grab the attention of visitors, color can be one of the most powerful weapons in your design arsenal. Carefully chosen colors that create a balanced contrast allow the designer to control what the user’s attention is drawn to. Without any contrast in color, it becomes difficult to emphasize the importance of different elements of your website.
When you’re trying to create an impressive layout and design for your website, that will grab the attention of visitors, color can be one of the most powerful weapons in your design arsenal. Carefully chosen colors that create a balanced contrast allow the designer to control what the user’s attention is drawn to. Without any contrast in color, it becomes difficult to emphasize the importance of different elements of your website.
 Your company's information on your network is labeled as "sensitive" for a reason. The files on your servers contain the secrets to your success, along with financial records about you, your employees, and your customers. When trusting sensitive data to a third party, make sure that it is someone you trust.
Your company's information on your network is labeled as "sensitive" for a reason. The files on your servers contain the secrets to your success, along with financial records about you, your employees, and your customers. When trusting sensitive data to a third party, make sure that it is someone you trust.
 Thanks to the cloud computing, there's a lot of chatter these days about doing your work remotely. The idea of accessing your data from anywhere on any device is an exciting prospect, but it is not a new one. Windows Terminal Services (renamed Remote Desktop Services in Windows Server 2008 R2) has had this ability for many years, and it is still a great remote service option for your network.
Thanks to the cloud computing, there's a lot of chatter these days about doing your work remotely. The idea of accessing your data from anywhere on any device is an exciting prospect, but it is not a new one. Windows Terminal Services (renamed Remote Desktop Services in Windows Server 2008 R2) has had this ability for many years, and it is still a great remote service option for your network.
 If your business is large enough to have its own IT department, then you know firsthand how valuable it is to have a knowledgeable technology professional on the premise. Being IT technicians ourselves, we experience this appreciation all the time from helping our clients. Sometimes, a technician's popularity can be almost overwhelming, and for times like these, it is nice to have backup.
If your business is large enough to have its own IT department, then you know firsthand how valuable it is to have a knowledgeable technology professional on the premise. Being IT technicians ourselves, we experience this appreciation all the time from helping our clients. Sometimes, a technician's popularity can be almost overwhelming, and for times like these, it is nice to have backup.
 One shocking IT scenario that we regularly encounter is expensive computer hardware plugged into inexpensive power strips. Power strips are adequate if you need a few extra outlets for your kitchen appliances, but if you want to protect the computer hardware that is mission critical to your business, like servers and NAS devices, then you will need a solution that is more powerful.
One shocking IT scenario that we regularly encounter is expensive computer hardware plugged into inexpensive power strips. Power strips are adequate if you need a few extra outlets for your kitchen appliances, but if you want to protect the computer hardware that is mission critical to your business, like servers and NAS devices, then you will need a solution that is more powerful.
 Every enterprise, whether it is a successful one or not, has to deal with its fair share of adversity. One of the most rampant difficulties a business is forced to deal with is the necessary ability to secure prompt payment for the goods and services it provides its customers. For small and medium-sized businesses, or even one-man bands, they likely do not have the deep pockets many larger organizations have. Not being able to timely collect income can make sustaining business operations all but impossible. With remote payment applications that are now available for mobile devices, collecting crucial revenue at a mobile point-of-sale is making collecting that is money easier.
Every enterprise, whether it is a successful one or not, has to deal with its fair share of adversity. One of the most rampant difficulties a business is forced to deal with is the necessary ability to secure prompt payment for the goods and services it provides its customers. For small and medium-sized businesses, or even one-man bands, they likely do not have the deep pockets many larger organizations have. Not being able to timely collect income can make sustaining business operations all but impossible. With remote payment applications that are now available for mobile devices, collecting crucial revenue at a mobile point-of-sale is making collecting that is money easier.
 We understand your desire to upgrade to a new computer, using the latest technology has its advantages. Although, upgrading because your old PC has "worn out" may be an inaccurate assessment. There are many reasons why a computer's performance slows down, but it is doubtful that hardware deterioration is a cause. This is because PC hardware is built to last.
We understand your desire to upgrade to a new computer, using the latest technology has its advantages. Although, upgrading because your old PC has "worn out" may be an inaccurate assessment. There are many reasons why a computer's performance slows down, but it is doubtful that hardware deterioration is a cause. This is because PC hardware is built to last.
 Everybody has a weakness; Superman has Kryptonite, the Wicked Witch of the West had water, and the Death Star had a womprat-sized exhaust port. Character weaknesses make for solid storylines because they drive conflict. Your company has its own set of vulnerabilities that you may not know about, and unlike stories, conflict in business is not a good thing. Here are a few of the lesser known IT weaknesses, and what you can do to resolve them.
Everybody has a weakness; Superman has Kryptonite, the Wicked Witch of the West had water, and the Death Star had a womprat-sized exhaust port. Character weaknesses make for solid storylines because they drive conflict. Your company has its own set of vulnerabilities that you may not know about, and unlike stories, conflict in business is not a good thing. Here are a few of the lesser known IT weaknesses, and what you can do to resolve them.
 With the widespread use of mobile devices in the workplace, more companies are questioning the relevance of their traditional IT infrastructure. Mobile devices take advantage of cloud computing, and every new generation of tablets and smartphones have productivity apps that can accomplish more tasks. Before you switch out your old technology, you will first want to consider the data needs of your business.
With the widespread use of mobile devices in the workplace, more companies are questioning the relevance of their traditional IT infrastructure. Mobile devices take advantage of cloud computing, and every new generation of tablets and smartphones have productivity apps that can accomplish more tasks. Before you switch out your old technology, you will first want to consider the data needs of your business.
 The evolution of Google from a search engine company renting a garage, to one of the largest companies on the planet, is a story that can truly boggle the mind. One cause of Google's growth is their investment in developing new technology. This is the case with the Google Spanner, which is a new technology designed to manage Google's growth.
The evolution of Google from a search engine company renting a garage, to one of the largest companies on the planet, is a story that can truly boggle the mind. One cause of Google's growth is their investment in developing new technology. This is the case with the Google Spanner, which is a new technology designed to manage Google's growth.
 Business growth is a double edged sword. It is great that you are increasing revenue, but you now have to deal with growing pains. These growing pains are often felt with your technology. Is your network cobbled together with random computers and your wires are one big tangle ball? Directive can help relieve these IT growing pains with network mapping.
Business growth is a double edged sword. It is great that you are increasing revenue, but you now have to deal with growing pains. These growing pains are often felt with your technology. Is your network cobbled together with random computers and your wires are one big tangle ball? Directive can help relieve these IT growing pains with network mapping.
 The ramifications of social media have extended well beyond just a tool used to keep in touch with friends. From games, to advertising, to even aiding in the overthrow of Middle Eastern governments, social media has added a new and powerful dynamics to the way people use technology. For better or for worse, social media also adds new and interesting dynamics to the most social part of our lives, our families.
The ramifications of social media have extended well beyond just a tool used to keep in touch with friends. From games, to advertising, to even aiding in the overthrow of Middle Eastern governments, social media has added a new and powerful dynamics to the way people use technology. For better or for worse, social media also adds new and interesting dynamics to the most social part of our lives, our families.
 The majority of today’s more conscientious shoppers will check out the consumer reviews of the device as well as the detail specifications before purchasing a product. Just because it’s pretty and all their friends at school have one, doesn’t always mean that it is the best value for your money. Still, we rarely consider: Do review sites and vendor release notes tell the whole story? Is this device really better because of its price tag or big name brand? There is a widely underused but extremely valuable resource online where customers can gain a little more perspective. This is called the product "teardown”.
The majority of today’s more conscientious shoppers will check out the consumer reviews of the device as well as the detail specifications before purchasing a product. Just because it’s pretty and all their friends at school have one, doesn’t always mean that it is the best value for your money. Still, we rarely consider: Do review sites and vendor release notes tell the whole story? Is this device really better because of its price tag or big name brand? There is a widely underused but extremely valuable resource online where customers can gain a little more perspective. This is called the product "teardown”.